Media file copyright protection method and system
A technology for media file and copyright protection, applied in the field of information security, can solve the problems such as the inability to track the illegal transmission of media files, and the inability to guarantee the duplication of media files, so as to achieve the effect of safeguarding legitimate rights and interests and improving security protection capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
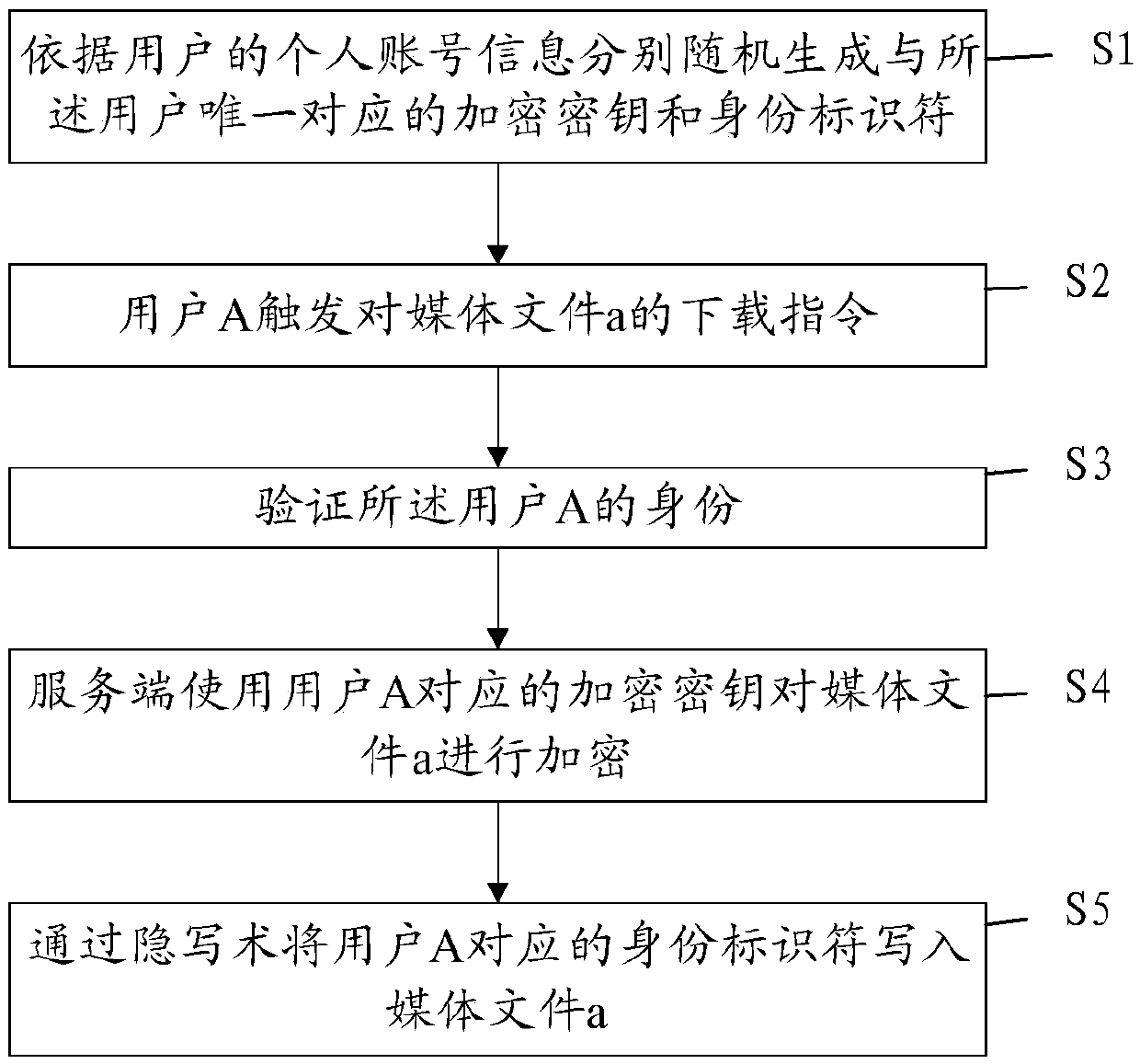
[0086] Please refer to Figure 2-Figure 5 , the present embodiment provides a method for copyright protection of media files, which can effectively prevent copyright-protected media files from being disseminated indiscriminately, ensure that they are circulated in authorized channels, and at the same time accurately locate the source of illegal duplication.
[0087] The method of this embodiment may specifically include the following steps:
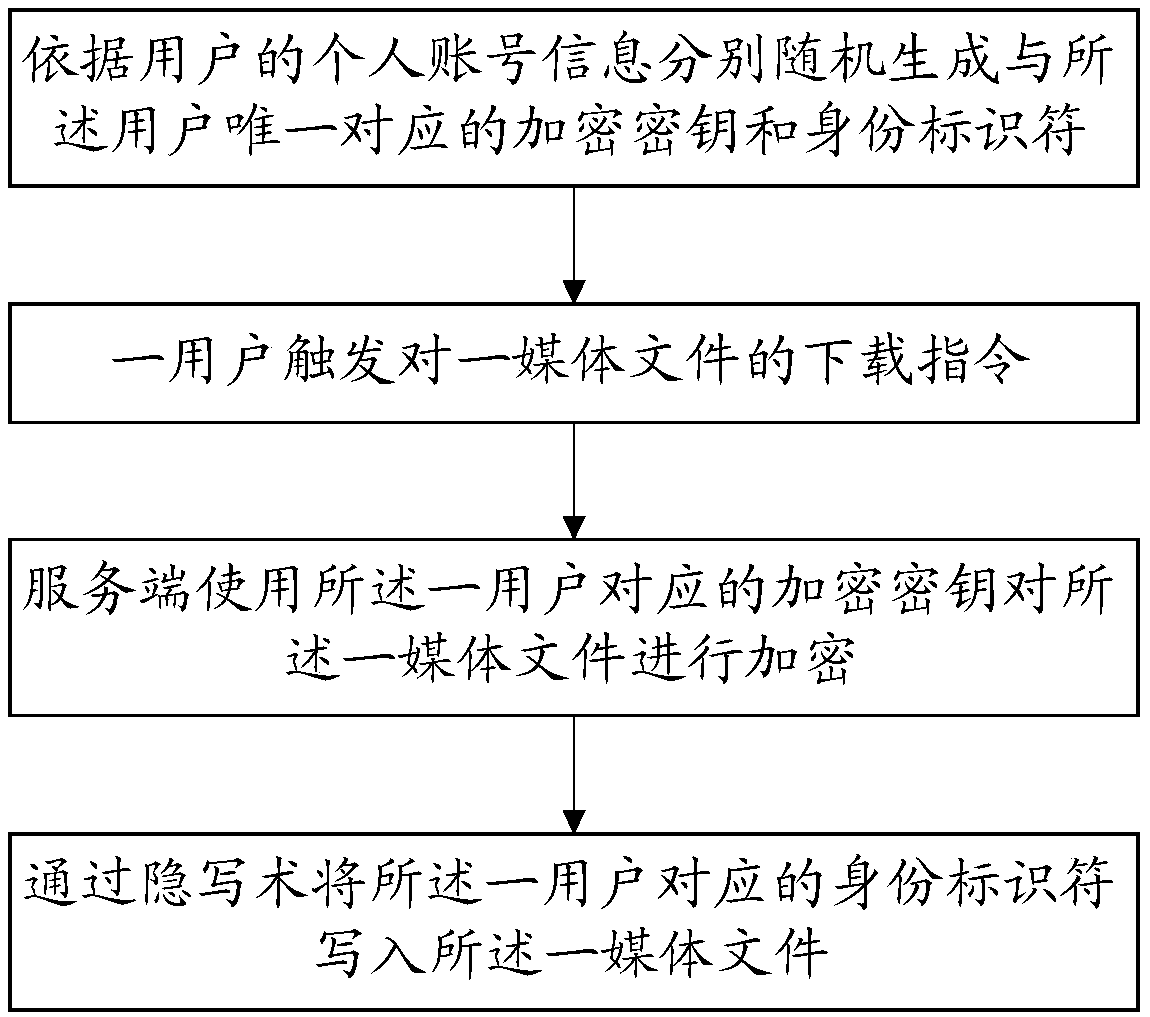
[0088] S1: Randomly generate an encryption key and an identity identifier uniquely corresponding to the user according to the user's personal account information.
[0089] Specifically, when a user applies for registration with the server, after filling in key personal account information, such as a mobile phone number with a unique identifier, the server will randomly generate a uniquely corresponding account number based on the user's personal account information. The encryption key is used for subsequent encryption of media files; in thi
Embodiment 2
[0150] This embodiment corresponds to Embodiment 1, and provides a protection system for media files, including a server and a first program; the first program can implement the following steps when called by a processor at the server:
[0151] Randomly generate an encryption key and an identity identifier uniquely corresponding to the user according to the user's personal account information;
[0152] After receiving a user-triggered download instruction for a media file, encrypting the media file using an encryption key corresponding to the user;
[0153] Writing the identity identifier corresponding to the user into the media file through steganography.
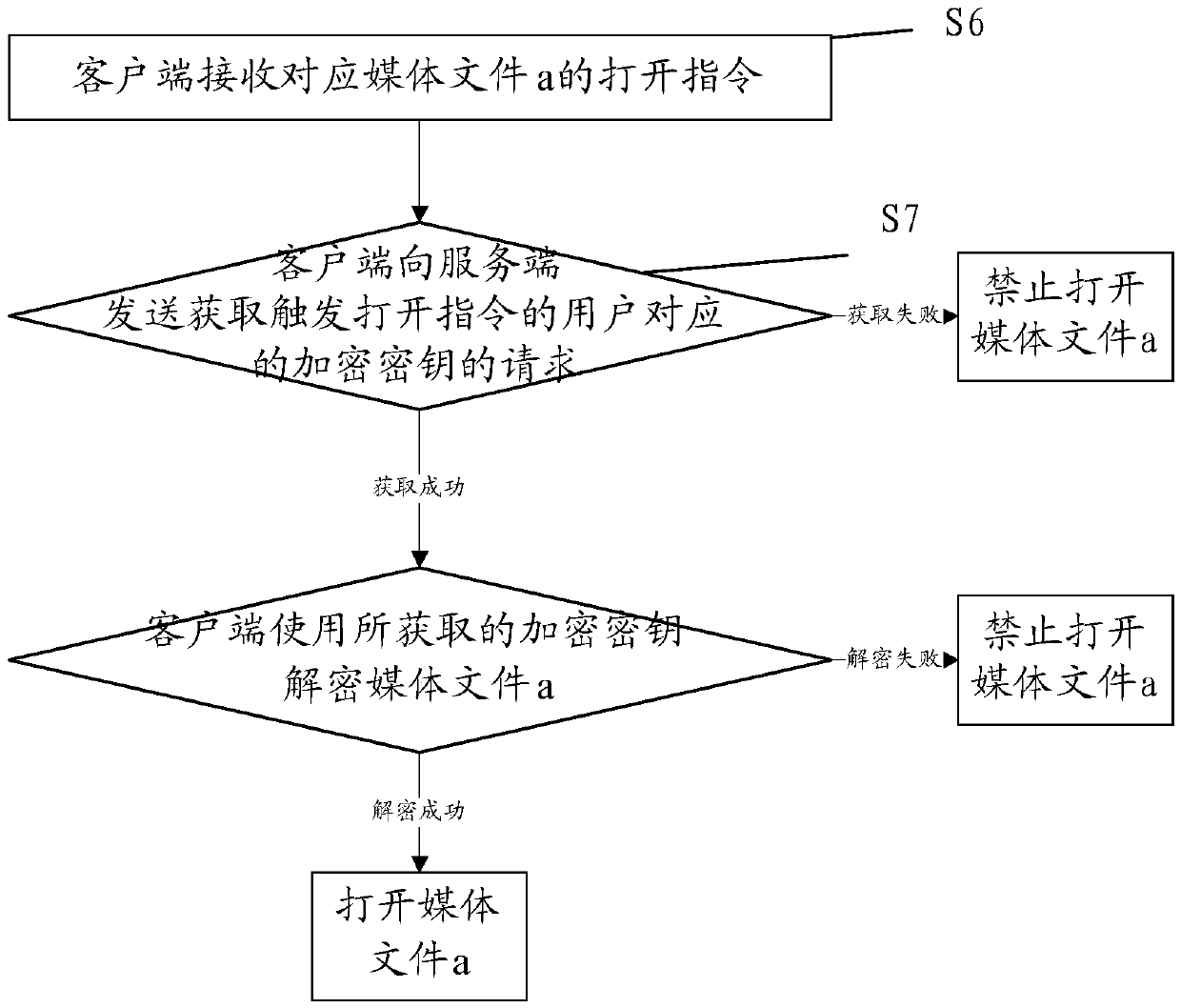
[0154] The protection system also includes a client and a second program, the second program can implement the following steps when called by the processor of the client:
[0155] The client receives an open instruction corresponding to the one media file;
[0156] The client tries to obtain the encryption key corresponding
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap