Safety detection system and method based on log analysis
A security detection and log technology, applied in the field of information security, can solve the problems of poor timeliness, lack of timeliness, and inability to meet the real-time detection and analysis of website threats, so as to improve the protection ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, the following will be described in detail in conjunction with the accompanying drawings and specific embodiments. The following embodiments are used to illustrate the present invention, but not to limit the scope of the present invention.
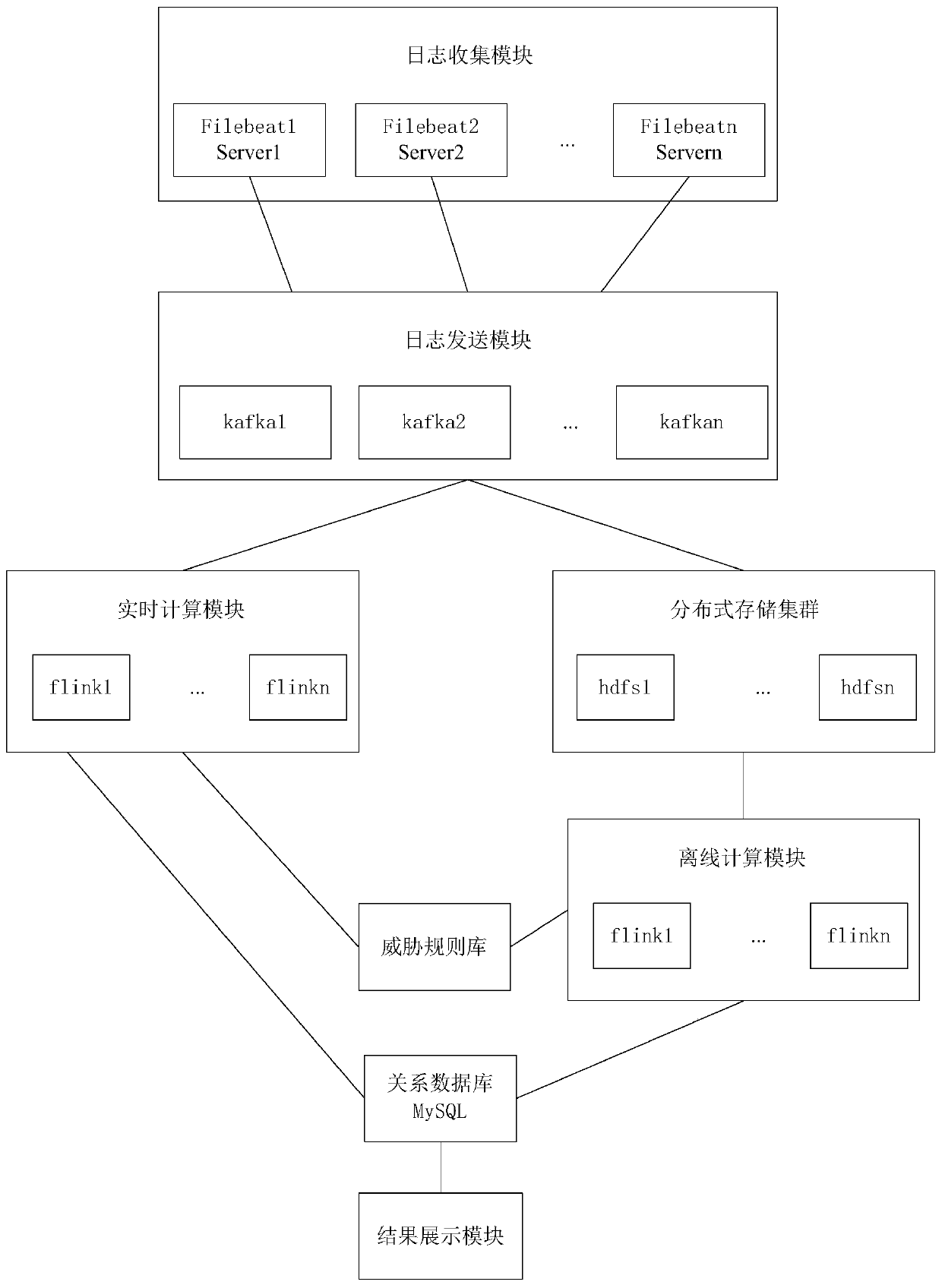
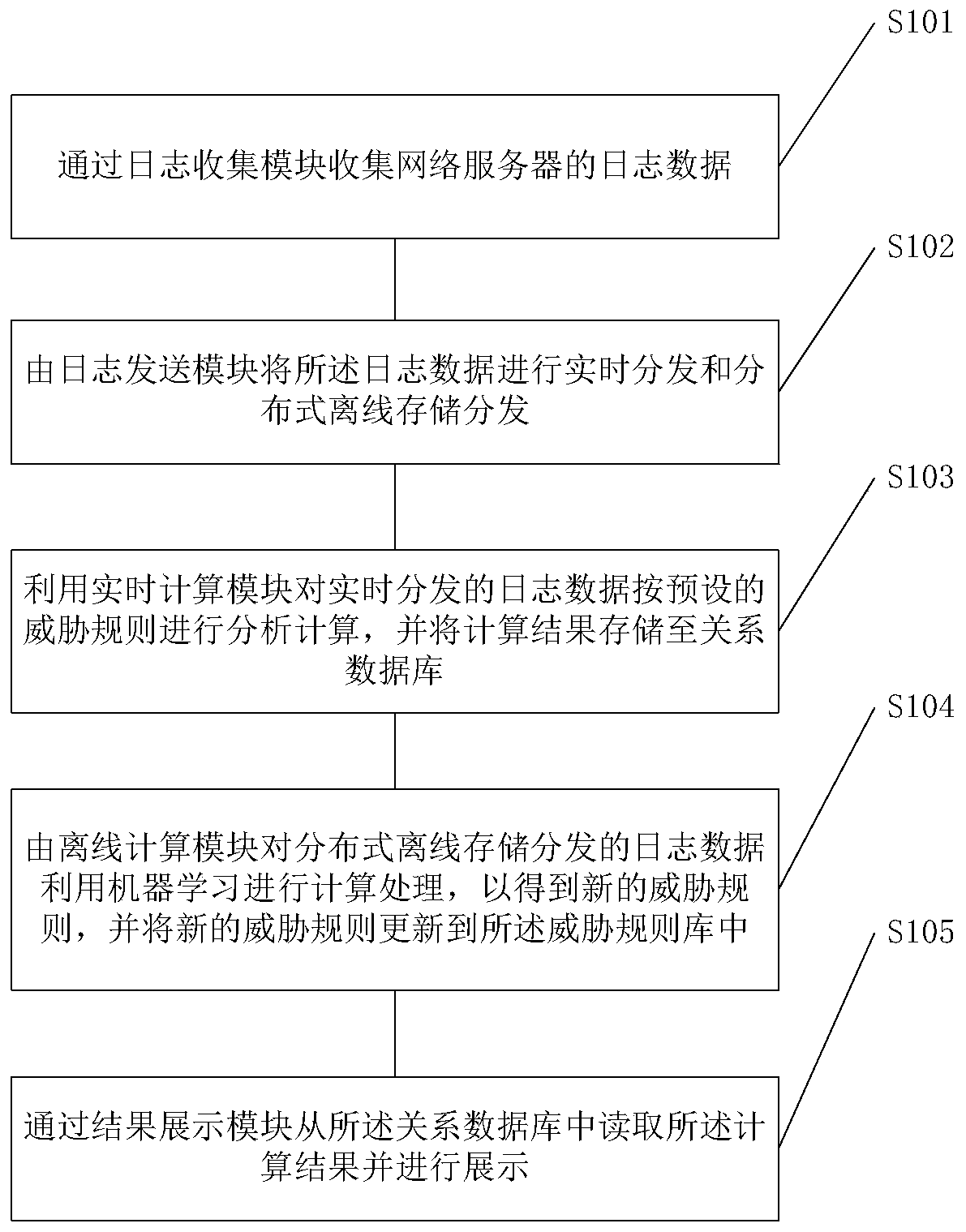
[0039] refer to figure 1 , figure 2 As shown, the embodiment of the present invention provides a security detection system based on log analysis, the system includes:
[0040] The log collection module is used to collect log data of the web server.
[0041] Specifically, in this embodiment, the filebeat plug-in is used to collect log data, and when a change in the log file is detected, the changed data is incrementally collected. Among them, the change of the file refers to the change of the content of the log file. During collection, multiple log data can be collected in parallel from multiple websites at the...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap