Method and network element for providing secure access to a packet data network
network element technology, applied in the field of method and system for providing secure access to a packet data network, can solve the problems of fraudulent users, invisibility registration of impus, and inability to use ipi
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
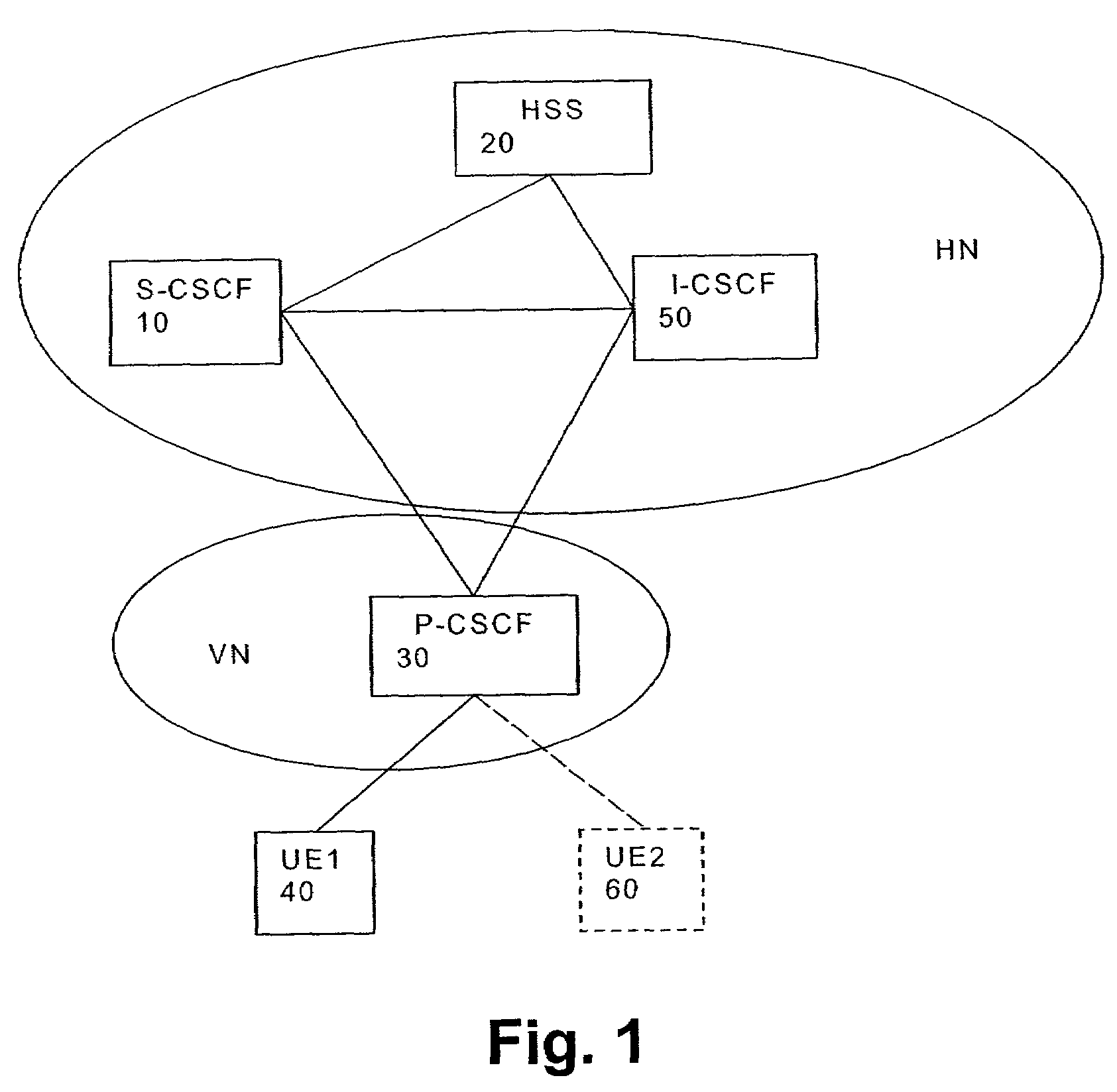
[0037]The preferred embodiment will now be described on the basis of an IMS architecture as shown in FIG. 1.
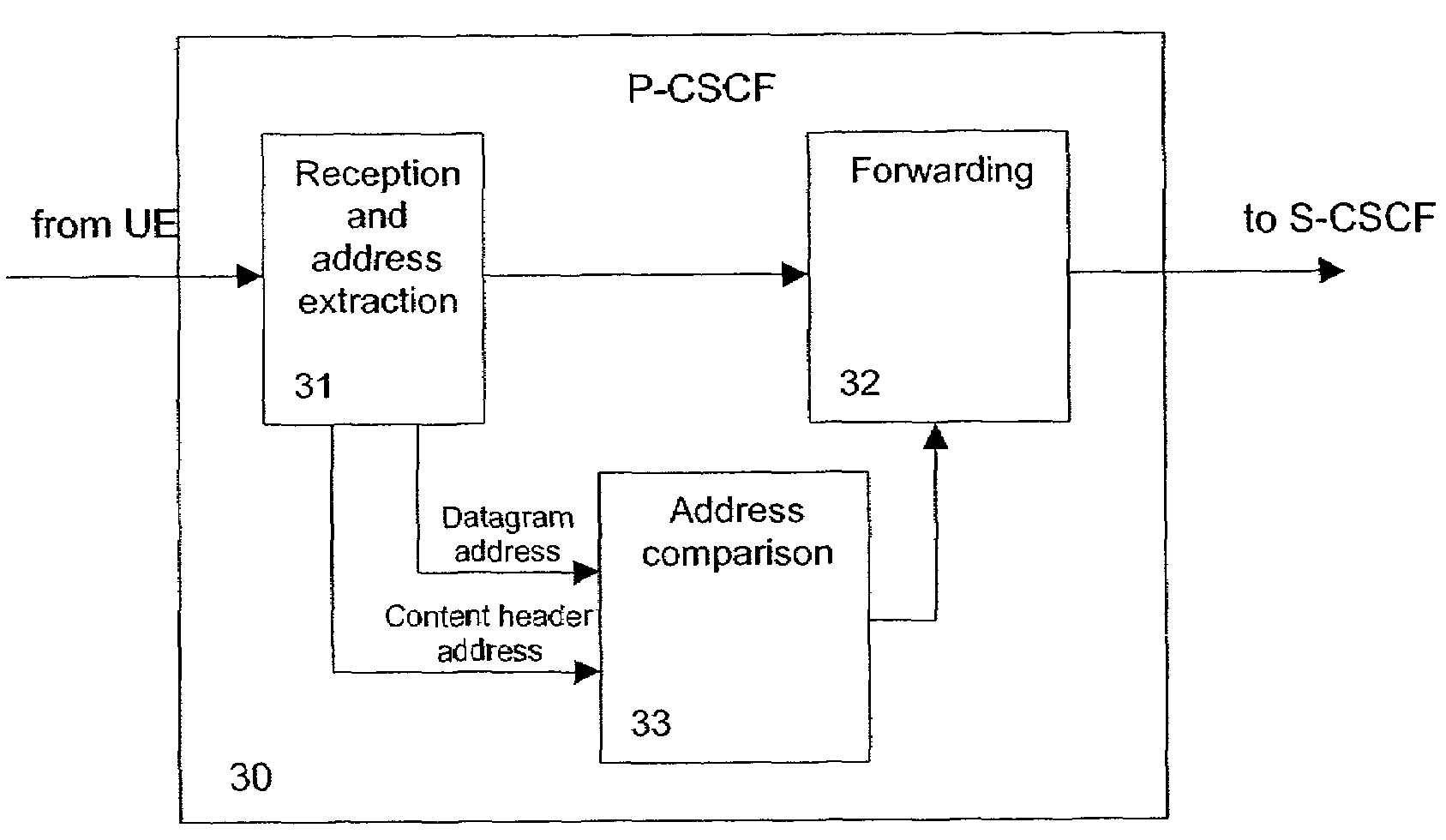
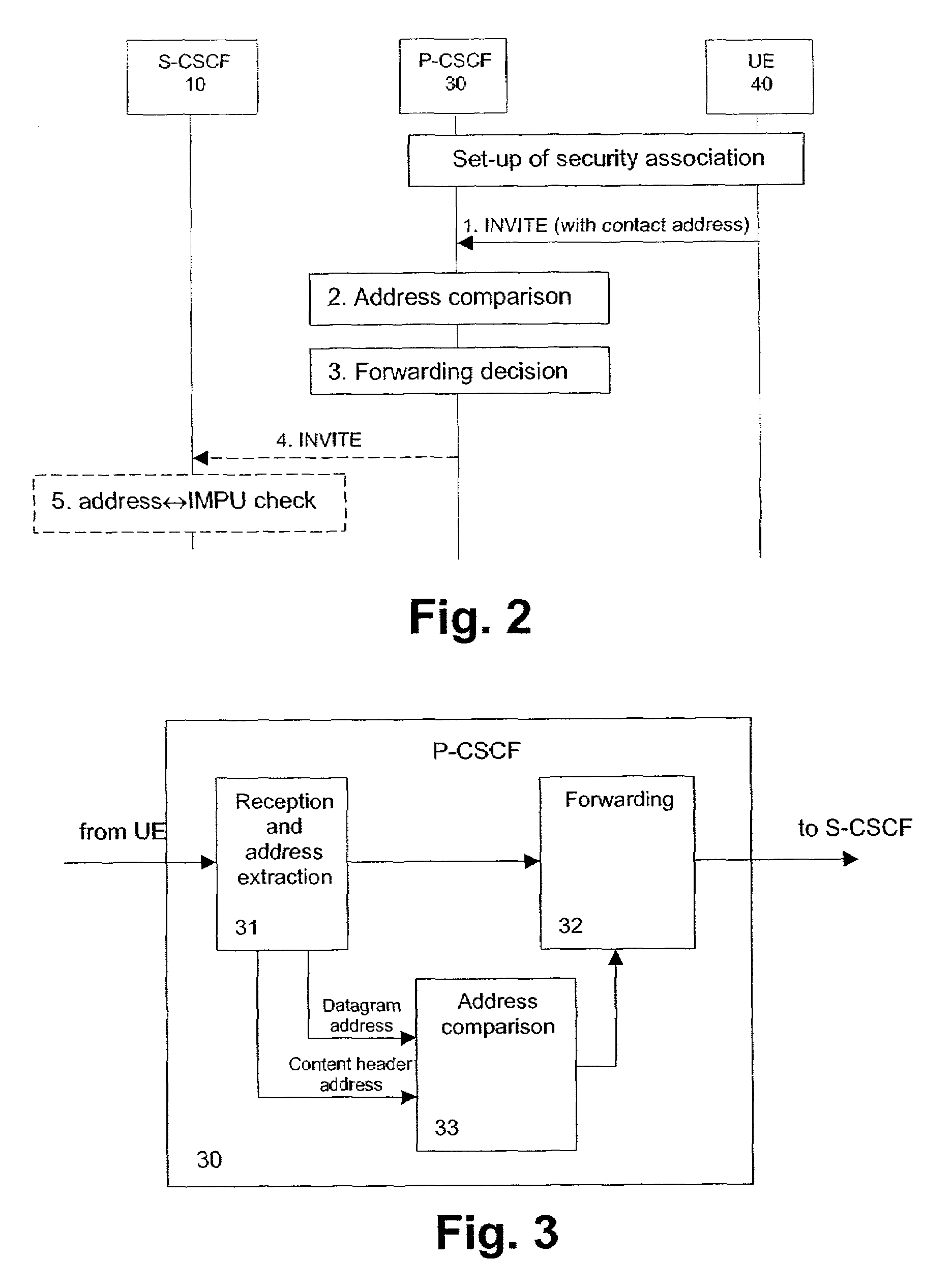
[0038]As already mentioned, a hole for an attacker is provided in the system according to the 3GPP specification TS 33.203. Even if security transmission protocols, such as IP security (IPSec) or a SIP-level security or protection function (SIPSec), are used to protect the SIP signaling between a UA and the P-CSCF 30, an attacker who is also a subscriber in the IMS has a chance to send a SIP request message using the right SA for him and with a public identity (IMPU) which is not allocated to him. This is called a fraudulent user attack, i.e. identity spoofing. According to the preferred embodiments, mechanisms are provided to check whether an IMS subscriber uses only those IMPUs as IP messages, which are allocated to him. In FIG. 1, the UE260 indicated with dotted lines is assumed to perform a fraudulent user attack, using an IMPU of the UE140.
[0039]FIG. 2 shows a message signal
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap