System and method for identifying a phishing website
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
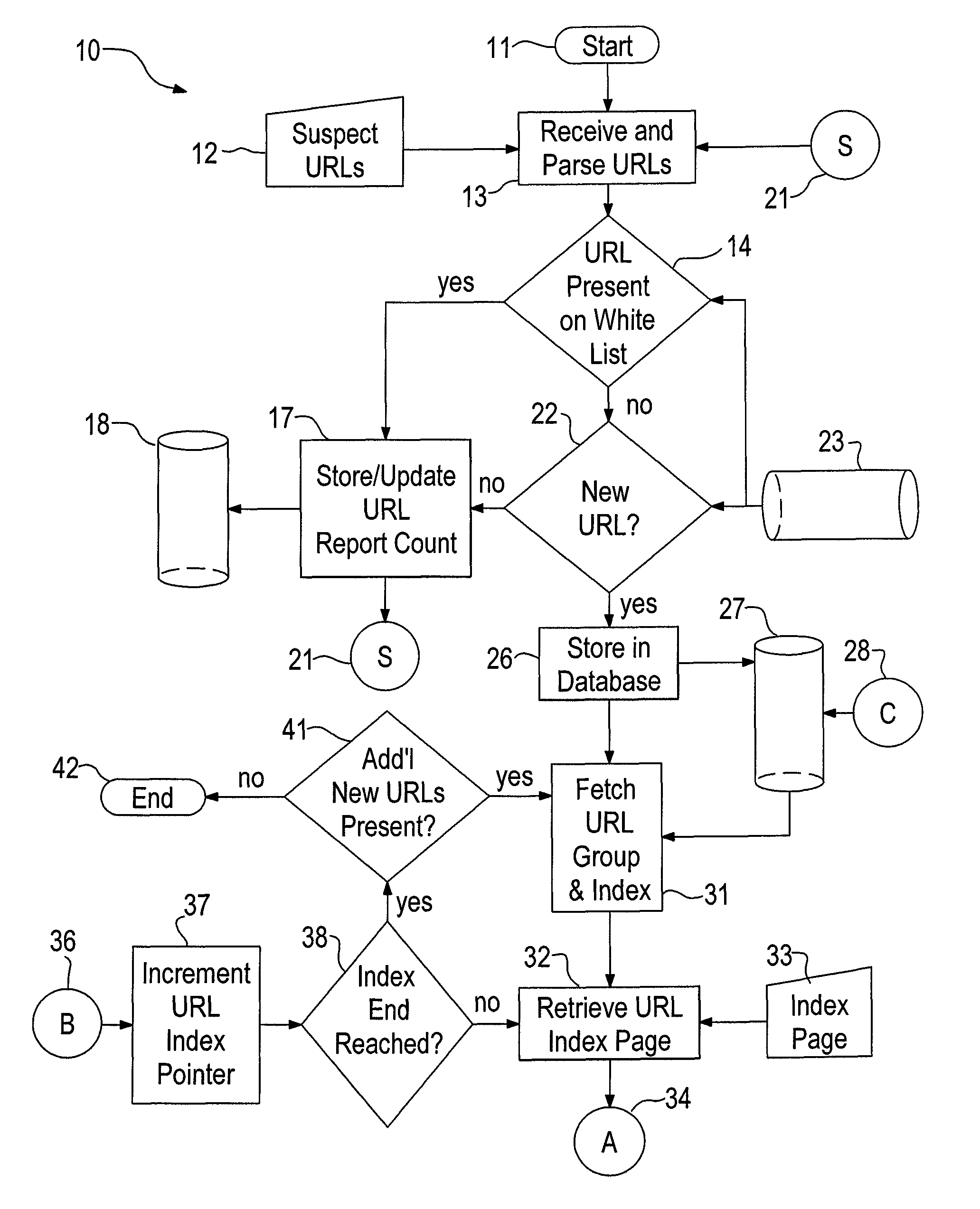
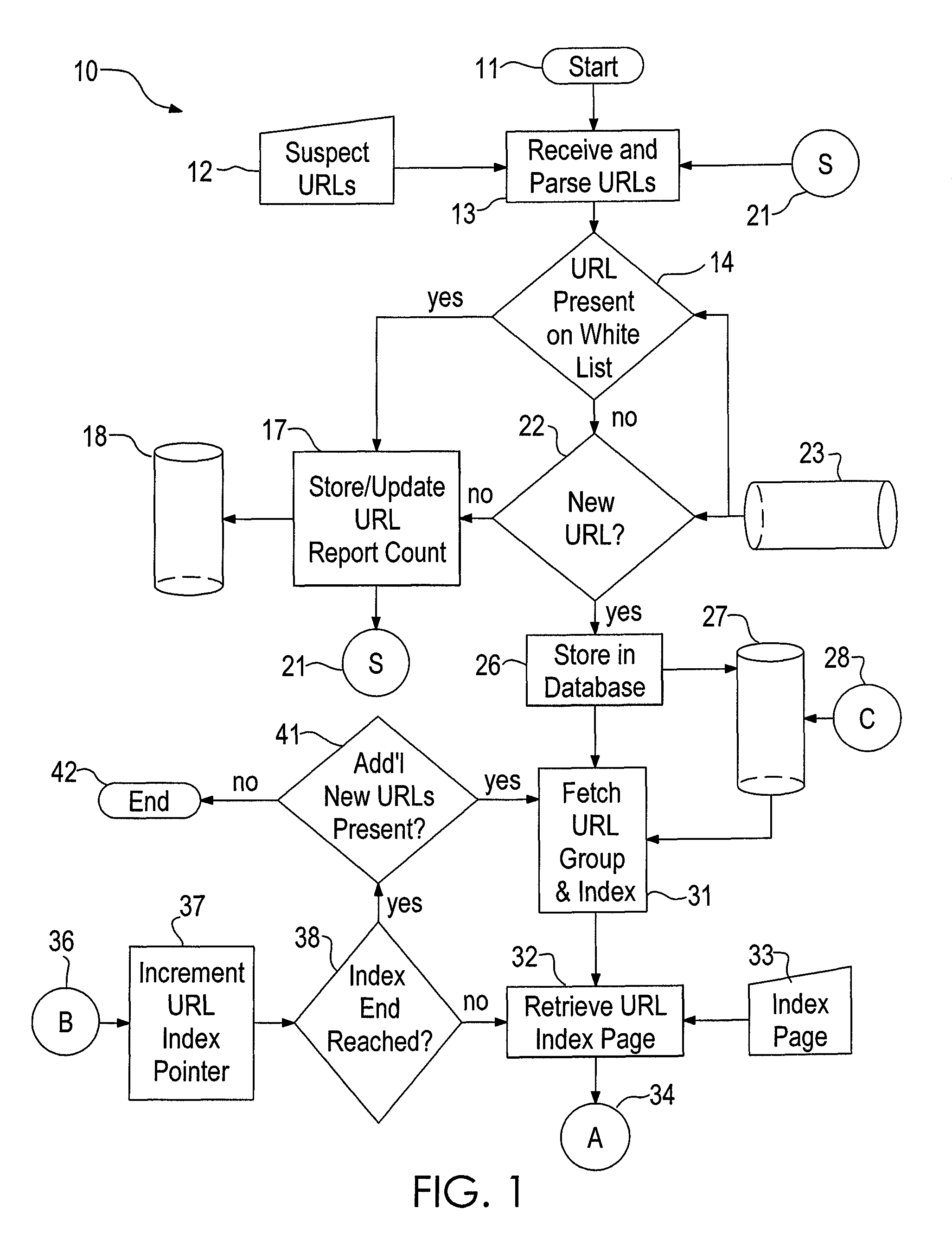
[0017]Referring to FIG. 1, the system 10 is constructed to run on a computer system, such as a computer server, having a modern operating system like Microsoft Windows or a variant of UNIX such as Linux. The present system is currently compiled to run on a Linux OS derivative, Cent OS, offered by Red Hat. Database functionality is provided by PostgreSQL, which is a powerful, open source object-relational database system. PERL is currently used in the system to control communications through the Internet and to parse received e-mails. While the interpretive language PERL is currently used by the inventors, it is anticipated that a compiled language such as C would ultimately implement the features of the system.
[0018]Upon initiation 11 the system 10 receives 13 a string of supplied urls 12 and parses them 13 into a text file having a separate url on each line. The urls 12 are provided by a variety of sources such as an anti-spam company, an anti-phishing company, a “shut-down” company,
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap