Batch resource sharing method for untrusted cloud centers based on exclusive OR operation and chaos
A resource sharing and resource technology, applied in the field of cloud security, can solve problems such as increased difficulty of key management, reduce the possibility of guessing and cracking, and reduce the difficulty of key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
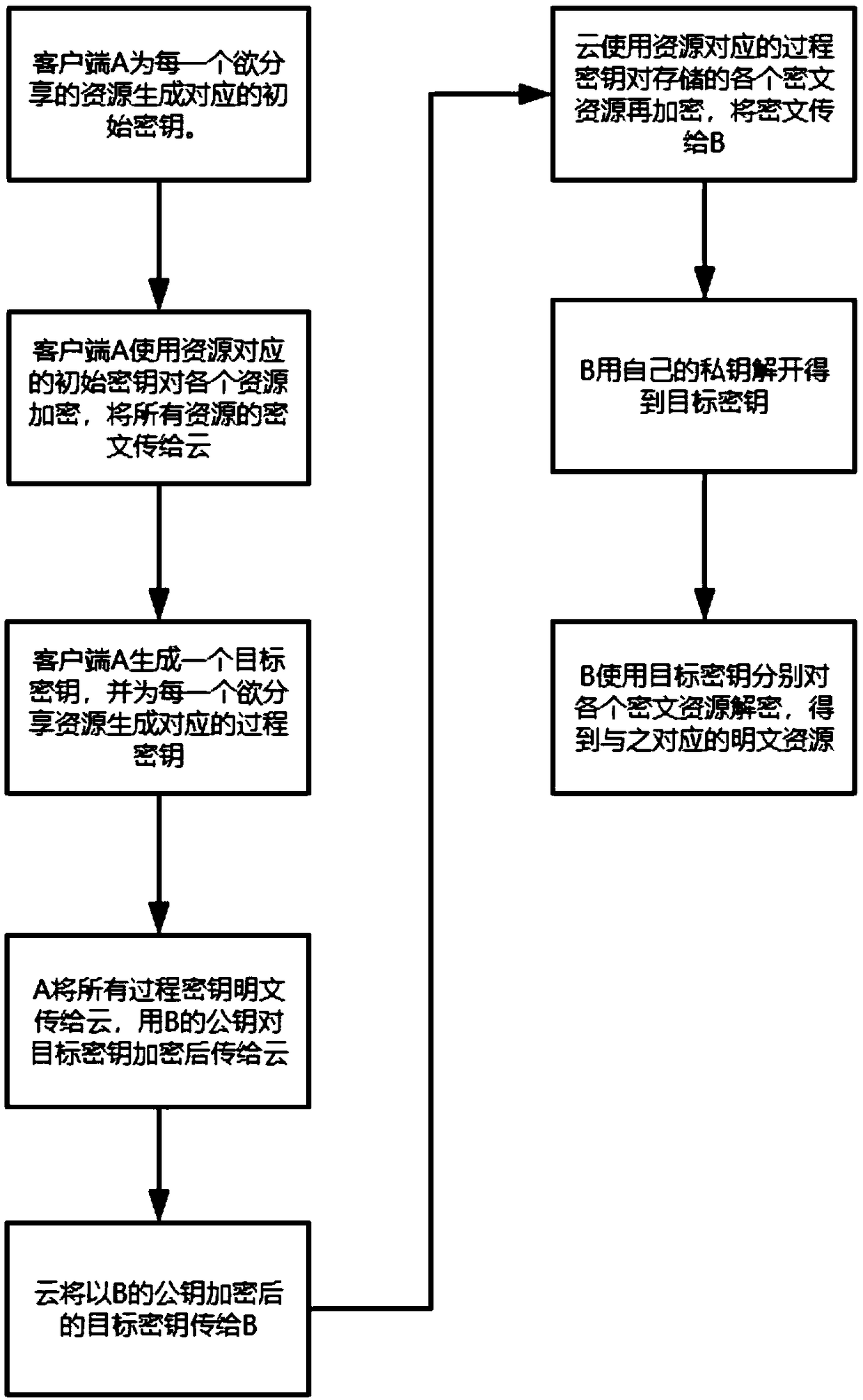
[0044] Client A shares batch resources with client B by using an algorithm based on XOR encryption and chaos theory. The batch resources are the string "ab" and the string "cd" respectively.
[0045] A method for sharing resources in batches in an untrustworthy cloud center based on XOR operation and chaos, comprising the following steps:
[0046] 1. Client A encrypts batch resources [S 1 ,S 2 ], and upload to the cloud center
[0047] Client A maps the shared string resource to a numeric array S 1 = {0x61,0x62}, S 2 ={0x63,0x64}, the mapping method is to take the ascii code of the string and convert it to hexadecimal;
[0048] 1.1: Client A is the batch resource [S 1 ,S 2 ] to generate the corresponding initial key as [k 11 ,k 12 ],k 11 =(M=0x8b3c, u=3.5699457, x=0.5, n=16), k 12=(M=0x497f, u=3.5699457, x=0.5, n=16), where u, x, n are random numbers, the value range of u is 3.5699456=1, M is a randomly generated bit string of n bits;
[0049] 1.2 Client A calls the ch
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap