A method and system for implementing secure billing in peer-to-peer network
A security, charging point technology, applied in the field of network and communication, can solve the security defects of the billing system, no key system, heavy system burden, etc., to reduce the number of network message interactions, simplify key generation and management Steps, the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0107] Example 1
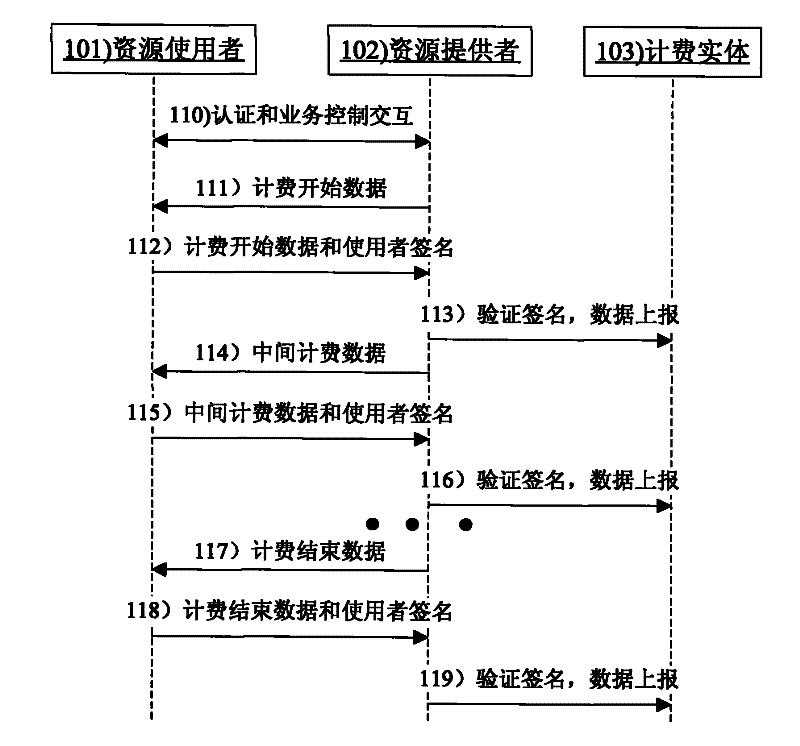
[0108] The implementation process of a secure charging method of the present invention is as follows: Figure 4 Shown. Specific steps are as follows:
[0109] 401) The resource user sends a request to the service control entity to request the use of a certain resource. This resource can be provided by other peer nodes. The request contains basic information such as the type, content, and service quality of the business.
[0110] 402) The business control entity selects resource provider A to provide services for this business. The business control entity allocates a business identifier for this business to identify this business. At the same time, the service control entity generates a service encryption feature code. The service encryption feature code can be randomly generated or generated by encryption of service-related information. After generating the service encryption feature code for this service, the service control entity generates the public part of t
Example Embodiment
[0125] Example 2
[0126] The implementation process of another charging method of the present invention is as follows: Figure 5 Shown. Specific steps are as follows:
[0127] 501) The resource user sends a request to the service control entity to request the use of a certain resource. This resource can be provided by other peer nodes. The request contains basic information such as the type, content, and service quality of the business.
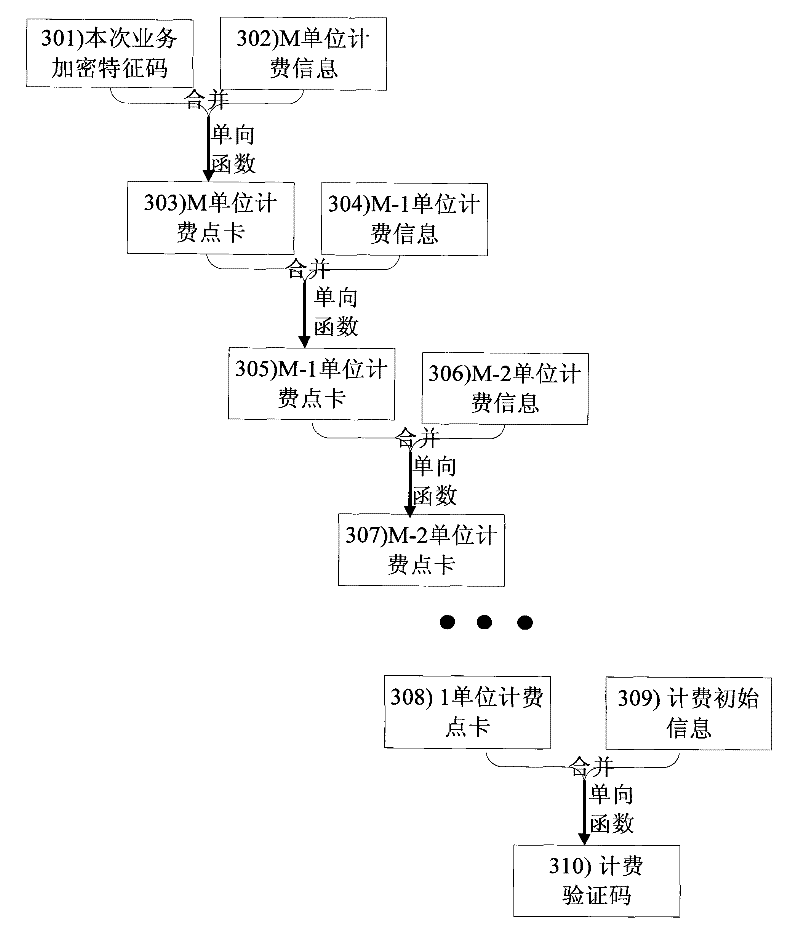
[0128] 502) The business control entity selects resource provider A to provide services for this business. The business control entity allocates a business identifier for this business to identify this business. At the same time, the service control entity generates multiple common parts of charging information. The common parts of multiple billing information can be targeted at different service qualities or provide longer billing time. For example, when the maximum billing duration of a single set of billing point cards is 60 minutes, four bil
Example Embodiment
[0135] Example 3
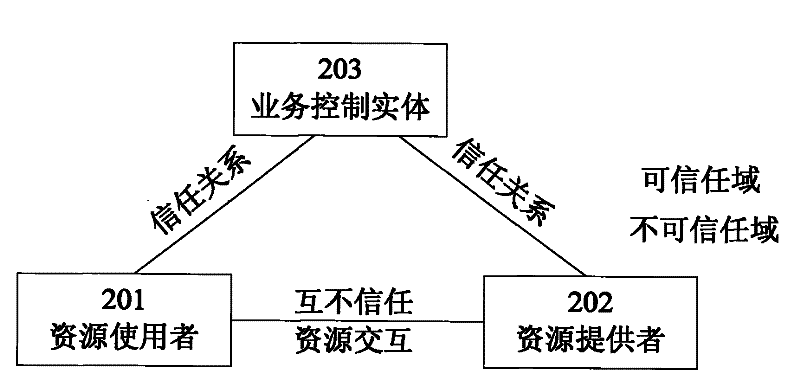
[0136] The invention can support the situation that multiple resource users use the same resource. For example, resource provider A provides data relay functions for two resource users B and C. Specific steps are as follows:
[0137] 601) The resource user B initiates a request to the service control entity, requesting to connect to the resource user C through the relay service.
[0138] 602) The service control entity selects resource provider A to perform this relay service. The business control entity allocates a business identifier for this business to identify this business. At the same time, the service control entity generates a service encryption feature code and related charging point card and charging verification code for resource users B and C, respectively.
[0139] The service control entity sends a message to the resource provider A to request resource reservation. The request message contains the public part of service charging information, the char
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap