GSM network-based access control system and access control method
A technology of GSM network and access control system, applied in the field of access control system of wireless data communication mode, can solve the problem of unmanageable access control system, and achieve the effect of convenient management and maintenance, simple operation and convenient operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
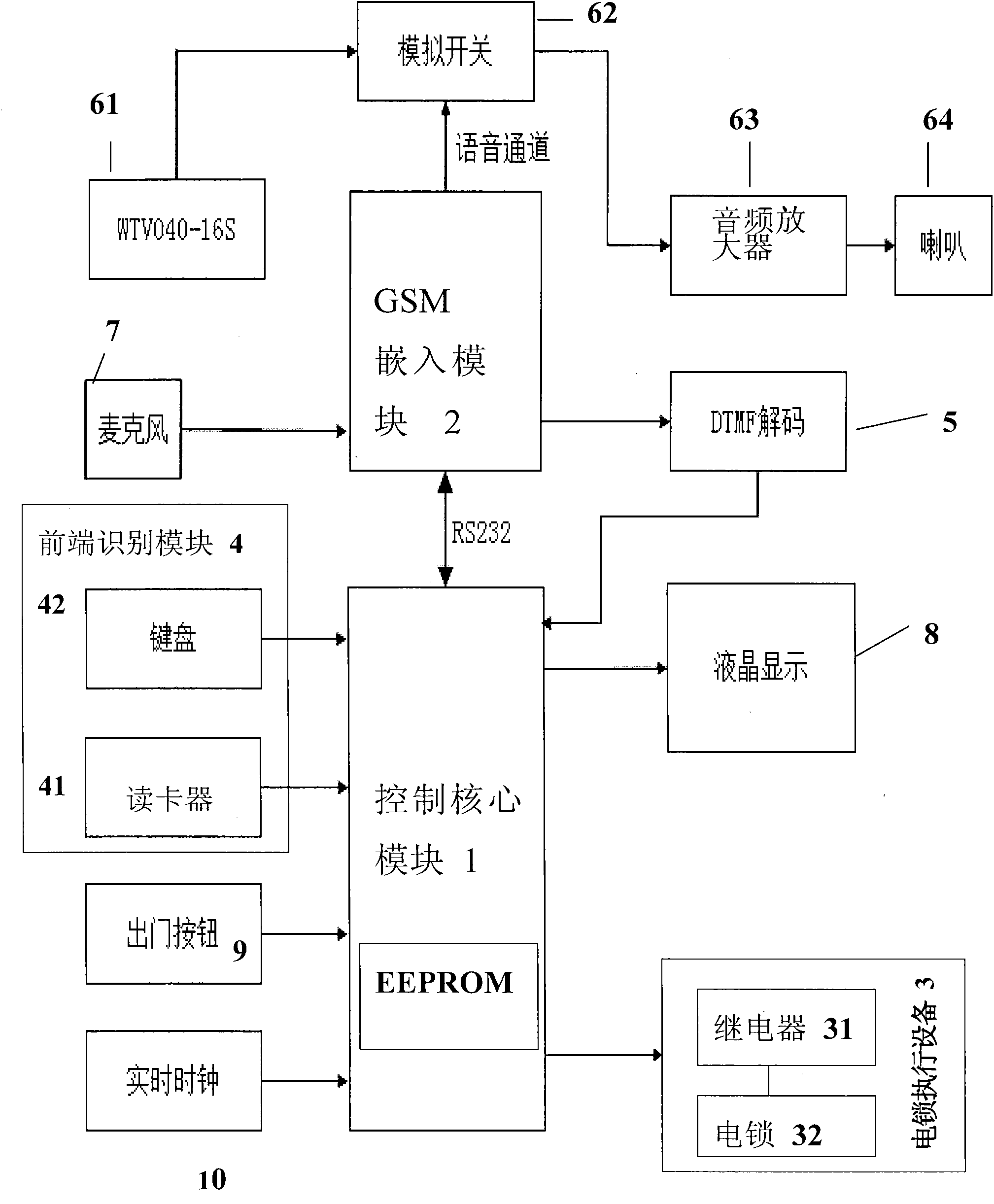
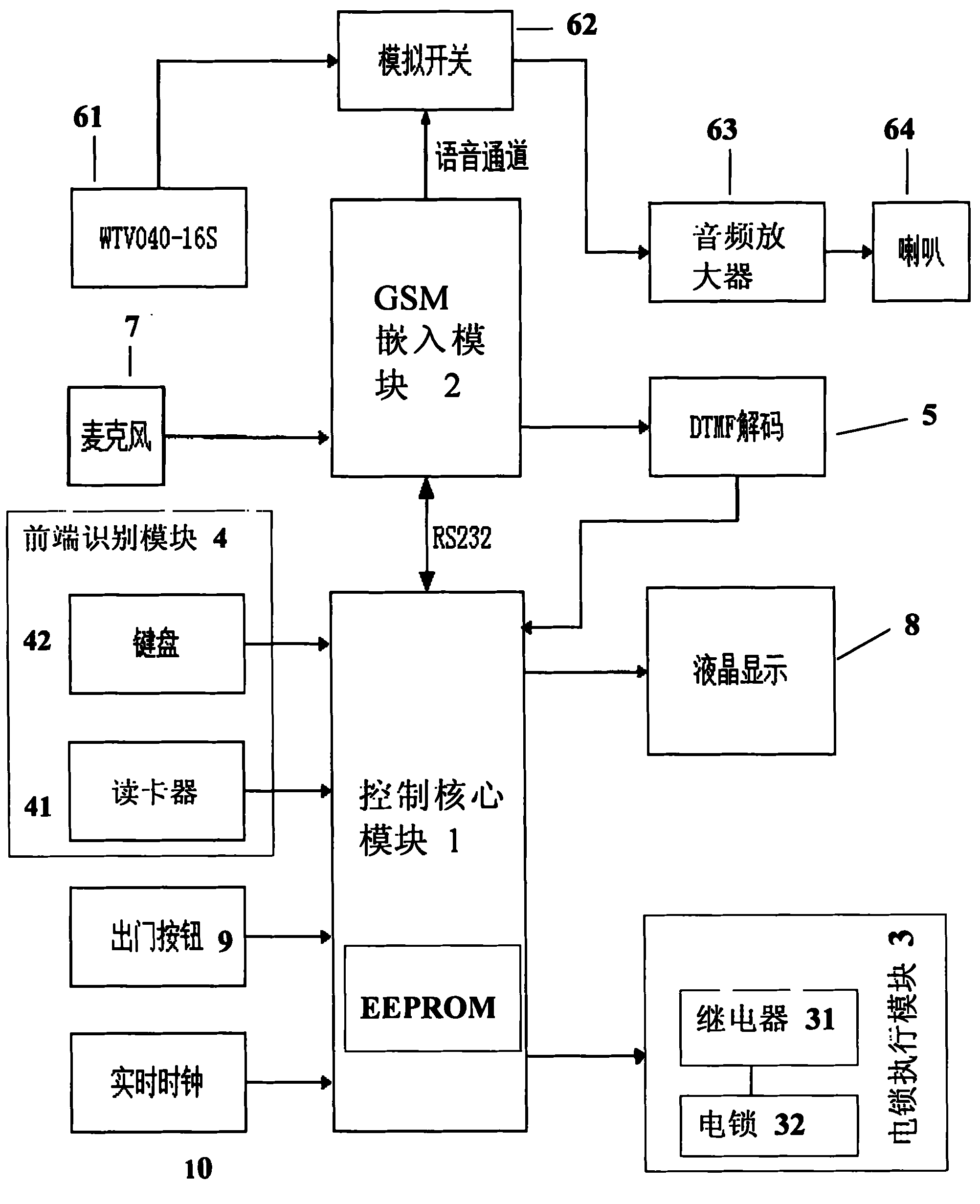
[0035] Implementation method for registered users (a registered user refers to a user who pre-stores the user's identification data in the core control module.)
[0036] When the user uses the password to open the door, he only needs to input the password in a certain format through the button on the keyboard 42 of the front-end identification module 4, and after the control core module 1 receives the password, compare it with the password set by the user pre-stored in the internal EEPROM And judgment, if consistent, core control module 1 sends the door-opening instruction, and the on-off of control relay 31 is to complete the door-opening action;
[0037] When the user adopts the method of swiping the card to open the door, for example, a 125K ID card is used. After the user swipes the card, the card reader 41 of the front-end identification module 4 reads the card number information, and the control core module 1 receives the ID card number. If the card number set by the user i
Embodiment 2
[0042] Implementation method for non-registered users (non-registered users refer to users who have not pre-stored user identification data in the core control module, such as visitors.)
[0043] When the visitor needs to enter and operate the button on the keyboard 42 of the front-end identification module 4 (for example, the room number), the control core module 1 sends the key information to the user's fixed phone or mobile phone through the GSM embedding module 2. It can be a landline phone call, a mobile phone call, or a mobile phone text message to inform the user (proprietor) that "there is a visitor". The user (proprietor) who receives this information can operate the landline phone button or mobile phone button in the call state, or Voice (acquisition of voice with microphone 7) or mobile phone text messages send the "door open" command to the control core module 1 through the GSM embedded module 2, and then the control core module 1 controls the electric lock execution m
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap