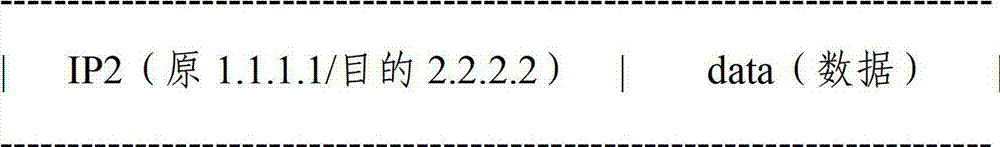Method for carrying out encryption and decryption by using IPSec security association
An alliance and security technology, applied in the field of communication, can solve problems such as confusion and response information that multiple devices do not correspond to
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] The present invention proposes a method for encrypting and decrypting using an IPSec security association, characterized in that at least one local device sends a message to a peer device, and the method includes:
[0027] A. The local device sends a message to the first firewall at the local end;
[0028] B, the first firewall receives the message, uses the IPSec security association to encrypt the message, and sends the encrypted message to the second firewall at the opposite end;
[0029] C. After the second firewall receives the encrypted message, it searches for the IPSec security association according to the security protocol type of the encrypted message and the security parameter index SPI, and decrypts the encrypted message through the found IPSec security association to obtain the decrypted message. arts;
[0030] D. The second firewall creates a mapping relationship table, and sends the decrypted message to the peer device.
Embodiment 2
[0032] This embodiment includes all the content of Embodiment 1. In addition, the message in step A is further limited to include: the address of the local device and the address of the peer device.
[0033] The encrypted message in step B includes: the address of the first firewall and the address of the second firewall. The first firewall encrypts the message into an encapsulating security payload (Encapsulating Security Payload, ESP) / authentication header (Authentication Header, AH) message.
[0034] The decrypted message in step C includes: the address of the local device and the address of the opposite device. When the second firewall receives the ESP / AH message, it searches for the IPSec SA (IPsec Security Association) on the server according to the security protocol type (AH protocol or ESP protocol) and the security parameter index of the message. After finding it, it uses the IPSec SA to Decrypt the encrypted message and send it to the peer device.
[0035] The map
Embodiment 3
[0043] This embodiment uses a specific IP address to more specifically describe a method for encrypting and decrypting using an IPSec security association. The specific examples are as follows:
[0044] Pc1-------------first firewall------------second firewall------------Pc2
[0045] The client Pc1 sends the message to the client Pc2, wherein the message passes through the first firewall (Firewall, fw) and the second firewall.
[0046] The local device IP2 address 1.1.1.1 of PC1 sends a message to the peer device IP2 address 2.2.2.2 of PC2.
[0047] At this time, the message structure is:
[0048]
[0049] When passing through the first firewall, it needs to be encrypted into an ESP packet through IPSec SA. The IP1 address of the first firewall is 192.168.1.1 and the IP1 address of the second firewall is 192.168.1.2
[0050] The encrypted message structure of the first firewall is as follows:
[0051]
[0052] After the second firewall receives it, it searches for the IP
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap