Server fingerprint mimicry and sensitive information mimicry method based on WEB security gateway
A sensitive information and security gateway technology, applied in the field of computer network security, can solve problems such as lack of active response methods and powerlessness, and achieve the effects of good scalability, leakage prevention, and flexible configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0036] Hereinafter, the present invention will be described in detail based on the drawings, and the purpose and effects of the present invention will become more apparent.
[0037] The present invention is a method for server fingerprint mimicry and sensitive information mimicry based on WEB security gateway, including the following steps:
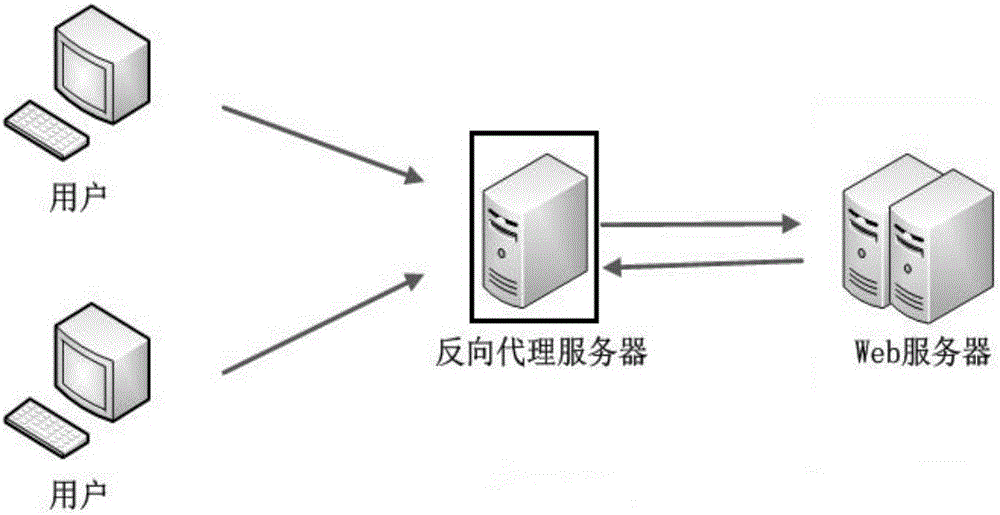
[0038] Step 1: Set up a reverse proxy server between the real web server and the user. The reverse proxy server is implemented based on Nginx. Realize the setting of forwarding and routing rules on the reverse proxy server, and then the message transfer between the user and the web server is processed and forwarded by the reverse proxy server, and the reverse proxy server is transparent to the user and the server; network topology Picture attached figure 1 ;
[0039] Step 2: Configure the mimic security gateway module on the reverse proxy server, including the fingerprint information mimic module of the Web server and the sensitive information mim
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap