Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5 results about "Access control list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An access-control list (ACL), with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject and an operation. For instance, if a file object has an ACL that contains (Alice: read,write; Bob: read), this would give Alice permission to read and write the file and Bob to only read it.
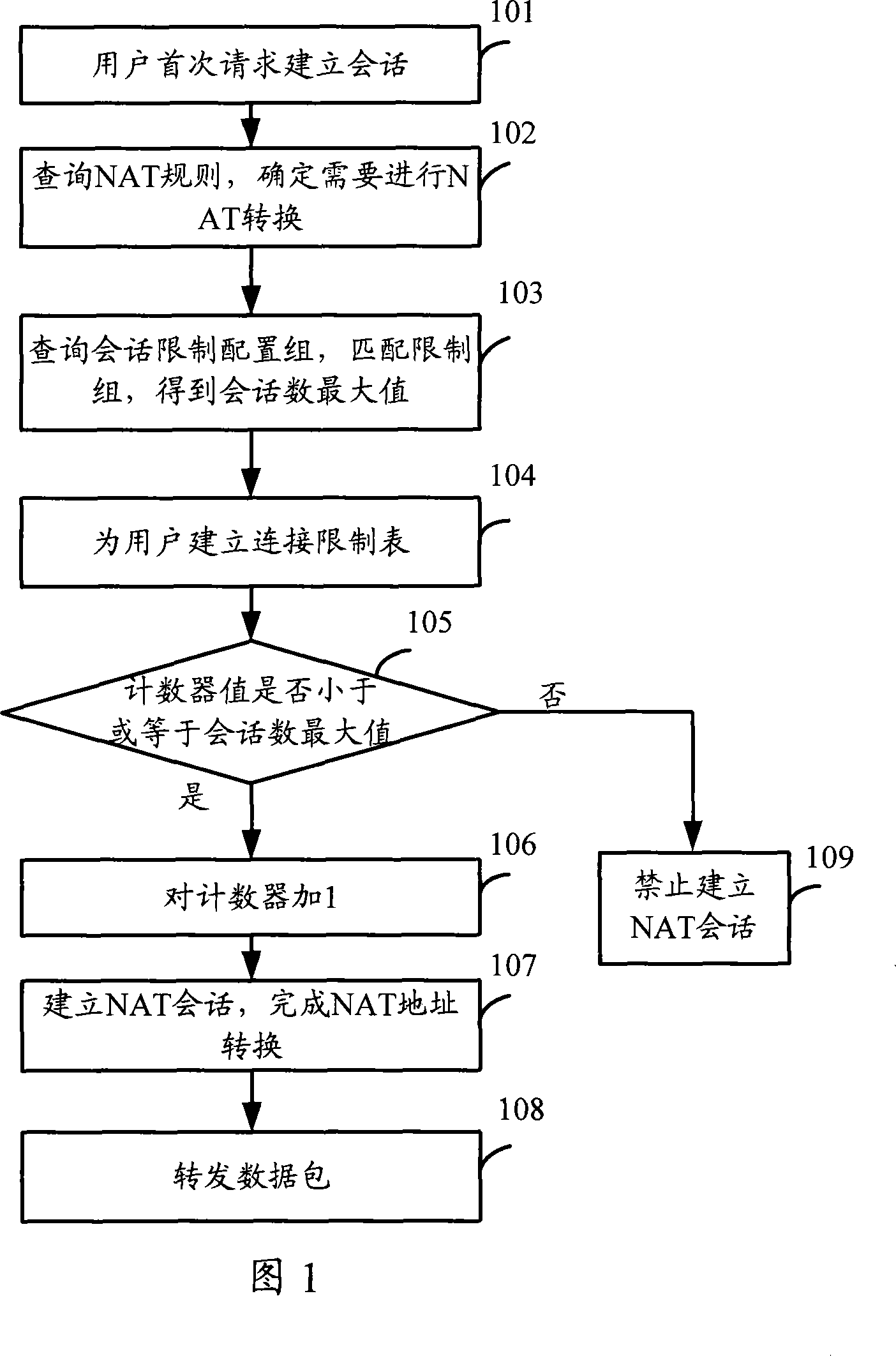
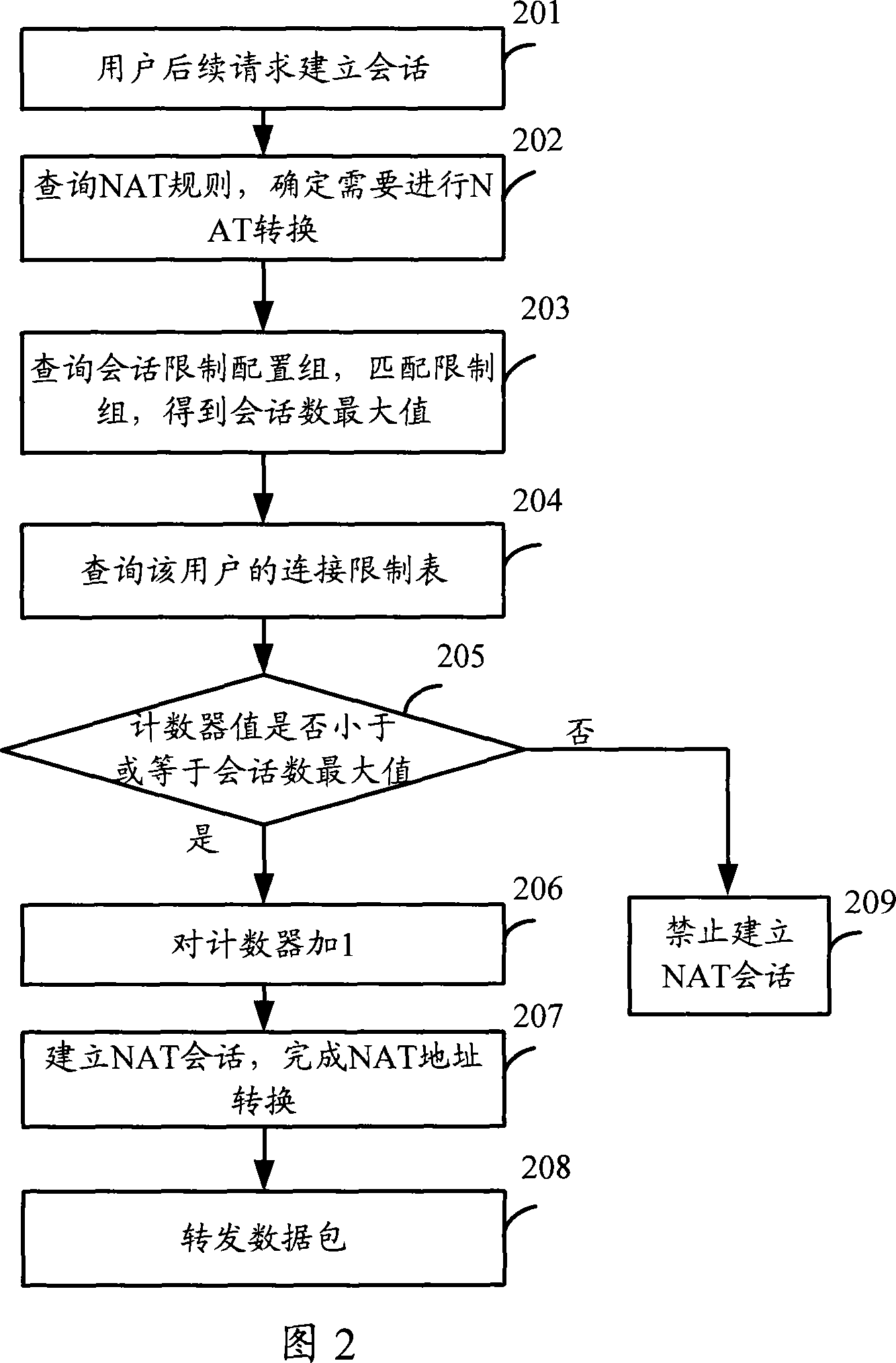
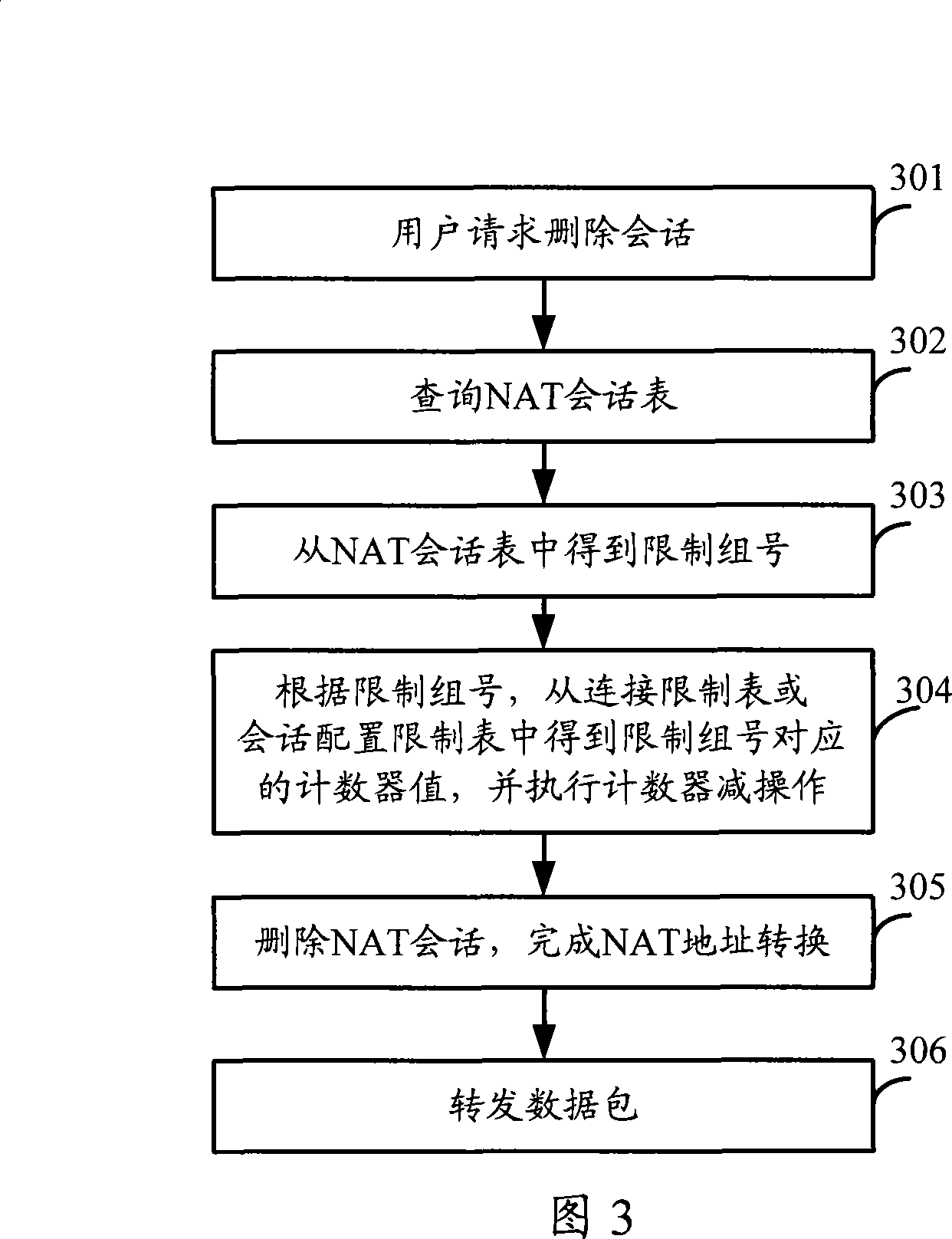
Method and apparatus for limiting session number
ActiveCN101083665AAvoid the problem of not being able to proceed with the rest of the applicationReduce the impactData switching detailsComputer scienceOperating system
Owner:北京华三通信技术有限公司
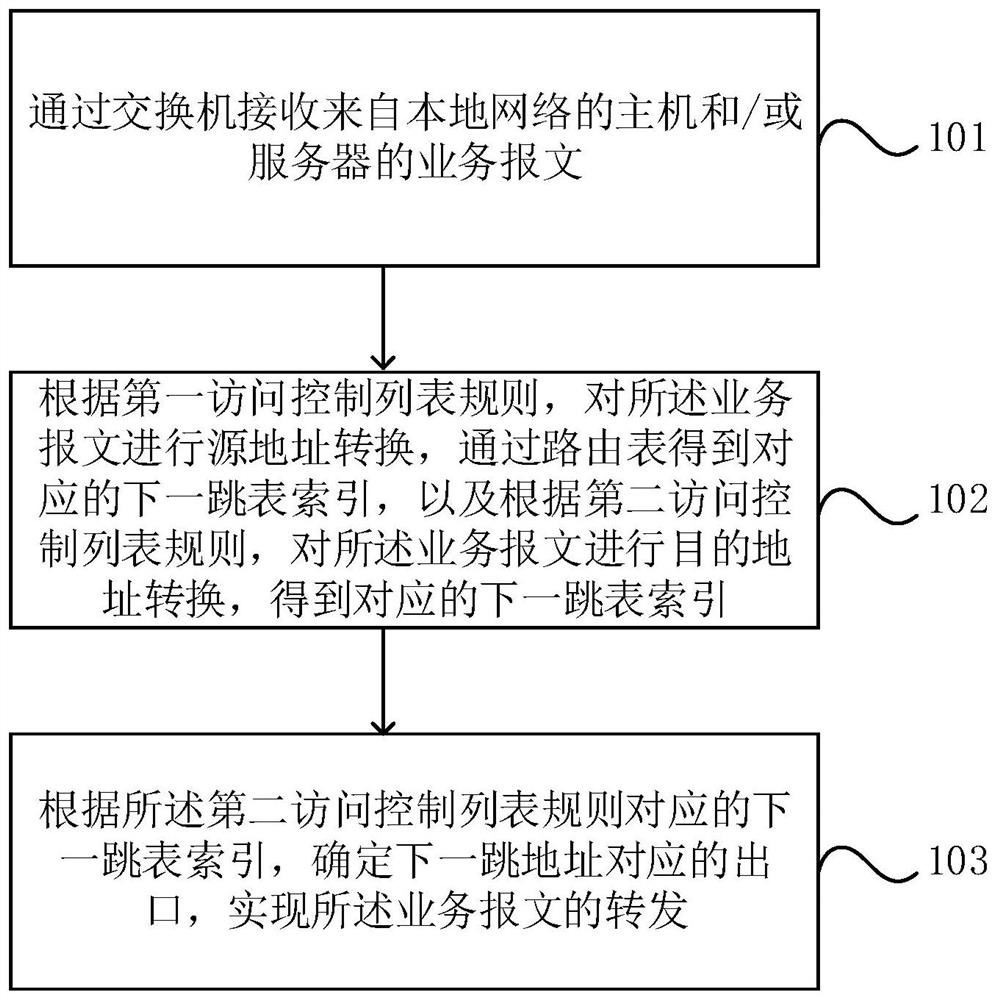
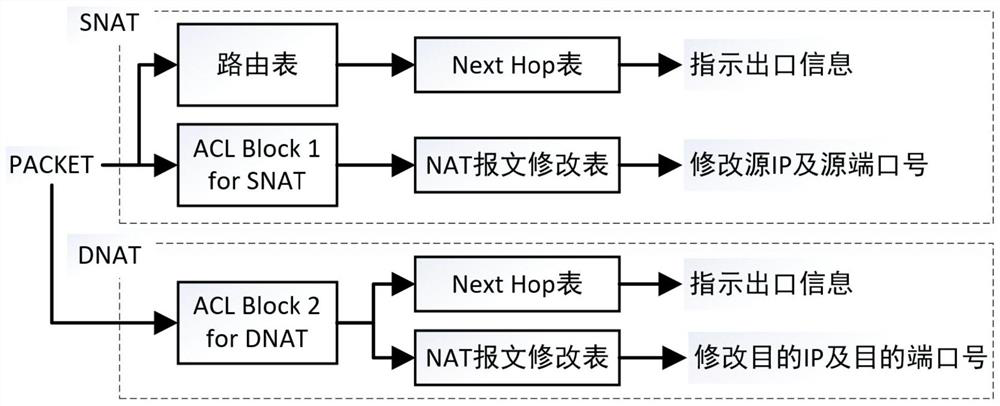
ACL (Access Control List) issuing method and equipment
ActiveCN104486299ASave resourcesReduce the burden onNetworks interconnectionHigh level techniquesVirtual switchAccess control list
The invention discloses an ACL (Access Control List) issuing method and equipment. The method comprises the following steps that an access device acquires an ACL corresponding to each user class identify issued on an upper connecting port; the access device receives a VDP (Vertical Data Processing) association request message from a physics server; a user class identify corresponding to a VM (Virtual Machine) is carried in the VDP association request message; the access device generates a VSI (Virtual Switch Interface) for the VM, and records a corresponding relation between the user class identify corresponding to the VM and the VSI corresponding to the VM in a preset information association table; the access device selects the ACL corresponding to the user class identify corresponding to the VM from the ACL issued on the upper connecting port, and confirms the selected ACL as the ACL corresponding to the VSI corresponding to the VM. According to the embodiment of the invention, the quantity of the ACL issued on the access device can be effectively reduced, the ACL resource is saved, the load of the access device is reduced, and the failure of ACL issuing is avoided.
Owner:NEW H3C TECH CO LTD
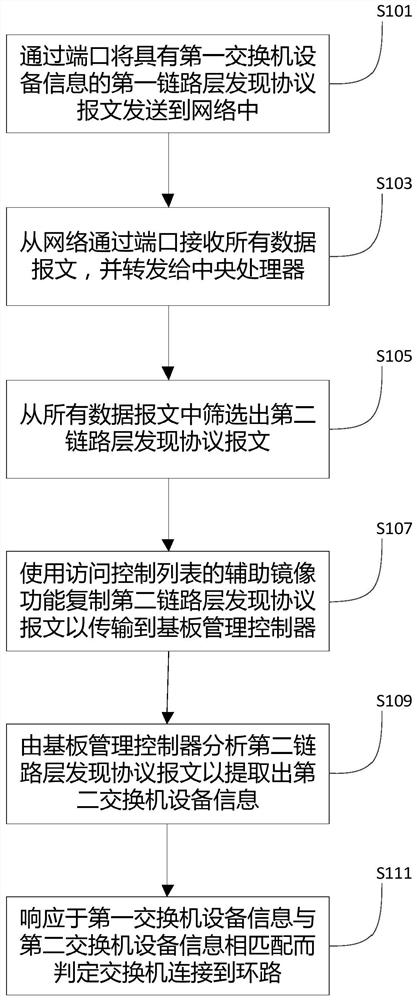
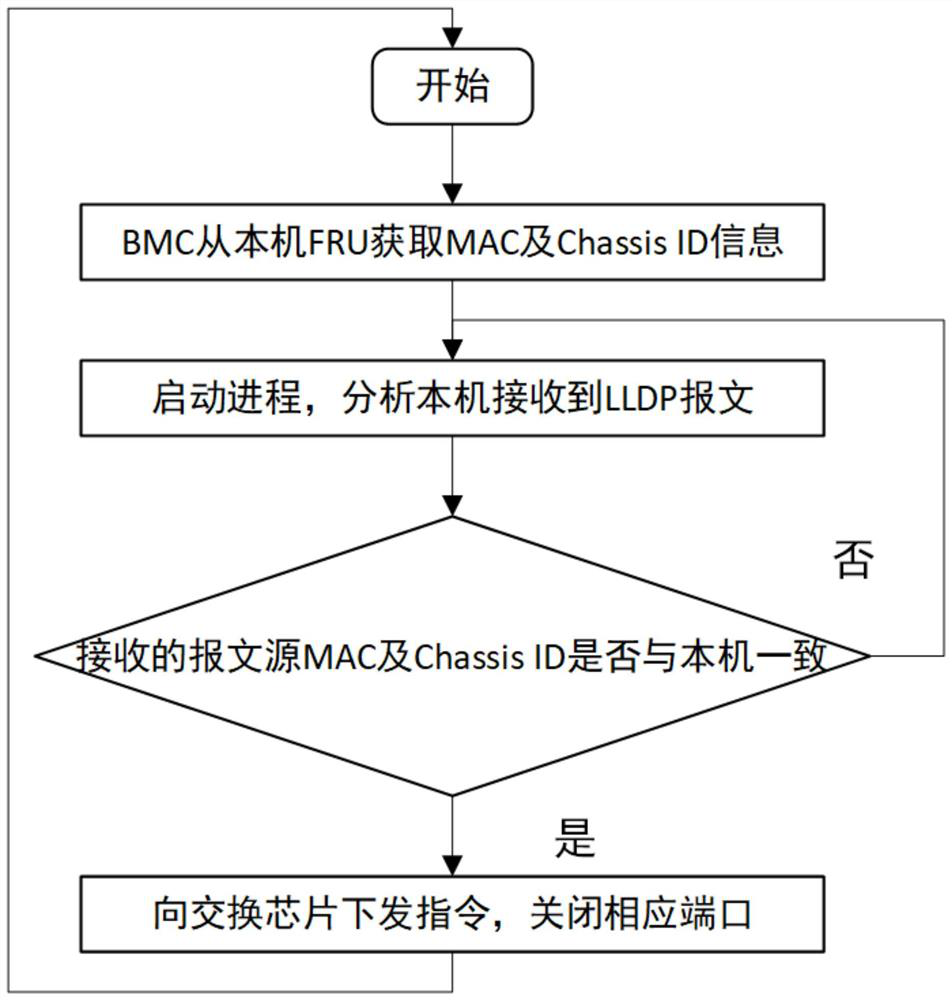
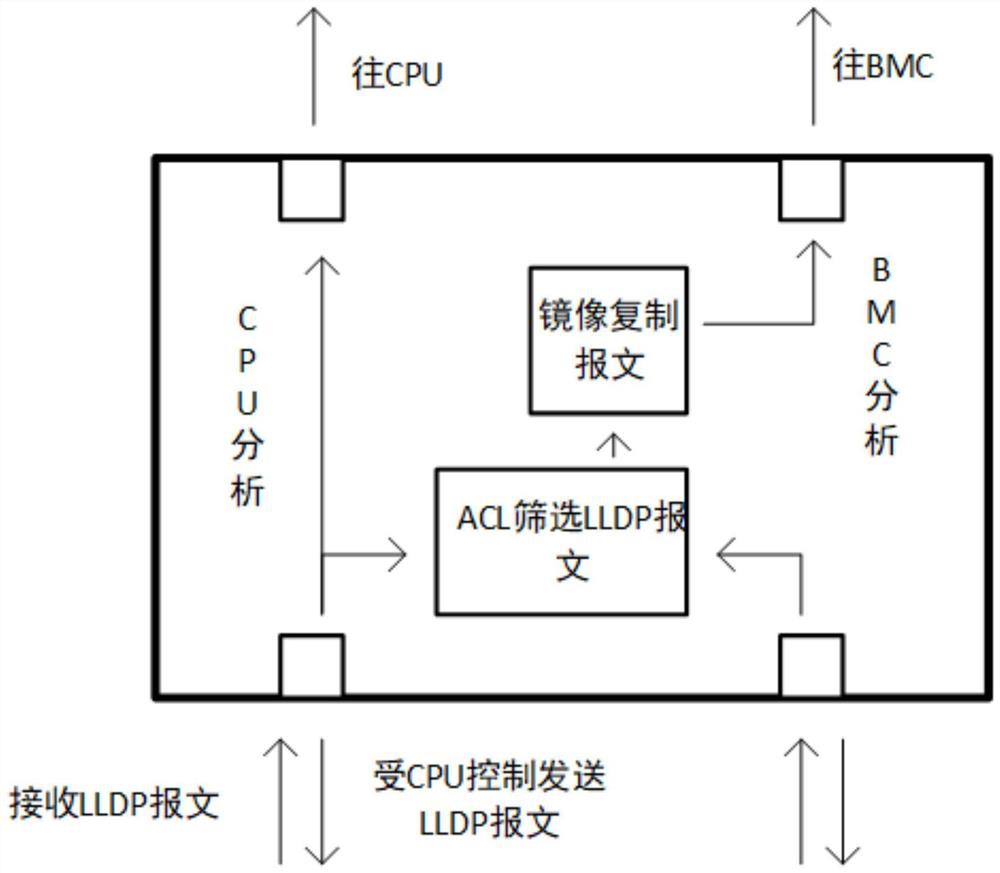
Switch loop detection method and device
ActiveCN112134775AReduce overheadReduce the burden onData switching networksHigh level techniquesEngineeringLink Layer Discovery Protocol
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Remote access control list generation and data packet processing method for CM
ActiveCN105812352AEnsure safetyImprove processing efficiencyTransmissionComputer hardwareInterface layer
The invention relates to the technical field of communications and networks, and provides a remote access control list generation and data packet processing method for a CM, for configuring a CM at an interface layer. The method comprises the following steps: writing an ACL command and adding the ACL command into a TLV43 field of a CM configuration file; the CM downloading the CM configuration file from a TFTP server and analyzing the CM configuration file, and then storing the ACL command obtained through analysis in a queue buffer zone; and when a CM interface receives or sends a data packet, obtaining the ACL command in the queue buffer zone, matching the ACL command with header information of the data packet, and according to a matching result, processing the data packet. According to the technical scheme provided by the invention, the network security can be ensured, the processing efficiency of CM equipment for the data packet is improved, the network performance is improved, far-end flexible configuration of the CM equipment can also be realized, and the onsite maintenance cost of the CM equipment is decreased.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap