Method of sending message, method of establishing secure connection, access point and work station
A technology for sending messages and access points, which is applied in the field of communication and can solve problems such as network access delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0136] like Figure 5 As shown, it is a signaling flowchart of Embodiment 1 of the method for establishing a secure connection in the present invention, and the process includes:
[0137] Step 501, with Figure 4 The steps 401-411 in are the same, and will not be repeated here;
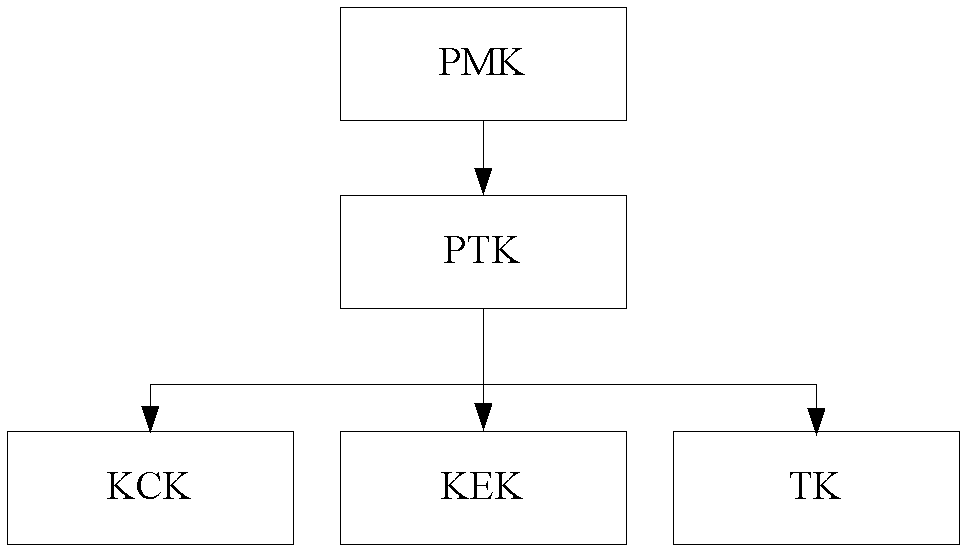
[0138]Step 502, AP generates PTK according to received PMK, and SNonce and ANonde, and generates KCK and KEK according to PTK; AP uses generated KCK to verify MSDU MIC; Verification is successful, AP uses generated KEK to decrypt DHCP-Discover message;
[0139] The process of decrypting the DHCP Discover message may also occur after step 503 .
[0140] Step 503, the AP sends an association reply message to the STA, and the association reply message sent by the AP to the STA may include AID, EAP_Success, EAPoL-Key and MIC; wherein the EAPoL-Key includes GTK and IGTK;
[0141] Step 504, the AP sends a DHCP-Discover message to the DHCP server, wherein the Rapid Commit option is carried;
[0142] Among t
Embodiment 2
[0153] like Image 6 As shown, it is a signaling flowchart of Embodiment 2 of the method for establishing a secure connection in the present invention, and the process includes:
[0154] Step 601, and Figure 4 The steps 401-411 in are the same, and will not be repeated here;
[0155] Step 602, AP generates PTK according to received PMK, and SNonce and ANonde, and generates KCK and KEK according to PTK; AP uses generated KCK to check MSDU MIC; Verification is successful, AP uses generated KEK to decrypt DHCP-Discover message;
[0156] Step 603, AP sends DHCP-Discover message to DHCP server, and this message carries Rapid Commit option;
[0157] Among them, the fast IP address allocation mechanism is optional.
[0158] In step 604, a timer is set in the AP, and starts timing after the AP sends a DHCP-Discover message to the DHCP server. If the timer expires and the AP has not received the DHCP-Ack message sent by the DHCP server, the AP sends an association reply message to th
Embodiment 3
[0165] like Figure 7 As shown, it is a signaling flow chart of Embodiment 3 of the method for establishing a secure connection in the present invention, and the process includes:
[0166] Step 701, with Figure 4 The steps 401-411 in are the same, and will not be repeated here;
[0167] Step 702, AP generates PTK according to received PMK, and SNonce and ANonde, and generates KCK and KEK according to PTK; AP uses generated KCK to verify MSDU MIC; Verification is successful, AP uses generated KEK to decrypt DHCP-Discover message;
[0168] Step 703, the AP sends a DHCP-Discover w / Rapid Commit message to the DHCP server;
[0169] Among them, the fast IP address allocation mechanism is optional.
[0170] Step 704, AP sends a DHCP-Discover message to the DHCP server, and this message carries the Rapid Commit option; a timer is set in the AP, and starts counting after the AP sends the DHCP-Discover message to the DHCP server, if the timer expires, the AP has not yet After receiv
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap