Encryption and decryption resource scheduling and key management-based encryption database and method
A key management and encryption key technology, applied in database model, digital data protection, structured data retrieval, etc. problem, to achieve the effect of efficient distribution, improved utilization, and improved throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments, where the schematic embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
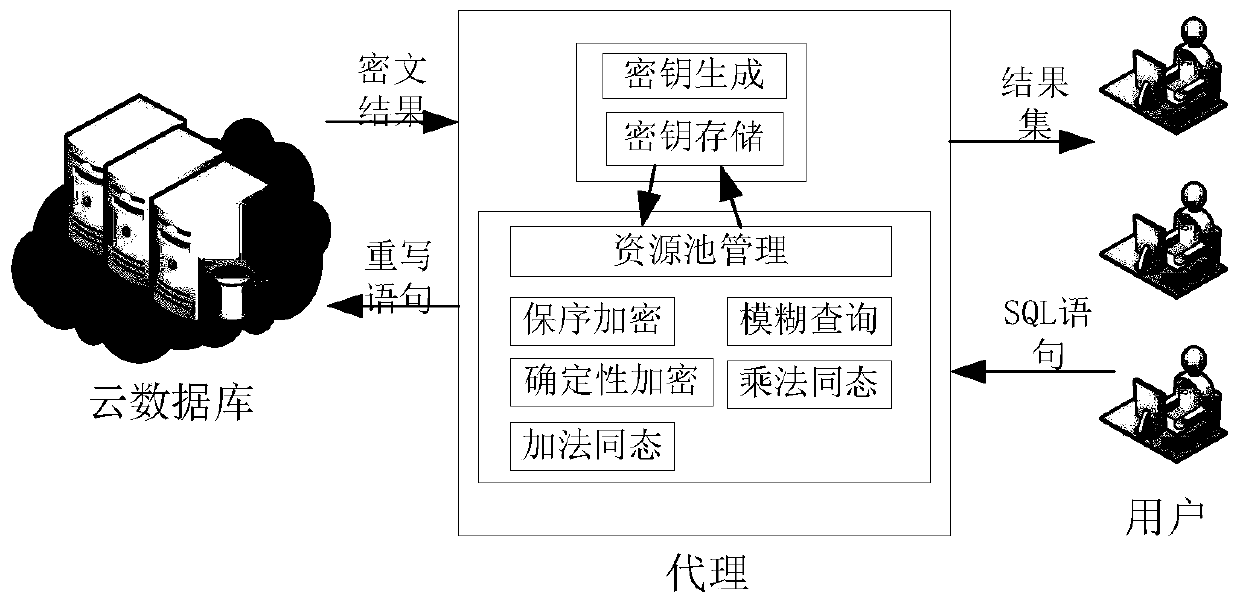
[0064] refer to figure 1 As shown, it is an overall frame diagram of the encryption database of the present invention, and an agent module is established, which includes a key management module and an encryption and decryption service module.
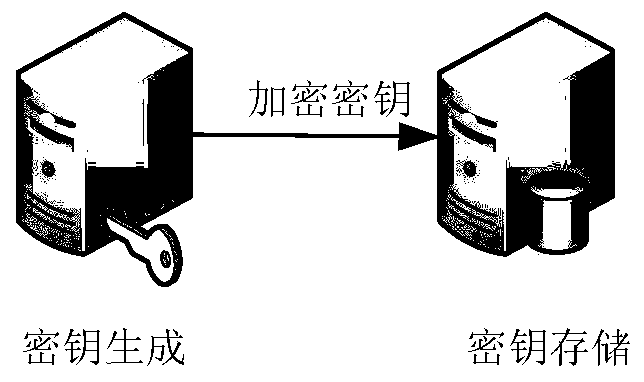
[0065] refer to figure 2 As shown, the key management module includes two modules of key generation and key storage. The key generation module generates the encryption keys required by different encryption methods corresponding to the user according to the user identity information, and the key storage module according to a certain storage rules to store the user's identity information and the corresponding encryption key.
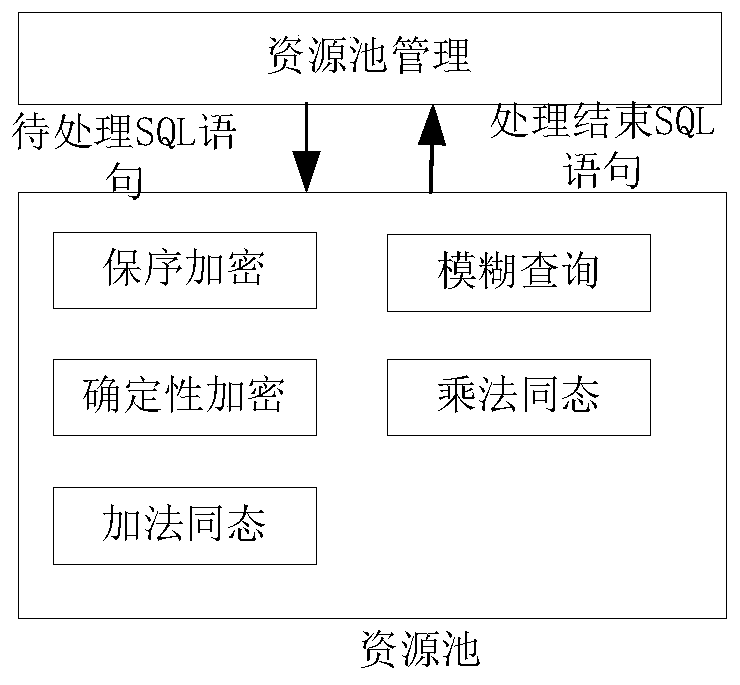
[0066] refer to image
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap