Data exchange method and security gateway
A security gateway and data exchange technology, applied in the field of Internet of Things, can solve problems such as the paralysis of the entire network, and achieve the effects of avoiding attacks, improving practicability, and ensuring performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0125] refer to Figure 5 , shows a flow chart of the steps of Embodiment 1 of a data exchange method of the present application. In the embodiment of the present application, the method is applied to the Internet of Views, and the Internet of Views is connected to the Internet through a security gateway, and the security gateway There is a first whitelist pre-configured in .
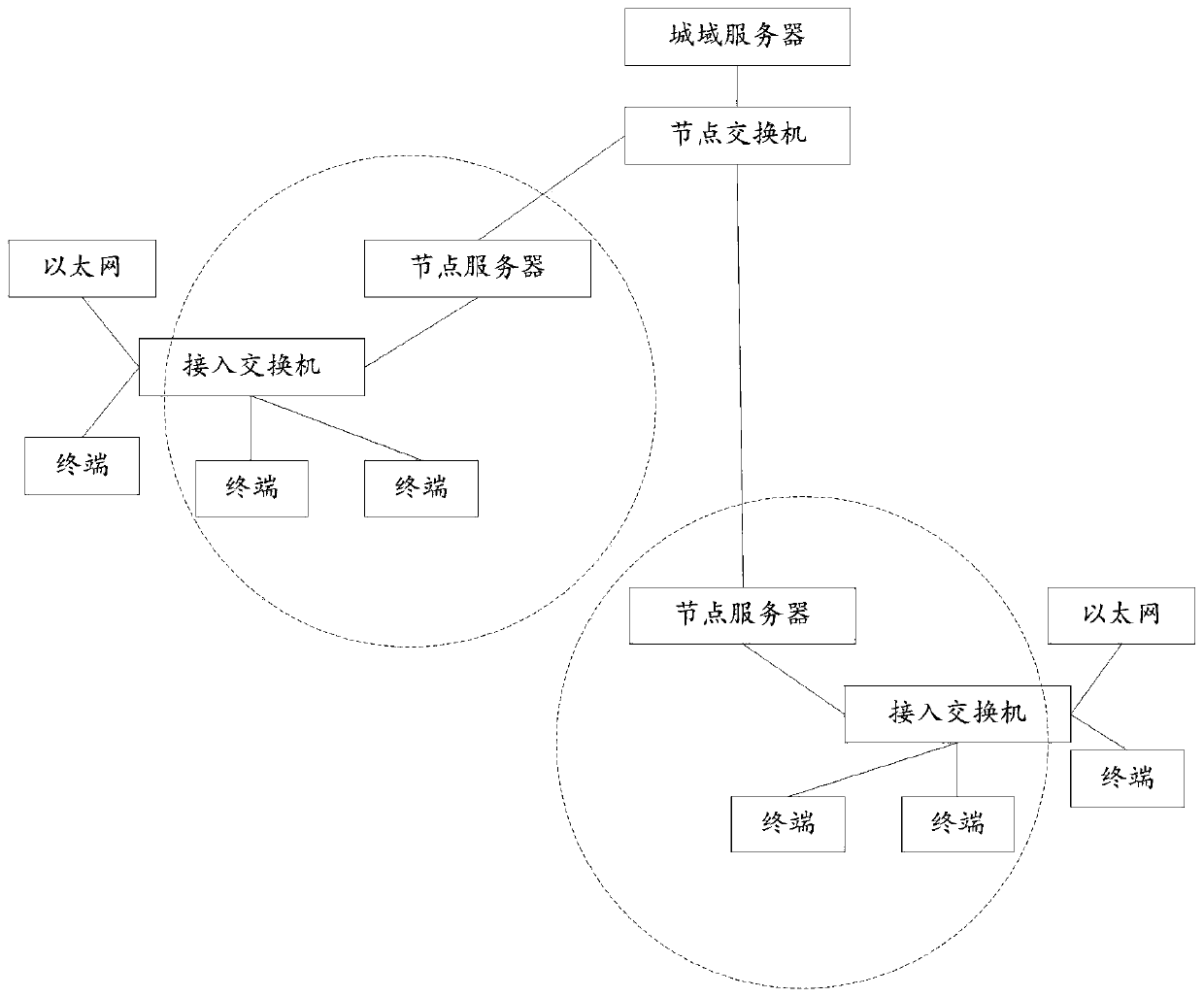
[0126] In the embodiment of this application, the security gateway can be deployed on network or service aggregation nodes such as node switches and node servers in the Internet of Vision, for example, it can be deployed on the co-translation server in the Internet of Vision, and the co-translation in the Internet of Vision The server is responsible for transmitting the data in the Internet of Vision to the Internet, or the data in the Internet to the Internet of Vision. Therefore, the co-translation server can be regarded as the network exchange node between the Internet of Vision and the Internet, and th
Embodiment 2
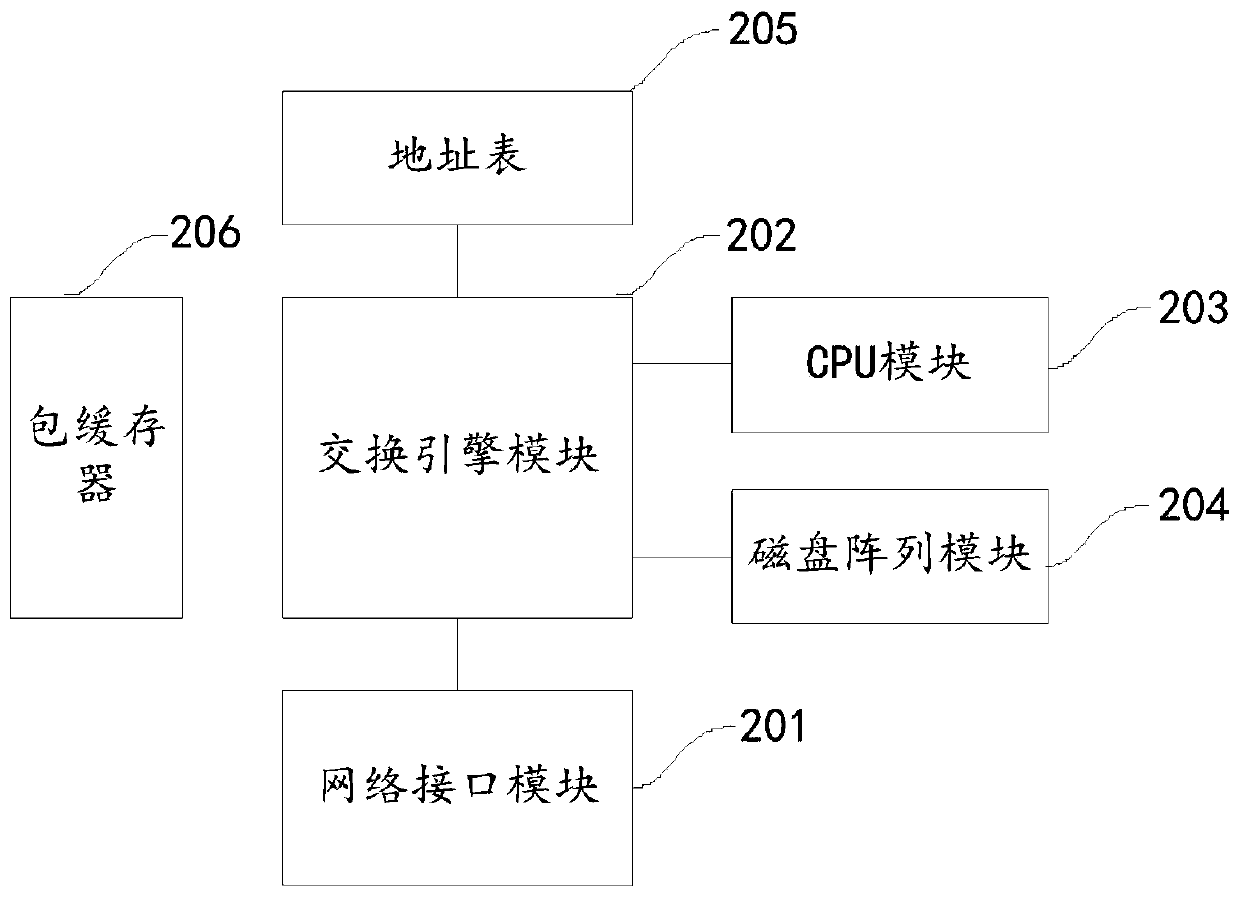
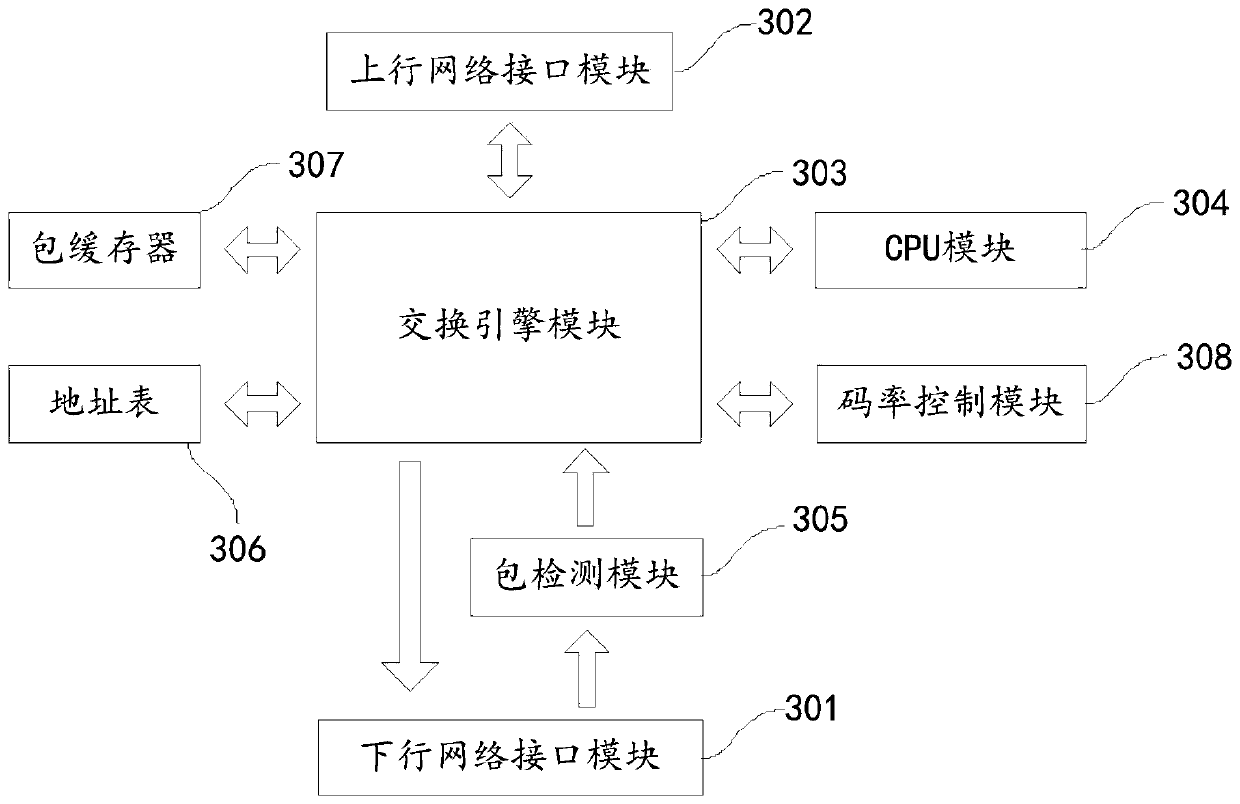
[0201] Such as Figure 8 It shows a security gateway in Embodiment 2 of the present application. Compared with the processing method in Embodiment 1, the security gateway can be applied to the Internet of View and the Internet, and includes a whitelist configuration module, which is pre-configured with the first A white list, the security gateway also includes:
[0202] The Internet of Vision gateway module 801 is used to verify the port information and protocol in each of the Internet of Vision data packets based on the pre-received first whitelist when receiving a plurality of Internet of Vision data packets from the Internet of Vision Type and MAC address are legal, and extract and verify legal N first Internet of Vision data packets from the plurality of Internet of Vision data packets; wherein, N is a positive integer.
[0203] The Internet gateway module 802 is configured to verify whether the port information, protocol type, and MAC address in each of the Internet data pa
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap