Method and device for preventing network attack
A network attack and network node technology, applied in the computer field, can solve problems such as EVPN paralysis, network errors, EVPNMAC address confusion, etc., and achieve the effect of reducing risks, avoiding refreshing, and reducing the risk of paralysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
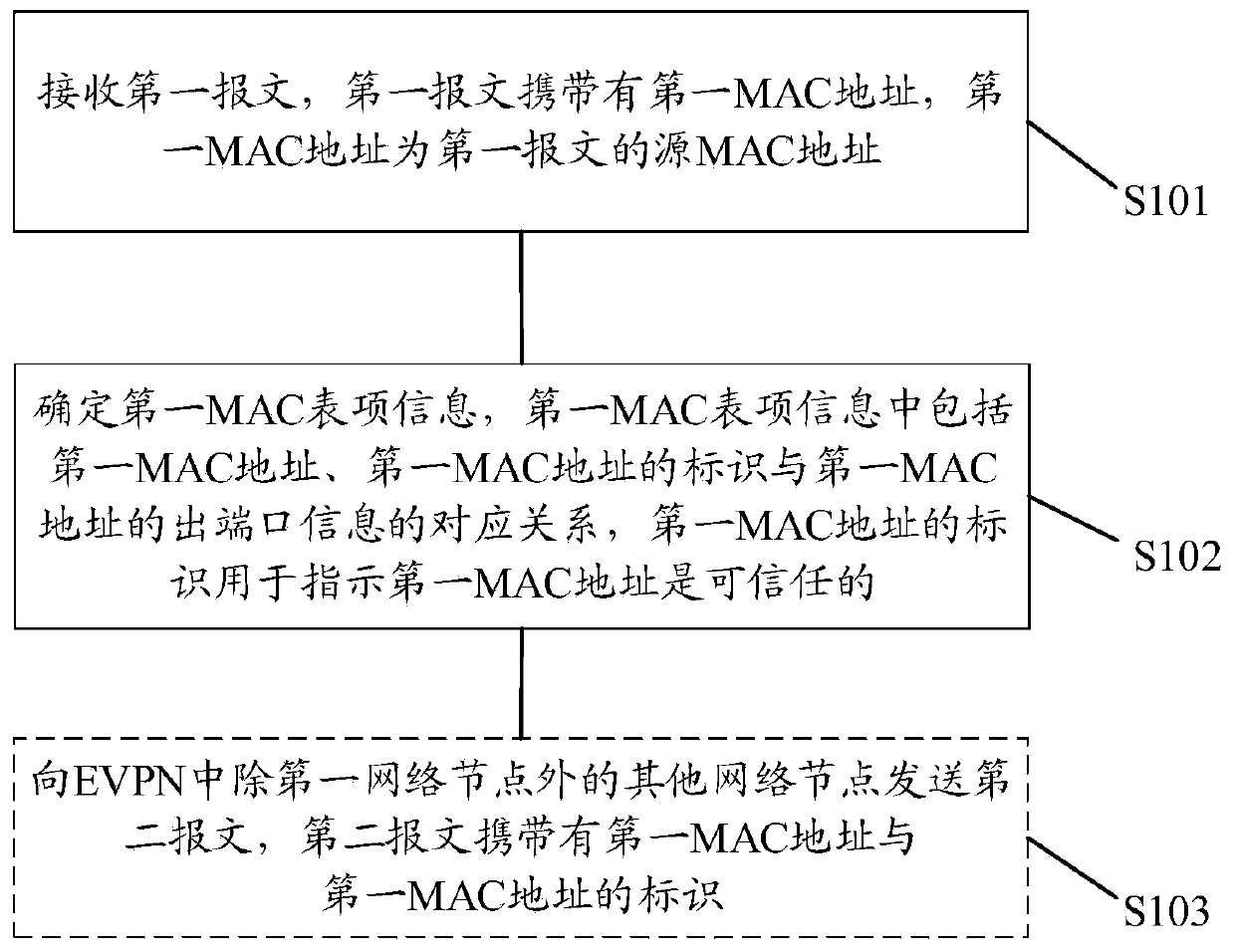
[0028] The technical solution in this application will be described below in conjunction with the drawings.
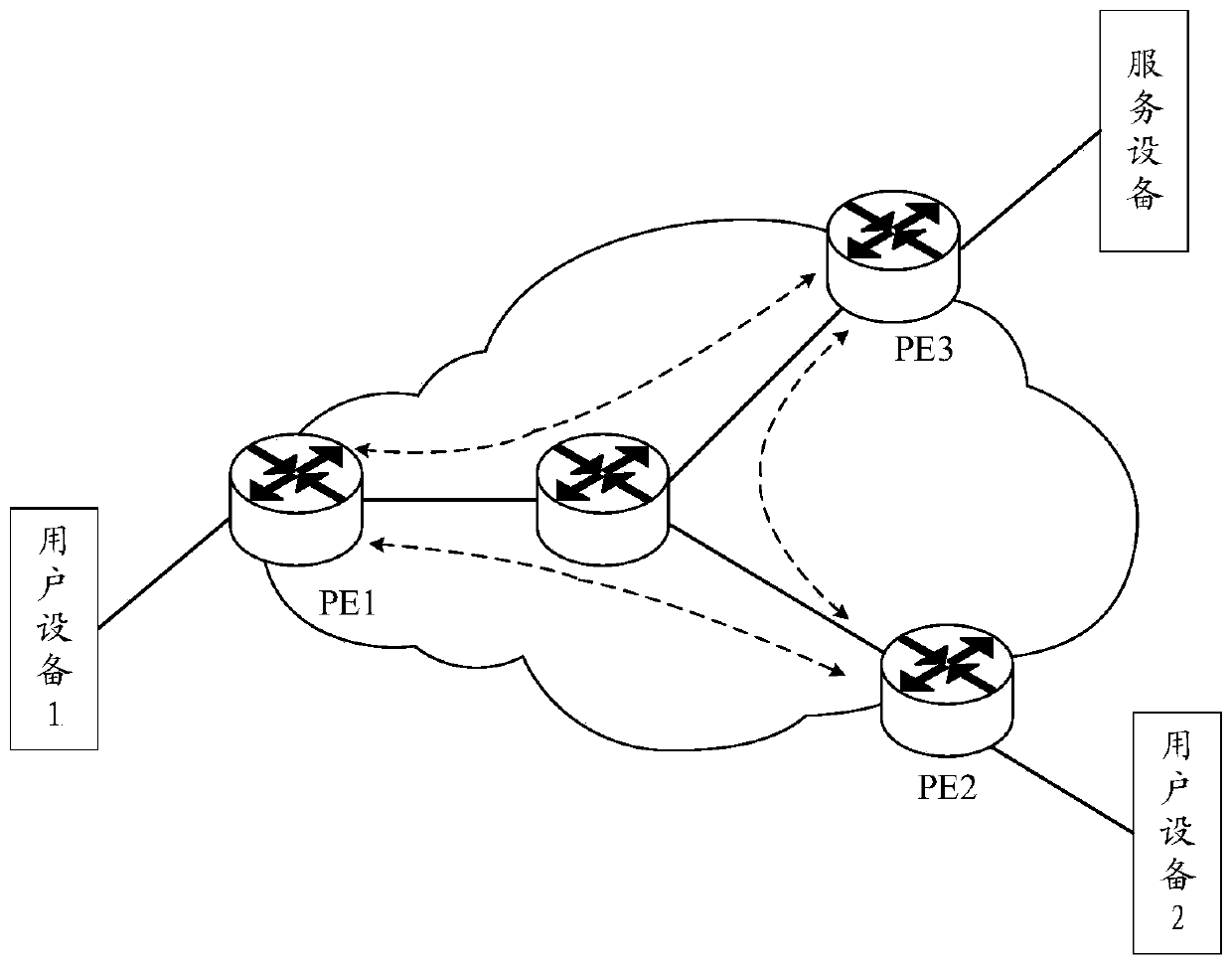
[0029] First combine figure 1 An introduction to the network architecture applicable to this application. figure 1 It shows an EVPN established by multiple network nodes (for example, PE). For example, multiple PEs can establish the EVPN based on BGP, and each PE is connected to multiple devices through its own port, and the multiple devices may include user equipment. And service equipment.
[0030] Such as figure 1 As shown, user equipment 1 accesses EVPN through PE1, user equipment 2 accesses EVPN through PE2, service equipment accesses EVPN through PE3, and information transmission between user equipment and service equipment can be performed through PE.
[0031] For example, the service device may send data packets to user equipment 1 through PE2 and PE1, and the service device may send data packets to user equipment 2 through PE2 and PE3.
[0032] In the embodiment of the p
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap