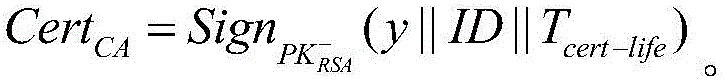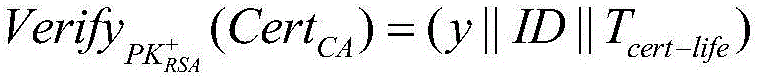Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2 results about "Public key certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject. In email encryption, code signing, and e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS, sometimes called by its older name Secure Sockets Layer (SSL), is notable for being a part of HTTPS, a protocol for securely browsing the web.
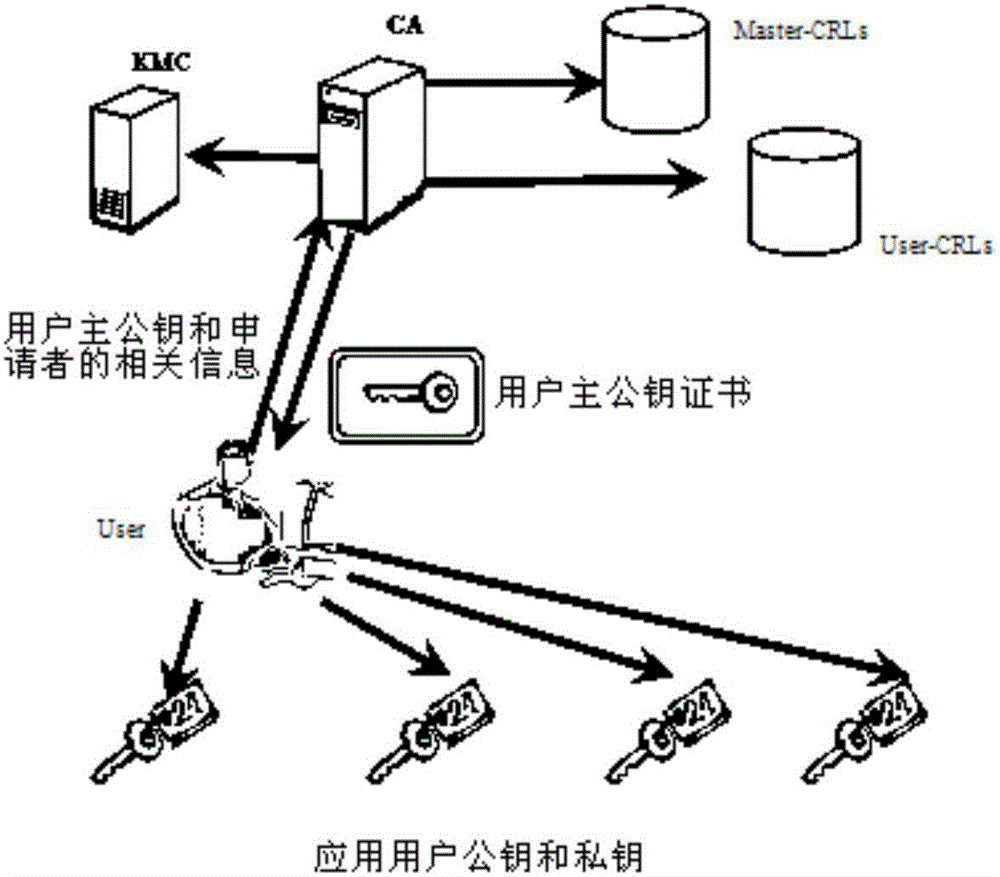
Reusable public key certificate scheme based on public key infrastructure
InactiveCN106059747AImprove management efficiencyReduce in quantityKey distribution for secure communicationUser identity/authority verificationRelevant informationPassword
Owner:成都蓝海贝信息技术有限公司
Software program module integrity detection method based on PKI public key algorithm
ActiveCN108667594AProtect intellectual propertyDoes not affect normal functionUser identity/authority verificationPublic key infrastructure trust modelsIntellectual propertyPublic key certificate
The invention discloses a software program module integrity detection method based on a PKI public key algorithm, and the method comprises the steps: carrying out the signing of a program module through a fixed certificate based on the PKI public key algorithm and a dedicated loading module; verifying module signature, loading a module, decrypting an imported table envelope, restoring an importedtable and starting a signature verifying thread of a code region during operation through comprising a fixed public key certificate, modulate signature and imported table digital envelope; entering anoriginal program inlet point for continuing the execution, wherein the secret keys employed during signing are consistent with the certificates employed during signature verification in a one-to-onemanner. The beneficial effects of the invention lie in that the method protects software from being tampered and used illegally under the condition that the normal function of the software is not affected, and also protects the intellectual property of a software owner.
Owner:KOAL SOFTWARE CO LTD
Popular searches
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap