File theft sensing method and system
A file and folder technology, applied in the transmission system, electrical components, etc., can solve the problems of increasing network traffic, increasing router tracking equipment overhead, high implementation and operation costs, etc., to achieve convenient deployment, low-cost perception and tracking, and improve efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the purpose, features and advantages of the present invention more obvious and easy to understand, the technical core of the present invention will be further described in detail below in conjunction with the accompanying drawings and examples instruction of.
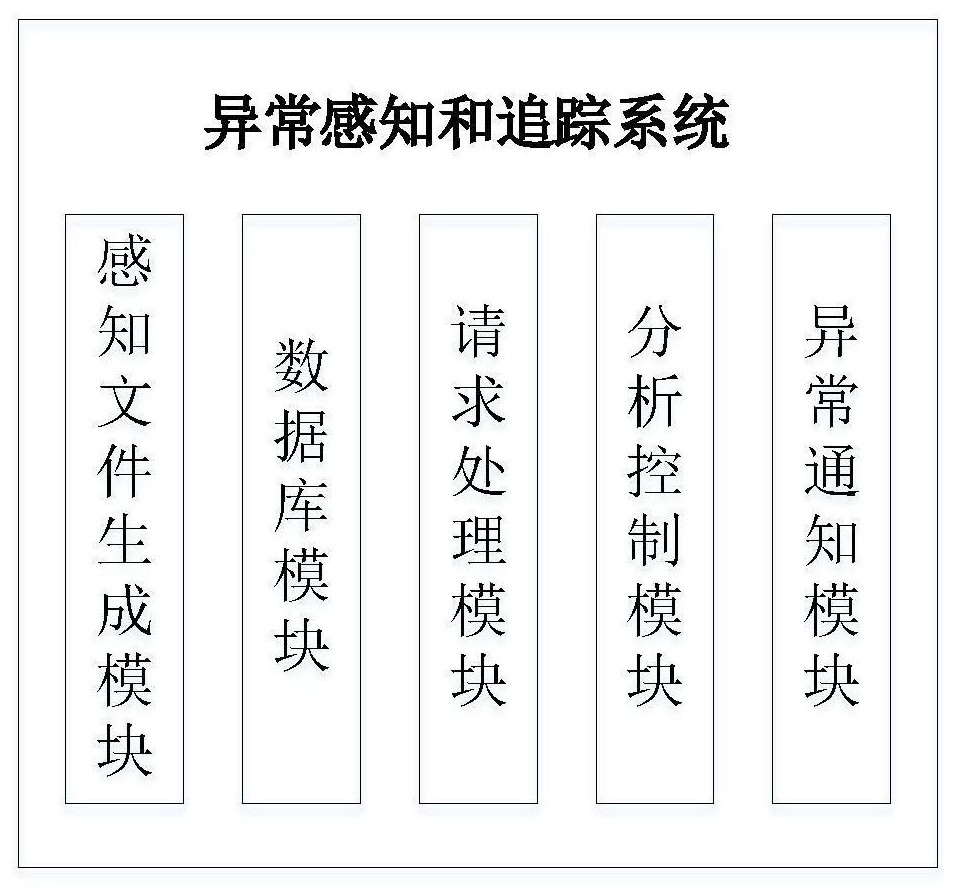
[0042] In the present invention, a set of perception and tracking system for document theft is designed by adopting the strategy of active marking and tracking, which can effectively solve the above-mentioned existing problems.
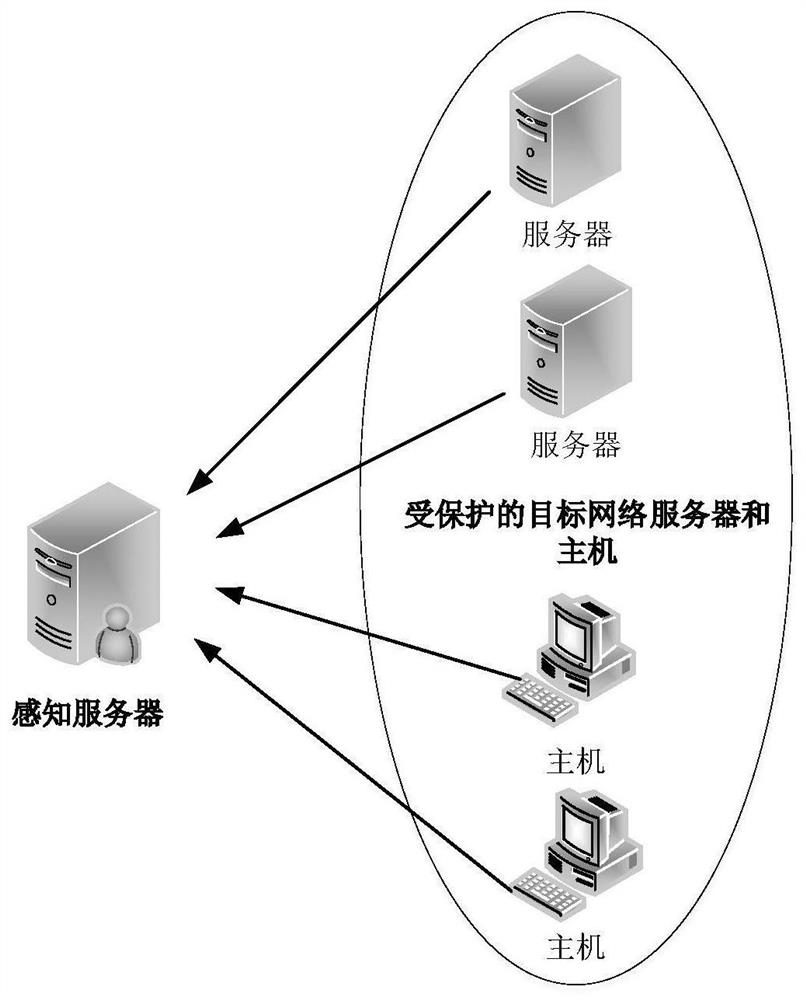
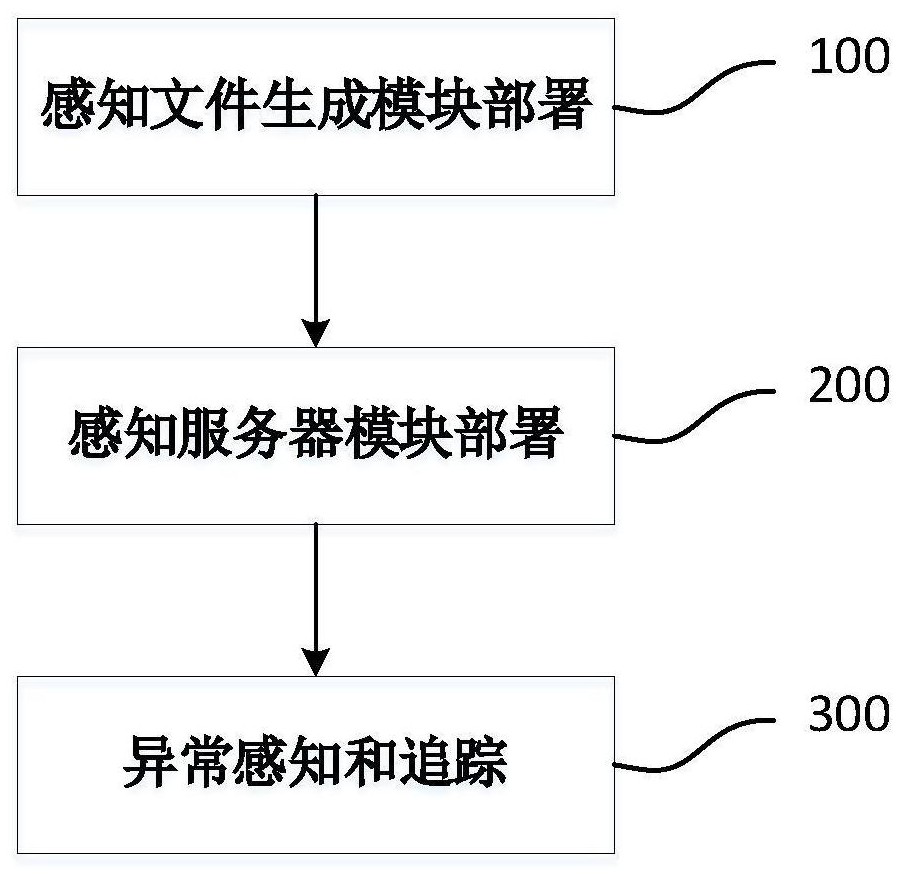
[0043] Such as figure 1 As shown in Fig. 1 , a schematic diagram of the overall composition of the file theft perception and tracking system is physically composed of multiple perception file generation clients embedded in the target host system and a comprehensively controlled anomaly perception and tracking master server.
[0044] Such as fig
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap