Weak password judgment method and device, equipment and storage medium
A storage medium and weak password technology, applied in the field of network security, can solve the problems of inability to hit, time-consuming, manpower, and false negatives, and achieve the effect of reducing the probability of false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
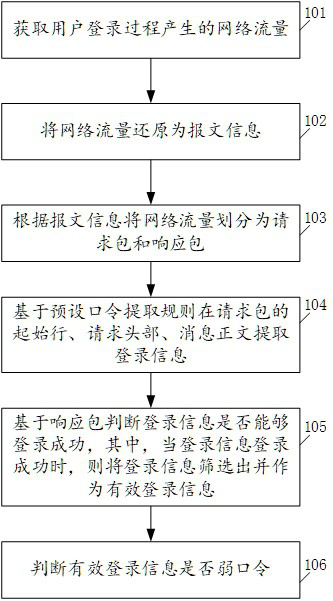
[0049] see figure 1 , figure 1 It is a schematic flowchart of a method for judging a weak password disclosed in the embodiment of the present application. Such as figure 1 As shown, the method of the embodiment of the present application includes the following steps:
[0050] 101. Obtain the network traffic generated during the user login process;
[0051] 102. Restore network traffic to packet information;
[0052] 103. Divide network traffic into request packets and response packets according to message information;
[0053] 104. Based on the preset password extraction rules, the login information is extracted from the start line, request header, and message body of the request packet;
[0054] 105. Based on the response packet, it is judged whether the login information can be successfully logged in, wherein, when the login information is successfully logged in, the login information is screened out and used as valid login information;
[0055] 106. Determine whether the
Embodiment 2
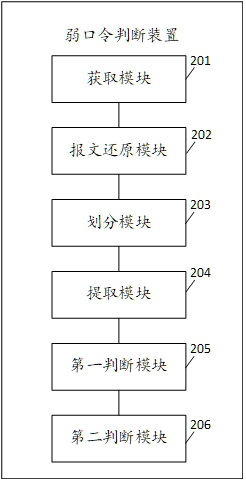
[0102] see figure 2 , figure 2 It is a schematic structural diagram of a weak password judging device disclosed in the embodiment of this application. Such as figure 2 As shown, the device of the embodiment of the present application includes the following functional modules:
[0103] Obtaining module 201, configured to obtain network traffic generated during the user login process;
[0104] A message restoration module 202, configured to restore network traffic to message information;
[0105] A division module 203, configured to divide network traffic into request packets and response packets according to message information;
[0106]The extraction module 204 is used to extract the login letter from the initial line of the request packet, the request header, and the message body based on the preset password extraction rule;
[0107] The first judging module 205 is used to judge whether the login information can be logged in successfully based on the response packet, whe
Embodiment 3
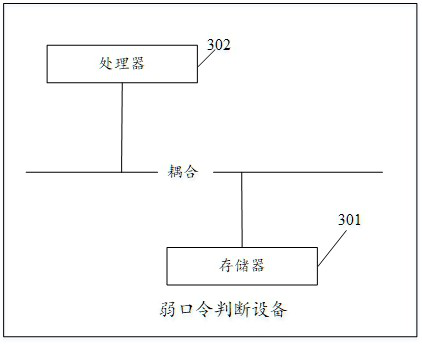
[0112] see image 3 , image 3 It is a schematic structural diagram of a weak password judging device disclosed in the embodiment of this application. Such as image 3 As shown, the equipment of the embodiment of the present application includes:
[0113] A memory 301 storing executable program codes;
[0114] a processor 302 coupled to the memory 301;
[0115] The processor 302 invokes the executable program code stored in the memory 301 to execute the method for determining a weak password according to Embodiment 1 of the present application.
[0116] The device in the embodiment of this application uses the weak password judgment method. On the one hand, it can filter out valid login information from a large number of login information, thereby reducing the workload of weak password judgment and reducing the disposal cost of weak passwords. On the other hand, this application The embodiment can further judge whether the login information is a weak password by customizing
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap