Security system and method for a mobile phone
a mobile phone and security system technology, applied in the field of security systems and methods, can solve the problem of nothing that can be done to prevent unauthorized access to private information on the mobile phon
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
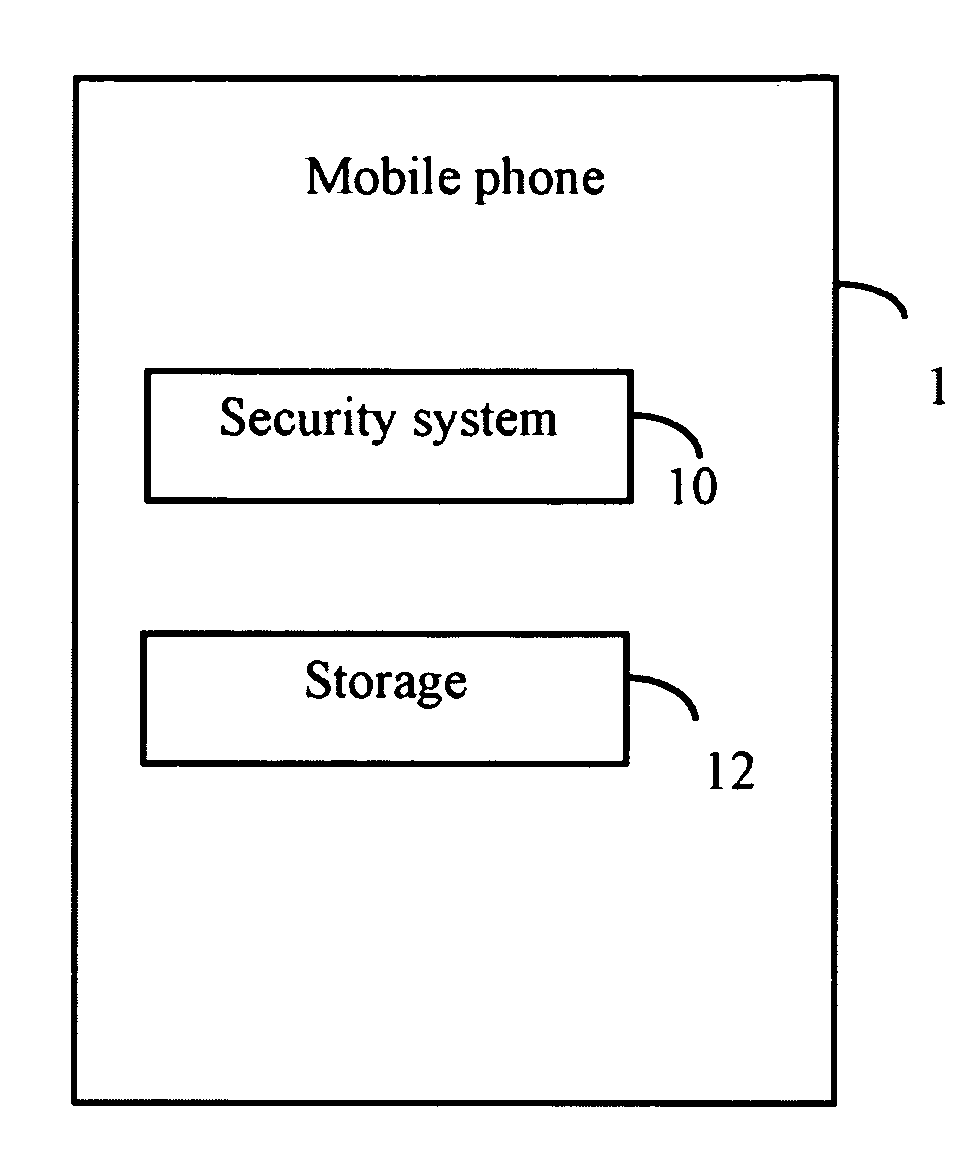
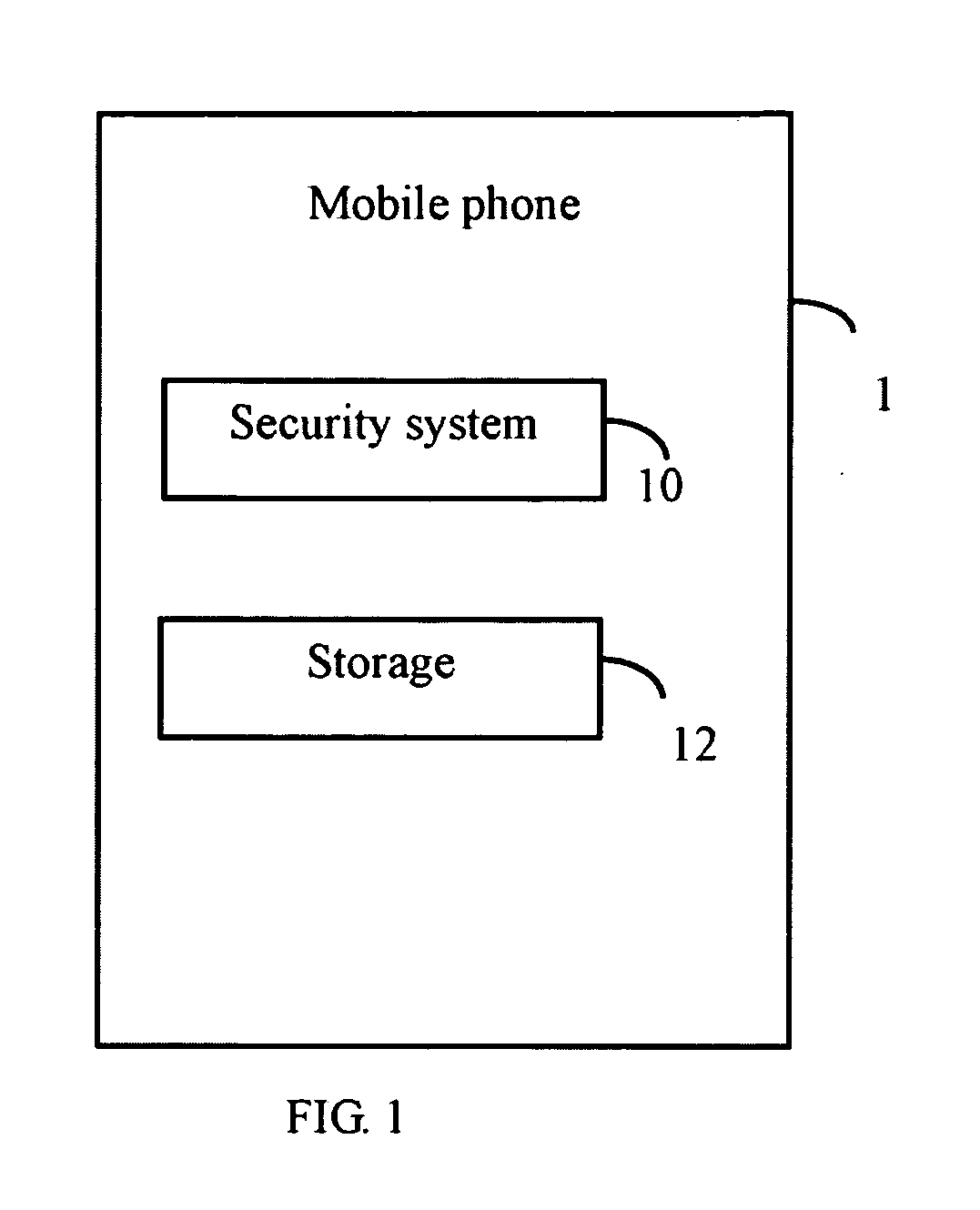
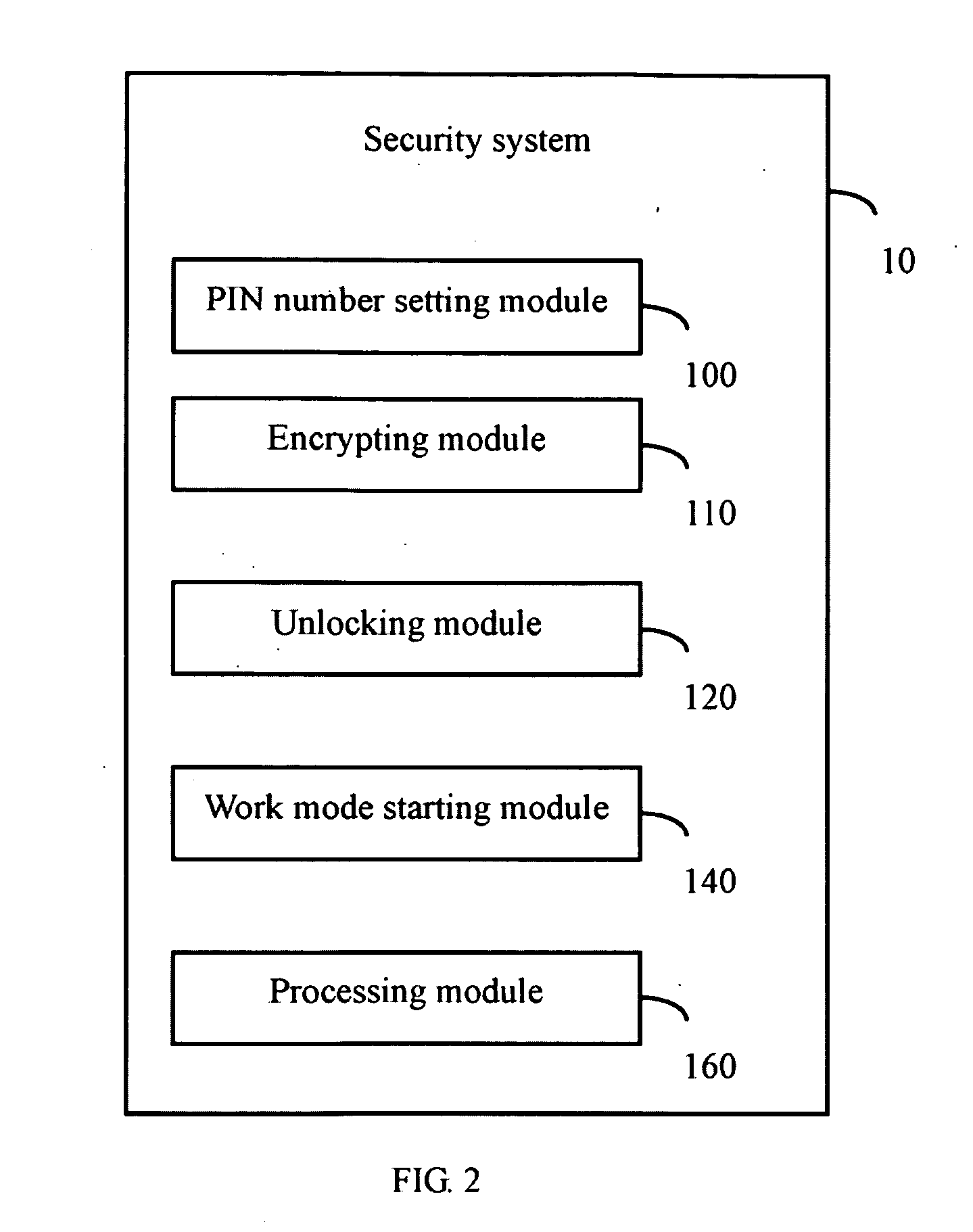
[0015]FIG. 1 is a block diagram of one embodiment a mobile phone 1 comprising a security system 10. The security system 10 is configured for setting security measurements for the mobile phone 1. The security measurements, in one embodiment comprises setting least two PIN numbers, encrypting an electronic phone book system (shown in FIG. 5) of the mobile phone 1, setting a security status for each contact in the phone book system, and starting a secure work mode of the mobile phone 1. Further details of these security measurements will be explained in further detail herein.
[0016]The encrypted phone book system includes information about an identification (ID) name, address, phone number(s), and security status for each contact in the phone book system. For example, in FIG. 6, a contact has an ID name “Peter,” an address “Shenzhen,” a phone number “135432546,” and a security status “yes.” In other words, a call and a message from Peter may be placed and / or sent as a secured call and a
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap