Network covert channel construction method based on Web application directory tree
A technology of covert channel and construction method, applied in the field of information hiding, can solve problems such as poor covertness, and achieve the effect of good covertness and good transmission rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment
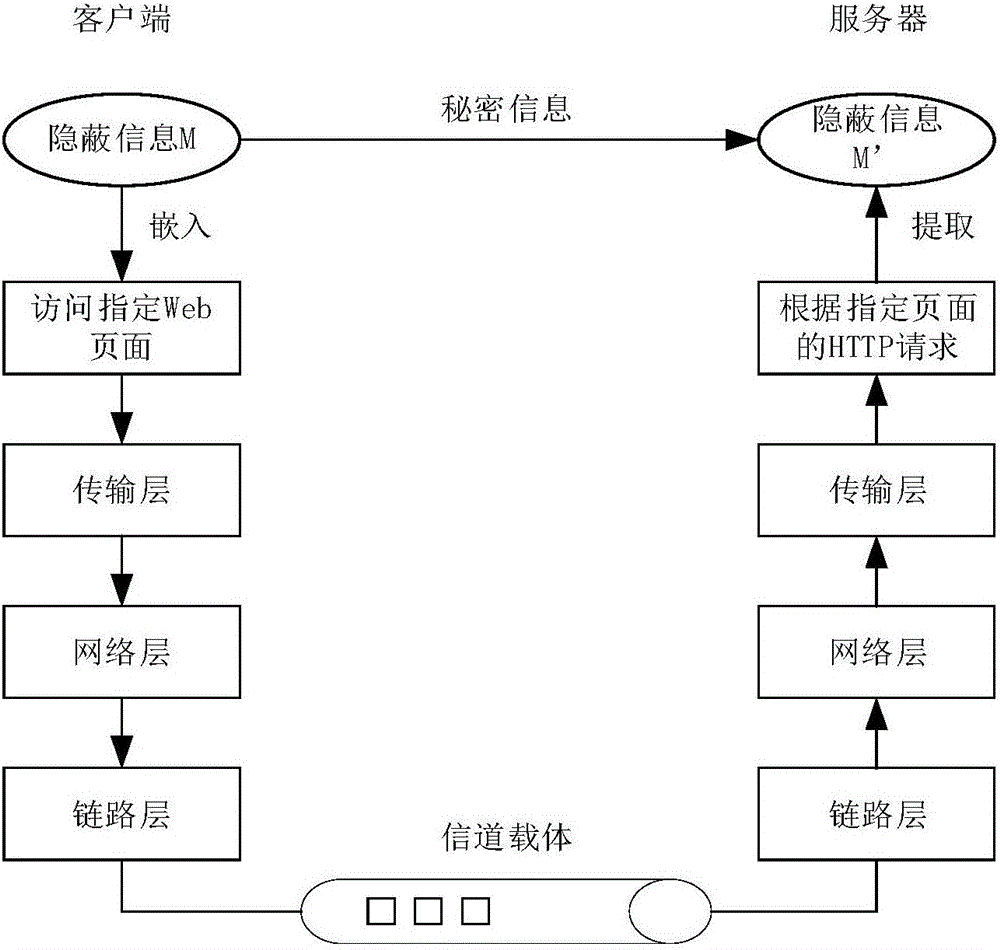
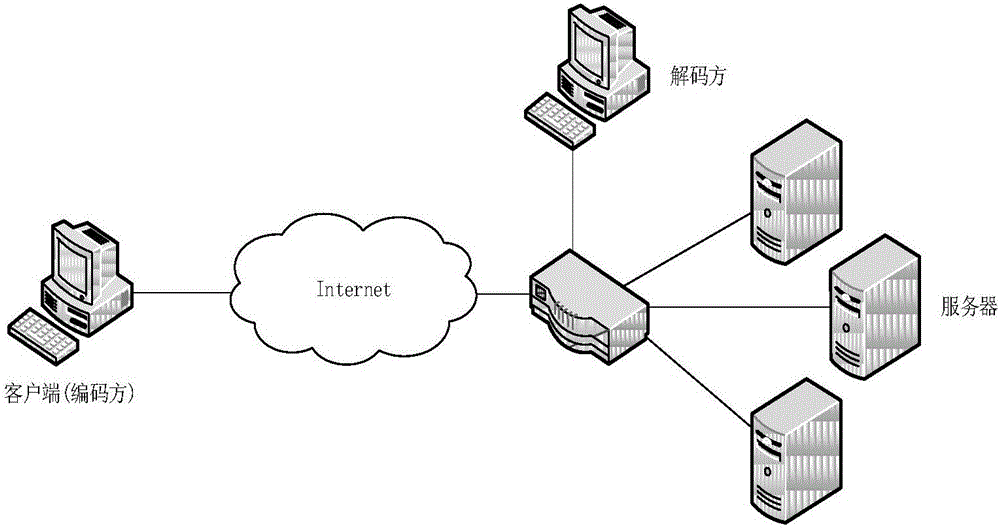
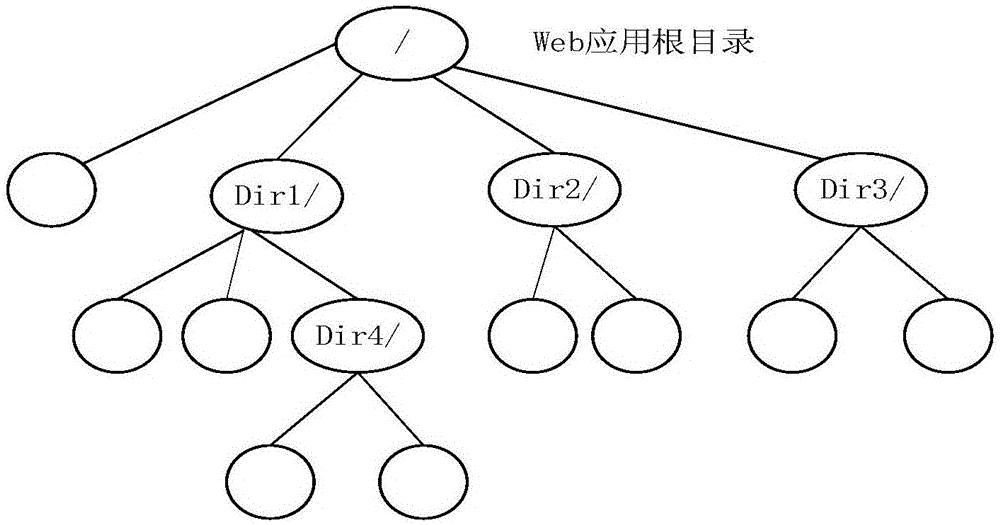
[0025] Such as figure 1 , figure 2 , image 3 As shown, a method for constructing a network covert channel based on a web application directory tree specifically includes the following steps:
[0026] The first step is to initialize the client program of the network covert channel. The user needs to input parameters at the sender end of the covert channel, including the address of the recipient and the intermediate value of the directory tree height of the selected Web application. The sender of the covert channel bases on these parameters to send covert information, and the entire covert channel construction process is realized through the client program.
[0027] The second step is to embed secret information: encode the concealed information to be sent into a binary bit stream represented by 0 and 1 and encrypt it using the DES encryption algorithm, and then map these bit streams to the server side through the embedding function Among the request operation behaviors of pre
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap