User privacy management apparatus and method in mobile communications system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
third embodiment
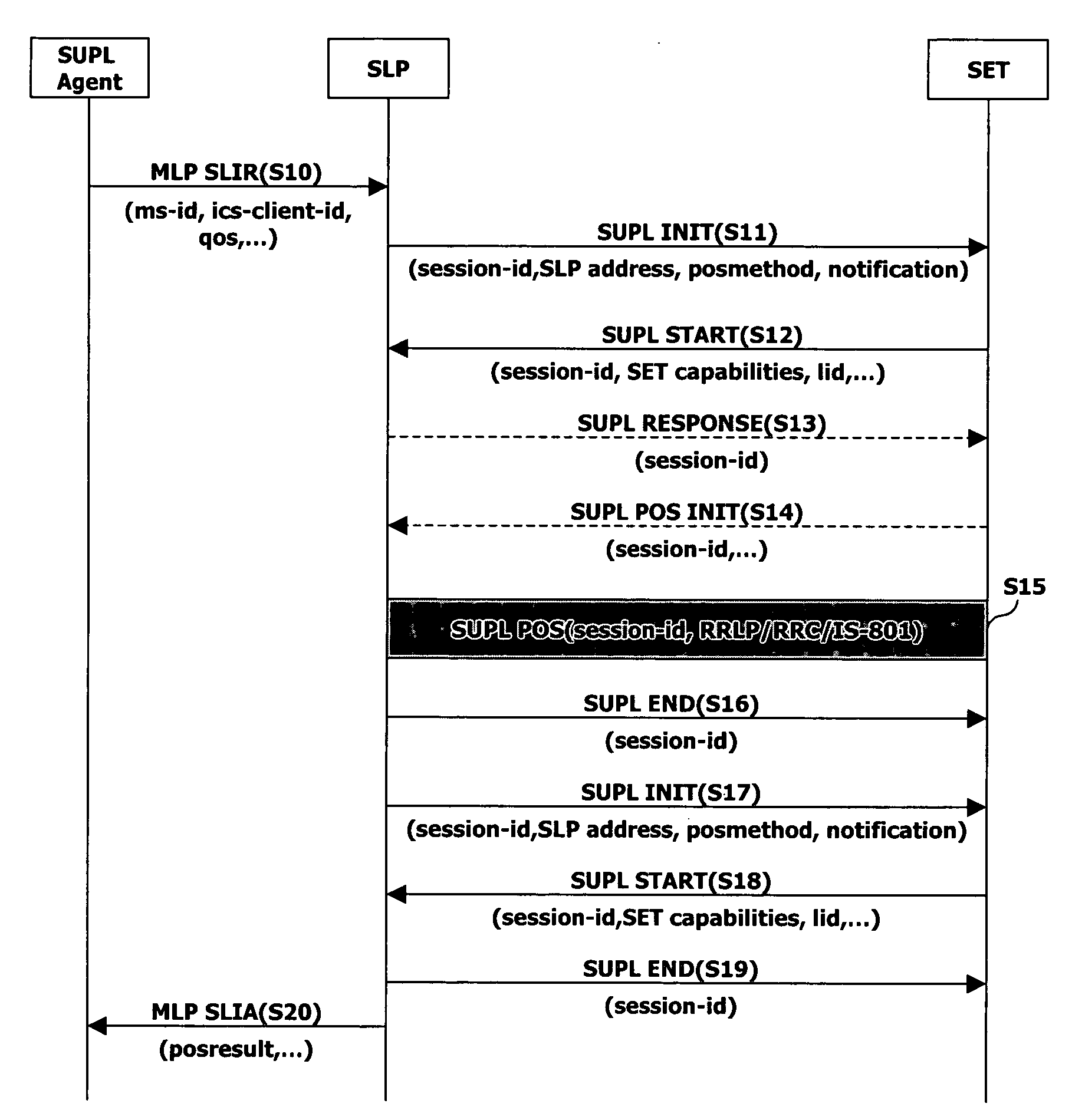
[0079]FIG. 5 illustrates a user privacy management method in a mobile communications system according to the present invention, in which the SET user is queried about whether the positioning resultant value should be transmitted by using a new dedicated message. Preferably, the dedicated message is a session notification (SUPL NOTIFICATION) message.
[0080] Referring to FIG. 5, in the third embodiment of the present invention, for an additional notification, a SUPL NOTIFICATION message and a SUPL NOTIFICATION RESPONSE message are used instead of the SUPL INIT and SUPL START messages. For all other portions in FIG. 5, which are similar to those shown in FIG. 4, detailed explanations therefor have been omitted to prevent the differences between FIGS. 4 and 5 from being obscured.
[0081] The SLP can know whether to grant permission for positioning of user C (case 4) having requested for positioning on the basis of the confirmation result transmitted from the PCE or privacy information having
fifth embodiment
[0091]FIG. 7 illustrates a user privacy management method according to the present invention.
[0092] The fifth embodiment of the present invention shows a SUPL message transmission process for a case of performing a privacy management by dividing the SLP (Home SLP) into a SUPL Location Center (SLC) and a SUPL Positioning Center (SPC) according to their functional aspects. The SLP, as a network component, may include a SPC which is an entity for calculating an actual location and a SLC for managing other functions of the SLP excluding the function for calculating location information, for instance, roaming, resource managing, and the like.
[0093] That is, the fifth embodiment corresponds to an example in which the SLP is divided into the SPC for calculating a location by exchanging messages with the actual SET, and the SLC for performing other functions of the SLP excepting the function for calculating the location information, so that the SPC performs the positioning process directly wi
sixth embodiment
[0101]FIG. 8 illustrates a user privacy management method of a mobile communications system according to the present invention.
[0102] The sixth embodiment illustrates a procedure in which, when the location of the SET is completely calculated through the SUPL positioning process, the SUPL session is terminated, and the user notification is transmitted to the SET at another positioning session according to a user privacy setting.
[0103] Referring to FIG. 8, first, steps (S80 to S85) therein are the same as those steps (S60 to S65) shown in FIG. 6 except their numerals, and detailed explanations therefor have been omitted. That is, operations in the fourth embodiment and the sixth embodiment of the present invention may be different from each other after calculating the location.
[0104] When the SUPL positioning process is performed to calculate the location of the SET (S85), the SLP transmits a SUPL END message to the SET to inform that the positioning process would be initiated any mor
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap