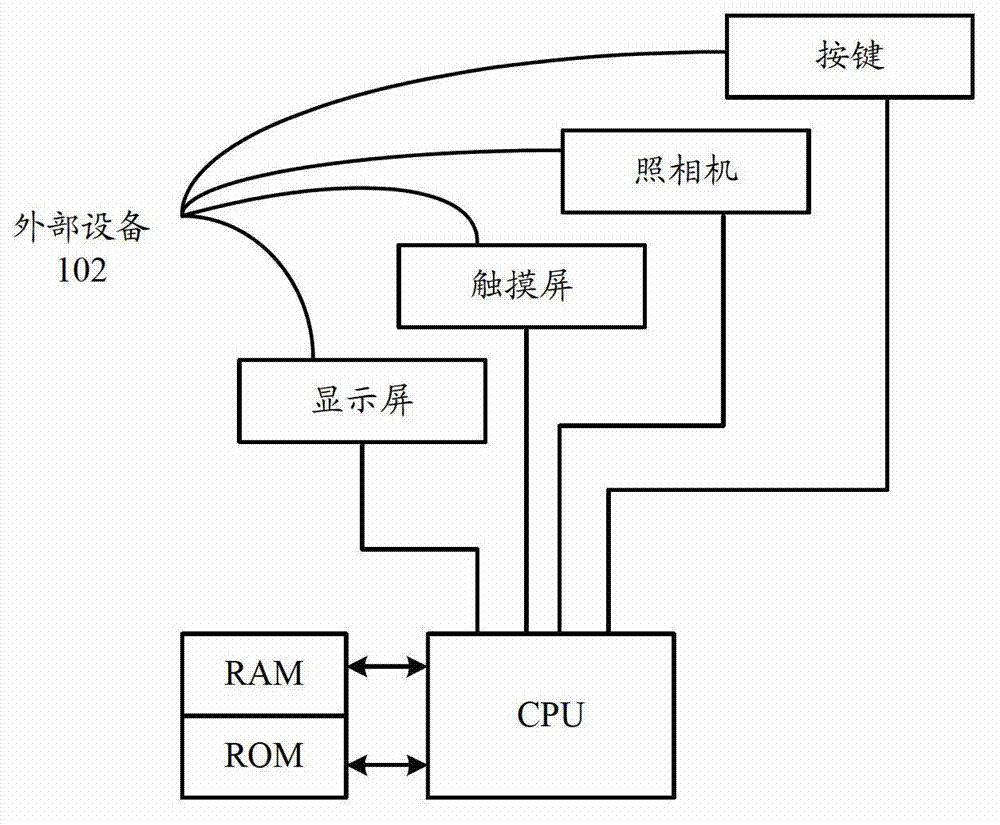
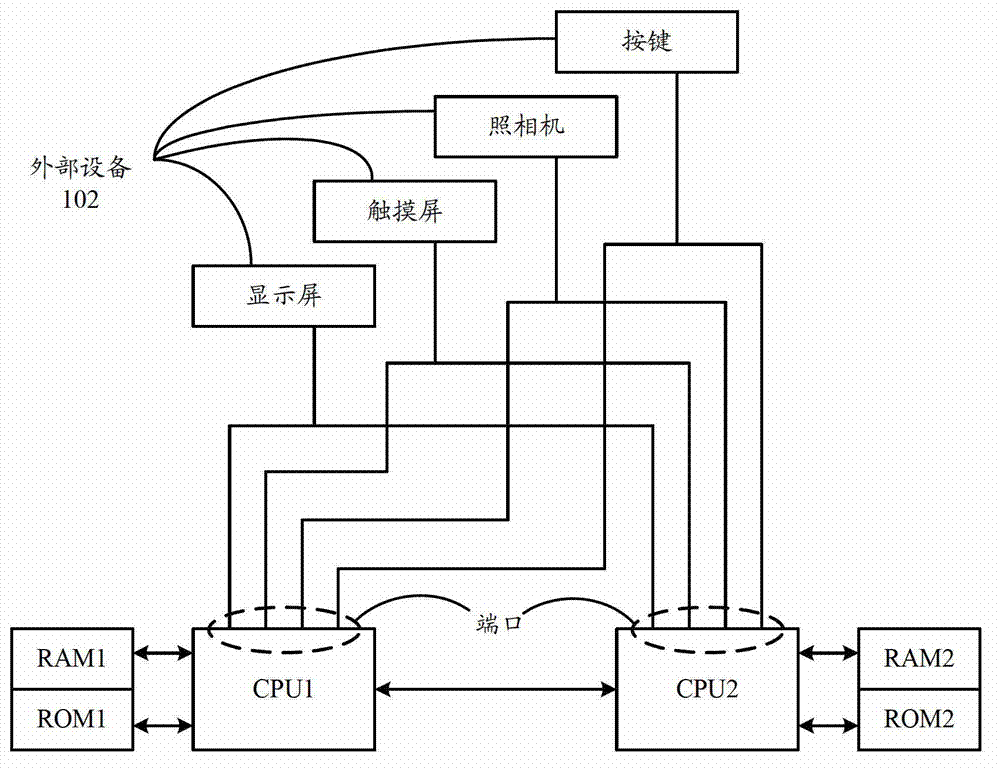
Terminal
A terminal and port technology, applied in the field of data security, can solve the problem of insecurity of private data such as user information, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0062] Among multiple CPUs for processing private data / non-private data, a certain CPU acts as a “relay” with the external device 102 , while other CPUs realize interaction with the external device 102 through the “relay”.
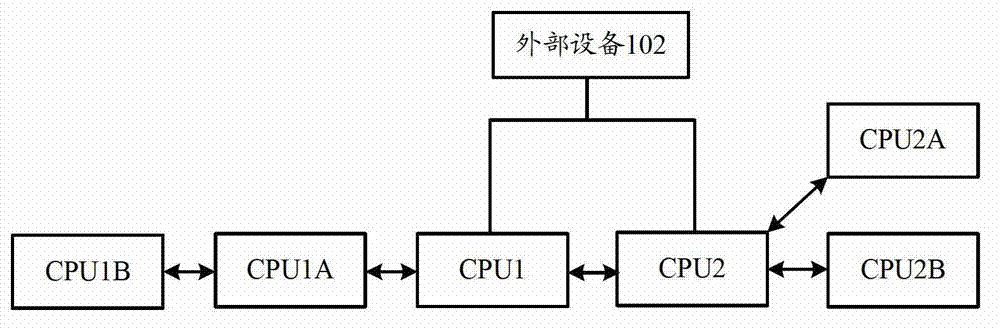
[0063] Specifically, such as image 3 As shown, it is assumed that a connection is established between CPU1 and the external device 102, and other multiple CPUs for processing private data are connected with CPU1 in a "serial" manner; at the same time, it is assumed that a connection is established between CPU2 and the external device 102, Other multiple CPUs for processing non-private data are connected with CPU2 in a "parallel" manner.
[0064] For the "serial" mode: when CPU1 needs to interact with external device 102, CPU1 directly performs data interaction with external device 102; when CPU1A needs to interact with external device 102, CPU1 performs data forwarding; when CPU1B needs to communicate with external When the device 102 interacts, CPU1A and
Embodiment approach 2
[0070] Among multiple CPUs for processing private data / non-private data, each CPU is "parallel connected" to the external device 102, and directly interacts with the external device 102 without requiring other CPUs as "relays".
[0071] Specifically, such as Figure 4 As shown, CPU1, CPU1A, and CPU1B for processing private data are respectively connected to the external device 102, while CPU2, CPU2A, and CPU2B for processing non-private data are also respectively connected to the external device 102.
[0072] At the same time, the "serial" and / or "parallel" methods mentioned in the above text can be used among multiple CPUs with the same processing function. As a specific example, Figure 4 It shows that: CPU1, CPU1A, CPU1B for processing private data adopts "serial connection" mode, while CPU2, CPU2A, CPU2B for processing non-private data adopts "parallel connection" mode.
[0073] When each CPU is connected to the external device 102, a CPU for one processing function may
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap