Industrial protocol detection method and device, computer equipment and storage medium
An industrial protocol and detection method technology, applied in the direction of safety communication devices, digital transmission systems, electrical components, etc., can solve problems such as interruption of equipment, interruption of industrial production, and unrealization of technology, and achieve the effect of optimal applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
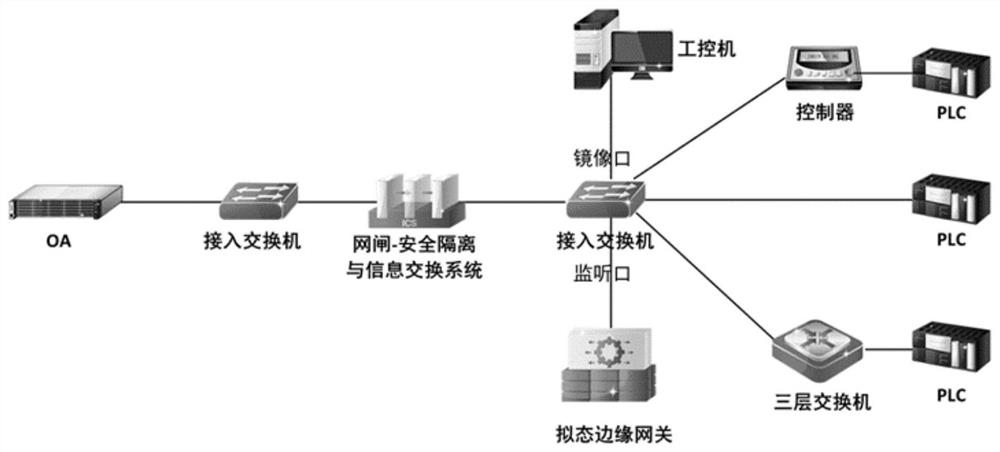
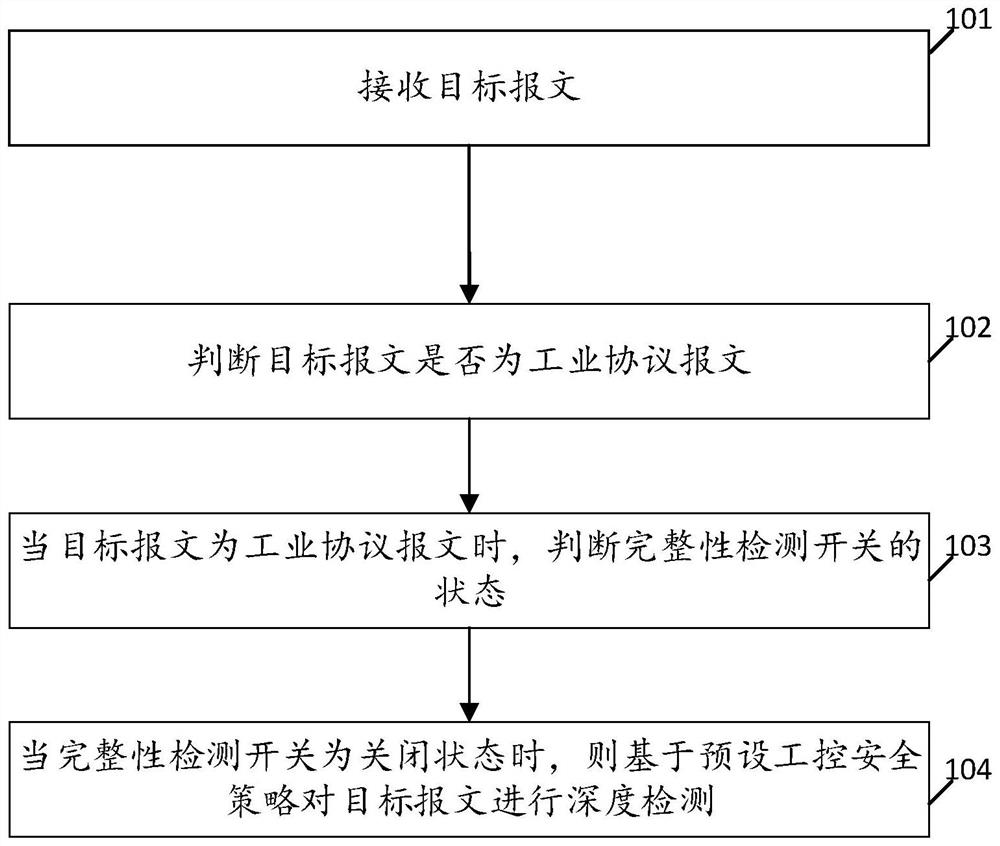
[0051] see figure 2 , figure 2 It is a schematic flowchart of an industrial protocol detection method disclosed in the embodiment of the present application, wherein the method in the embodiment of the present application is deployed in a mimic edge gateway in an industrial network in a bypass deployment mode. Such as figure 2 As shown, the method of the embodiment of the present application includes the following steps:
[0052] 101. Receive the target message;
[0053] 102. Determine whether the target message is an industrial protocol message;
[0054] 103. When the target message is an industrial protocol message, judge the state of the integrity detection switch;
[0055] 104. When the integrity detection switch is turned off, perform in-depth detection on the target message based on the preset industrial control security policy.
[0056] In some scenarios, the target message includes industrial protocol message and non-industrial protocol message, and it is only nec
Embodiment 2
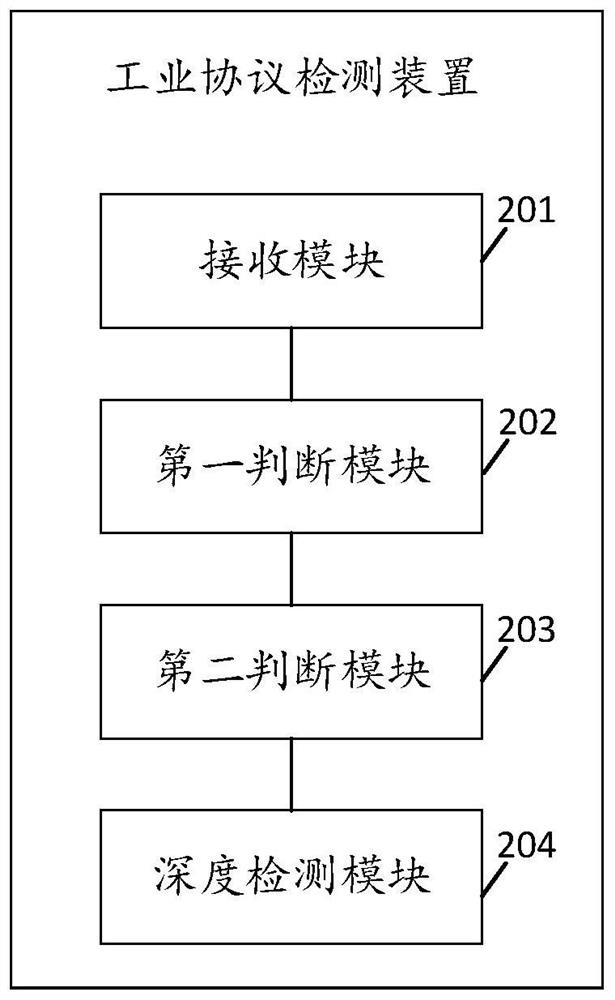
[0081] see image 3 , image 3 It is a schematic structural diagram of an industrial protocol detection device disclosed in an embodiment of the present application, wherein the device in the embodiment of the present application is deployed in a mimic edge gateway in an industrial network in a bypass deployment mode. Such as image 3 As shown, the device of the embodiment of the present application includes the following functional modules:
[0082] A receiving module 201, configured to receive a target message;
[0083] The first judging module 202 is used to judge whether the target message is an industrial protocol message;
[0084] The second judging module 203 is used to judge the state of the integrity detection switch when the target message is an industrial protocol message;
[0085] The deep detection module 204 is configured to perform deep detection on the target message based on the preset industrial control security policy when the integrity detection switch is
Embodiment 3
[0089] see Figure 4 , Figure 4 It is a schematic structural diagram of a computer device according to an embodiment of the present application. Such as Figure 4 As shown, the computer equipment of the embodiment of the present application includes:
[0090] a memory 302 storing executable program code;
[0091] a processor 301 coupled with a memory 302;
[0092] The processor 301 invokes the executable program code stored in the memory 302 to execute the industrial protocol detection method in Embodiment 1 of the present application.
[0093] By implementing the industrial protocol detection method, the computer equipment in the embodiment of the present application can, on the one hand, realize in-depth detection of messages in the industrial network without interrupting the equipment in the industrial network; , based on the status of the integrity detection switch, the integrity detection process of the message is skipped, and the deep detection of the message is direc
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap