Asymmetric key encryption method
An encryption method and asymmetric technology, applied to encryption devices with shift registers/memory, key distribution, can solve the problems of low data encryption, short key length, etc., to increase complexity, reduce time, increase Effects on Safety and Reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
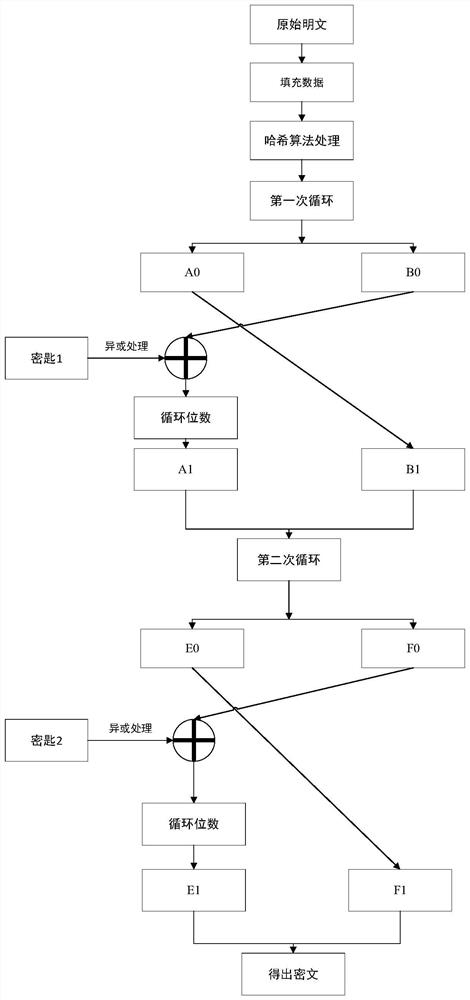
[0036] Embodiment 1: as figure 1 As shown, an asymmetric key encryption method, first divides the plaintext of any length into groups according to the byte length, each group is 256bit, divides 256bit into 2 groups according to 128bit; then divides the key into each group of 128bit, and uses The key processes the plaintext, and only cyclically encrypts the plaintext processed by the previous group. The number of cycles of the main cycle is M / 256*2, where M is the length of the original text after processing, and each cycle contains 256 / 128*2 = 4 subcycles.
[0037] The specific steps are:
[0038] Step1: Increase the amount of initially obtained data;
[0039] Take the remainder of the original plaintext length according to the byte length of 1024bit, and fill the plaintext. After filling, the length of the information is (1024*N+896)bit, fill the original plaintext length with 128bit, and the length of the processed information is 1024* (N+1)bit.
[0040] Step2: Data ini
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap