Method for realizing network security information tagging processing based on NLP
A network security and information labeling technology, applied in the field of network security information labeling processing based on NLP, can solve problems such as low accuracy, lack of relevance in the label system, and low efficiency of data organization, and achieve precise construction and solve manual screening inefficient effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
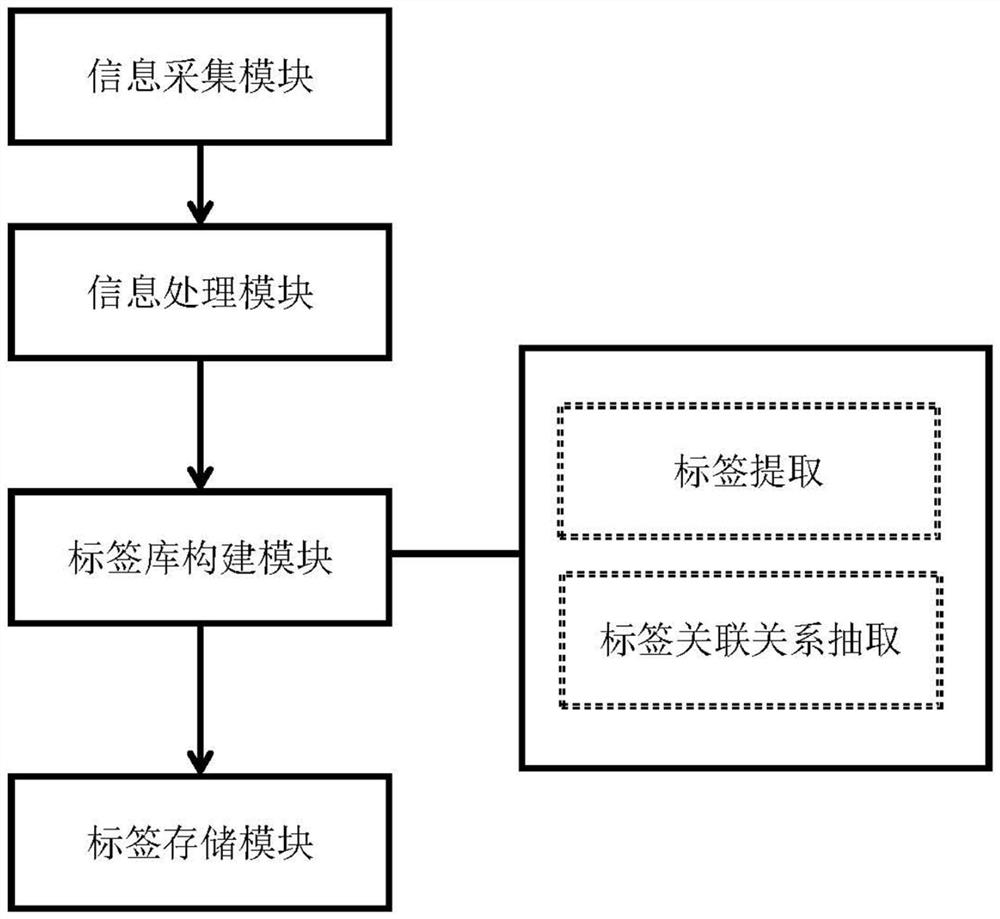
[0033] A method for tagging network security information based on NLP, comprising the following steps: S1. information collection; S2. information processing; S3. tag library construction; S4. tag storage.
[0034] In S1, the information collection module is used to collect network security industry information from official channels or third-party channels based on software technology and manual integration and entry. The information collected by the information collection module is divided into subject information databases of legal database, policy database, standard database, character database and product database. Software technology is used to collect external information resources, and the two data collection methods will be used comprehensively depending on the situation.
[0035] In S2, the information processing module is used to analyze and process the collected information data through data cleaning and attribute alignment technology to ensure the data quality and...
Embodiment 2
[0039]The difference between this embodiment and Embodiment 1 is that the tag library construction module in S3 utilizes the network security ontology to realize the construction of the tag library in the network security field. The network security ontology is constructed based on the analysis of the interrelationships between the six cross-domain label entity systems, which include the legal system, policy system, standard system, protection system, defense system, and guarantee system. The next level of the six major tag entity systems are domain tags, direction tags and application tags. Domain tags and direction tags determine the attribution of tag categories, while the application tag layer is more detailed and has a wide variety.
Embodiment 3
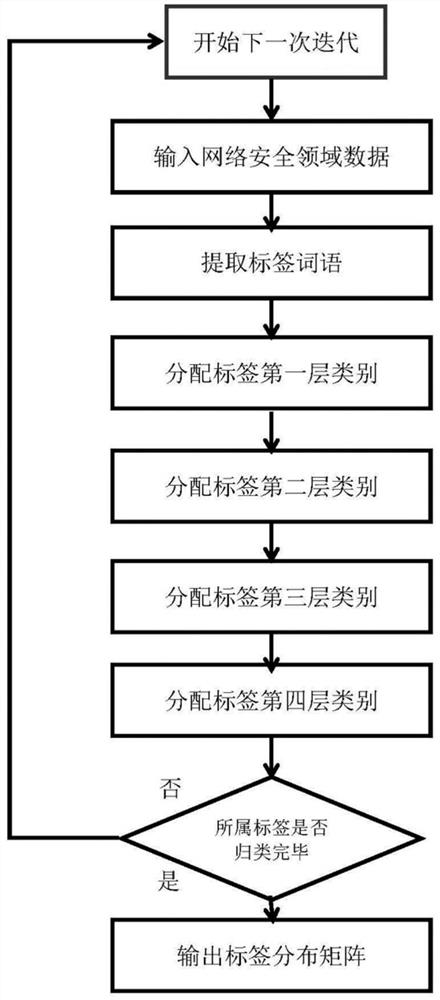
[0041] The difference between this embodiment and Embodiment 2 is that the network security domain tag library is designed and implemented in a bottom-up order, and the structure of numbers, graphs, and spectra is constructed to process network security industry information labeling. The tag library in the field of network security analyzes data from the perspectives of systems, people, and products, adopts cross-domain and multi-dimensional methods, and has a panoramic view of the network security ecology from multiple dimensions, striving to achieve the best information classification method.
[0042] The label library in the field of network security includes the first layer domain information database, the second layer domain label space map, and the spectrum formed by the six information systems in the third layer network security field.
[0043] Field information database According to the needs of network security ecological construction, combined with expert opinions, a ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap