Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
13 results about "Privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Device and method for protecting privacy
InactiveCN103501407AEffective occlusionImprove the effect of personal privacy protectionTelevision system detailsColor television detailsTransmittancePrivacy protection
The invention provides a device and method for protecting privacy, and relates to the field of intelligent equipment. The device comprises a recognizing unit and a privacy protecting unit. The recognizing unit is used for judging whether people or cameras or shooting behaviors exist in the surroundings. The privacy protecting unit is used for reducing the light transmittance when people or the cameras or the shooting behaviors exist in the surroundings. According to the device and method for protecting the privacy, whether people or the cameras or the shooting behaviors exist in the surroundings or not is judged and whether privacy violating risks exist in the surroundings or not is judged, when the judging result shows that people or the cameras or the shooting behaviors exist in the surroundings, the privacy protecting unit is triggered to reduce the light transmittance, and a person to be protected is effectively sheltered so that the whole or part of the body of the person to be protected can be prevented from being seen or shot, and the effect of protecting the individual privacy of the person to be protected is improved.
Owner:BEIJING ZHIGU RUI TUO TECH
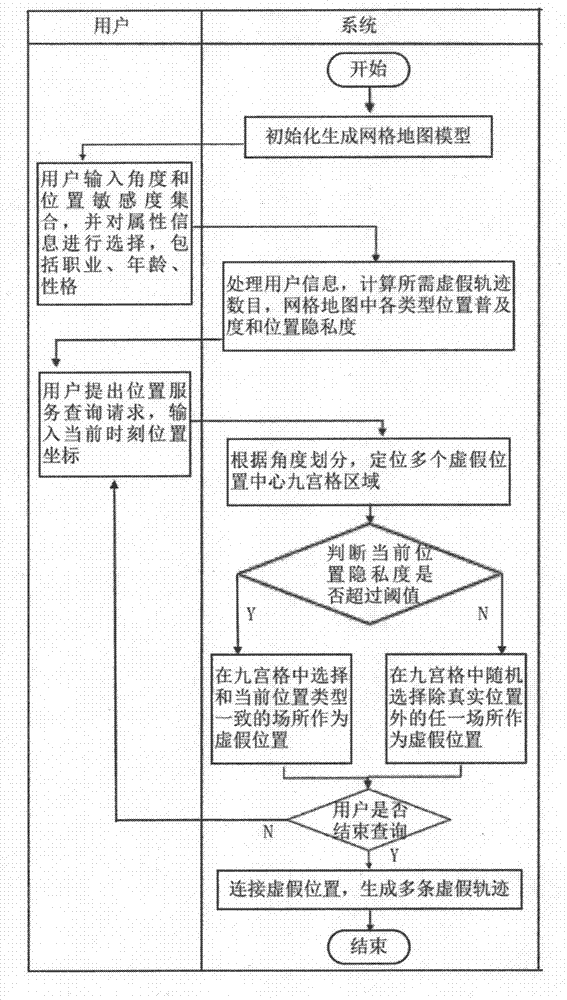
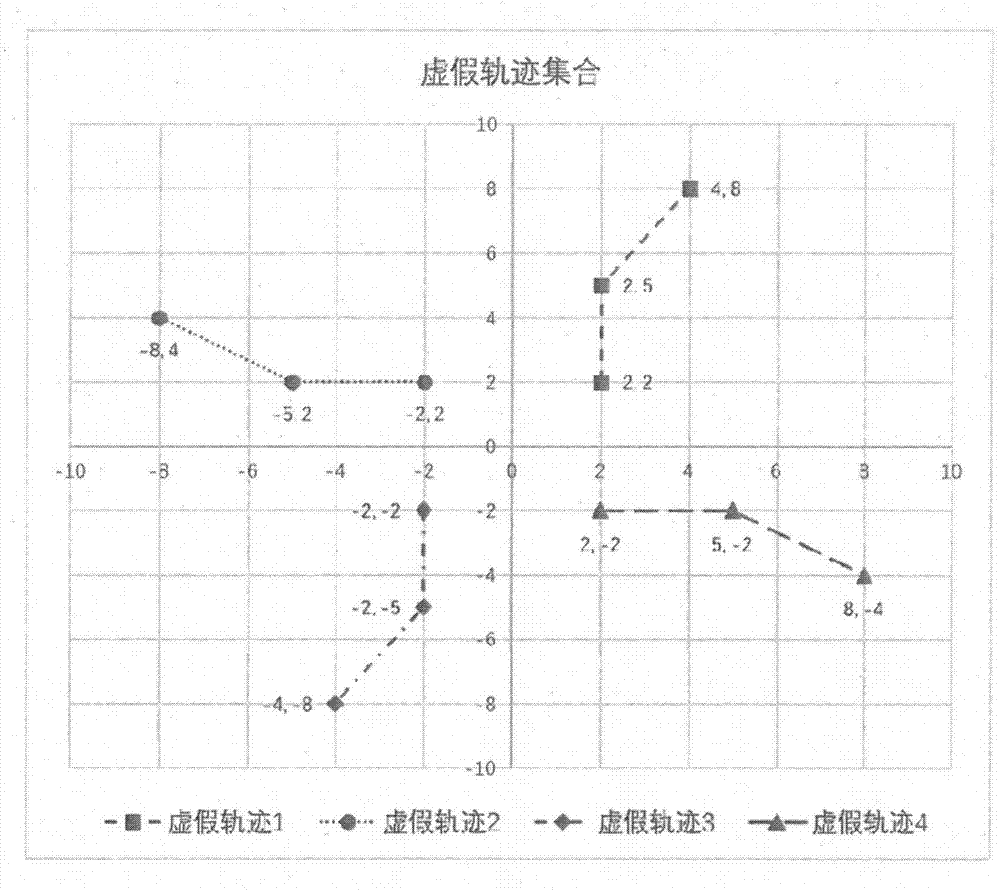
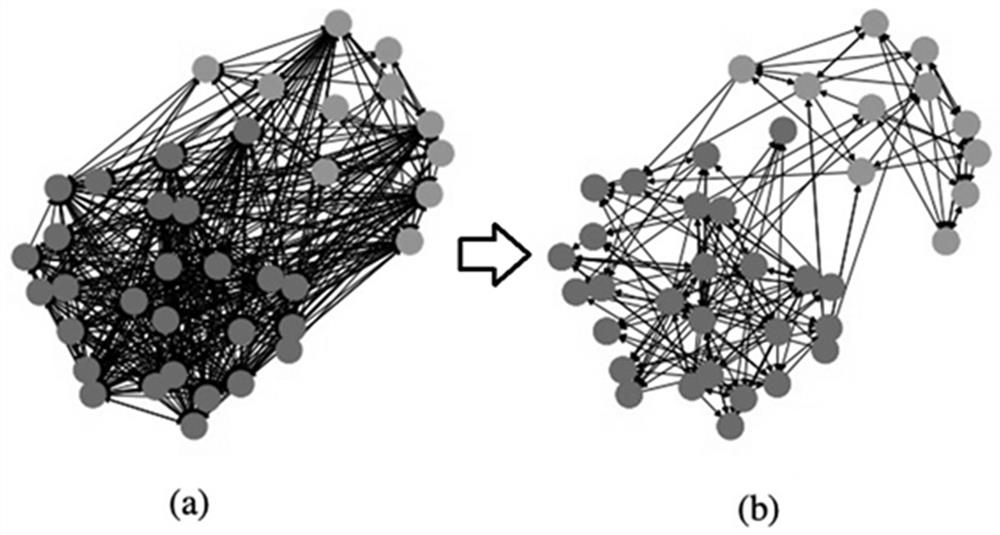
Track privacy protection algorithm based on angle division and position semantics
ActiveCN107480550AResist attackReduce leakageDigital data protectionSpecial data processing applicationsUser inputAlgorithm
Owner:上海东华大学科技园企业管理有限公司
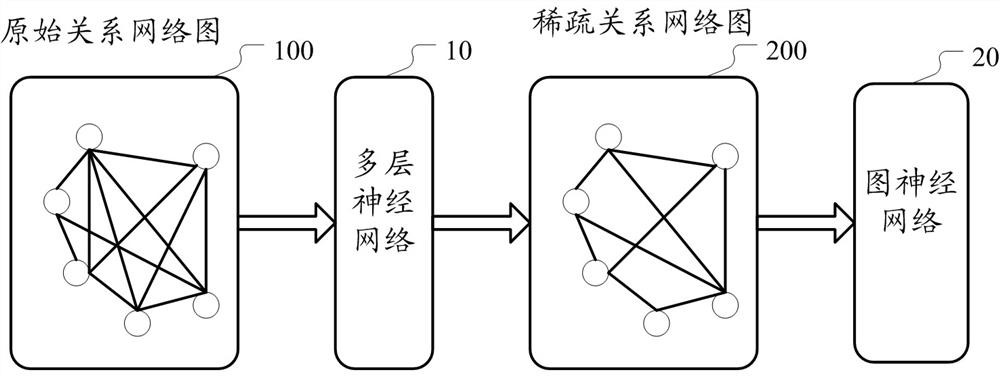
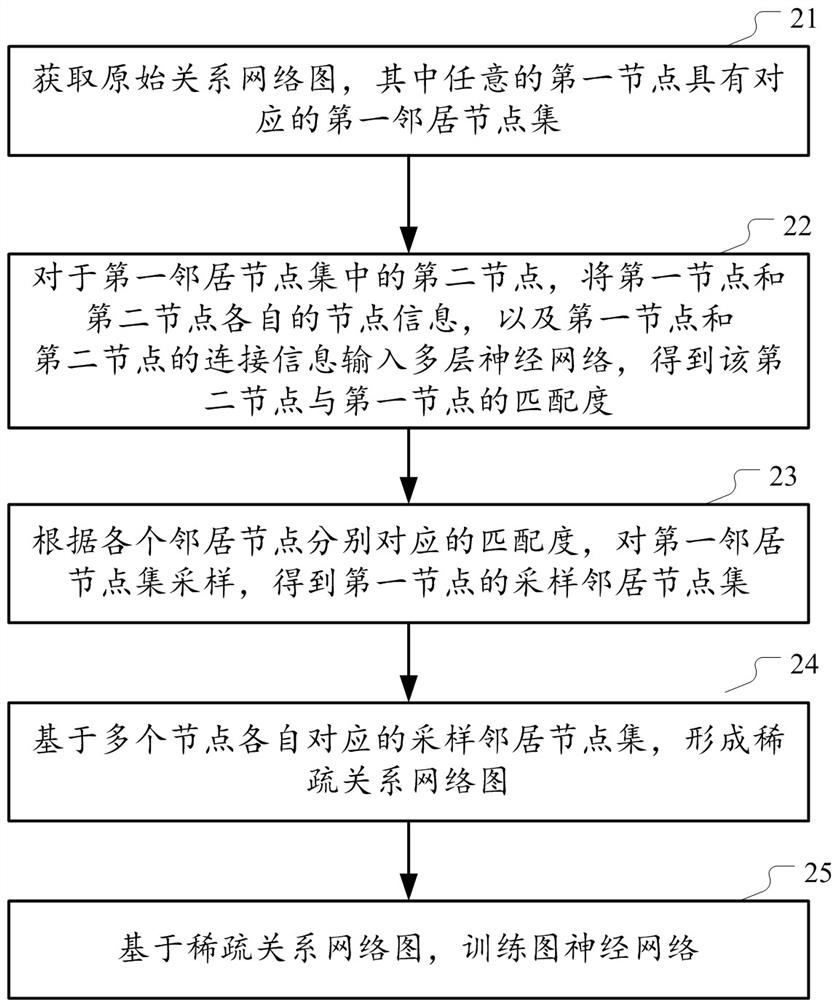
Method and device for training graph neural network based on privacy protection
ActiveCN112464292AProtect data privacyGuaranteed basic performanceDigital data protectionNeural architecturesPrivacy protectionEngineering
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
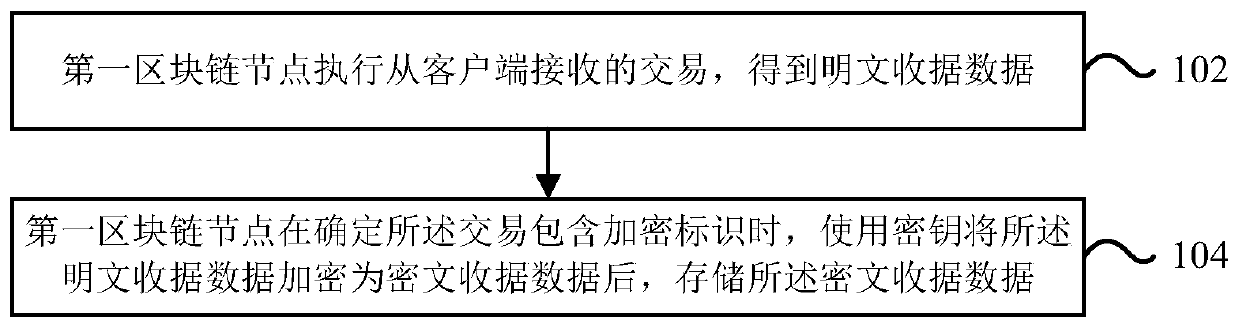
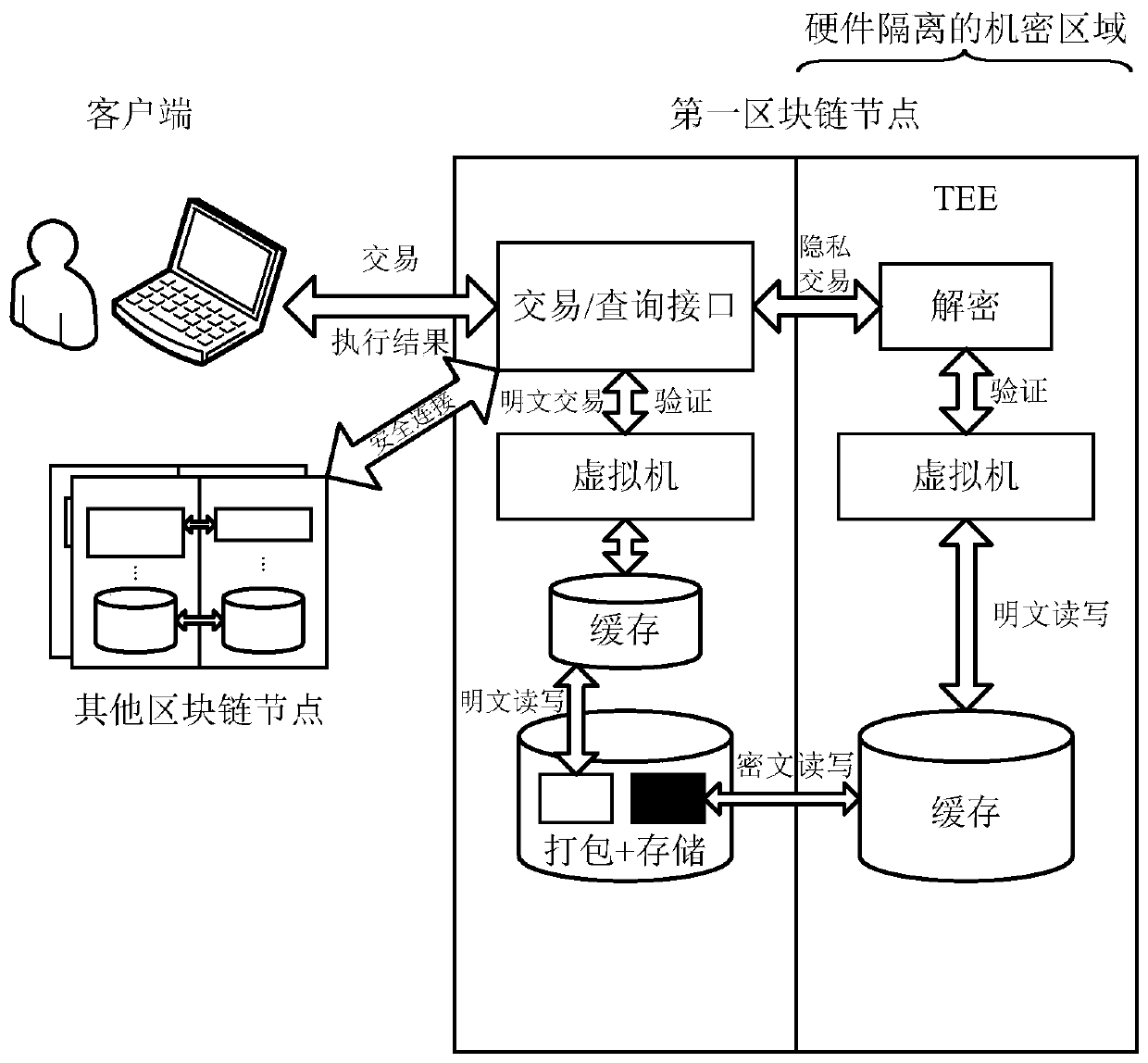
Method for realizing privacy protection in block chain, node and storage medium
One or more embodiments of the present specification provide a method for realizing privacy protection in a block chain, a node and a storage medium, the method comprising: a first block chain node executes a transaction received from a client to obtain plaintext receipt data; and when determining that the transaction is a private transaction, the first block chain node encrypts the plaintext receipt data into ciphertext receipt data by using a key, and then stores the ciphertext receipt data.
Owner:ADVANCED NEW TECH CO LTD
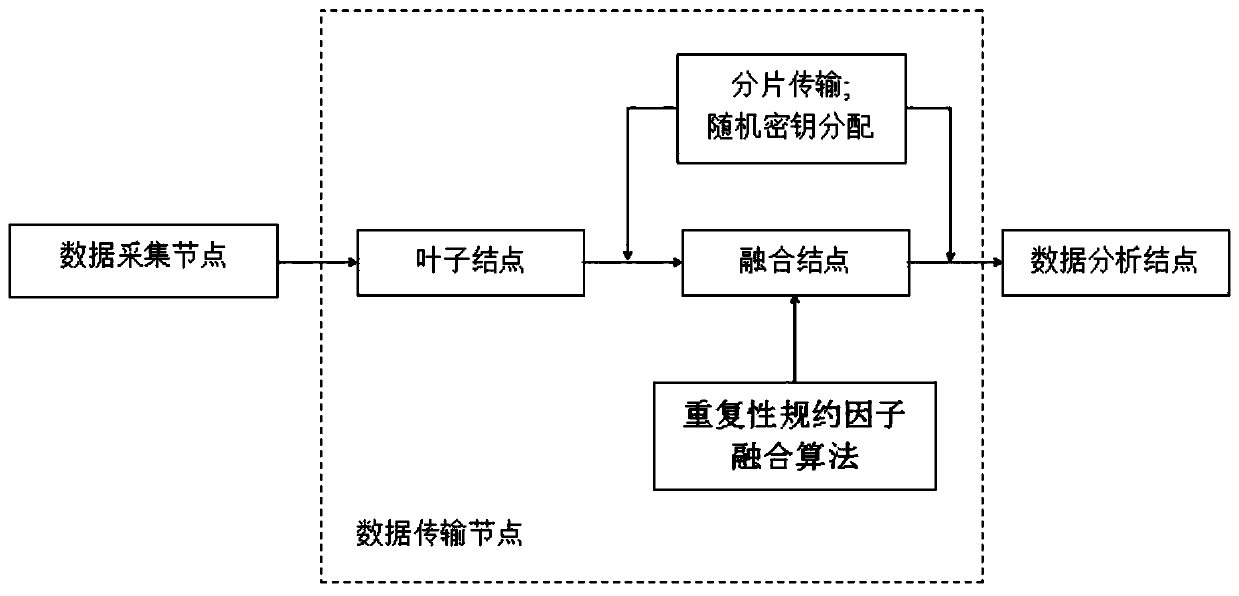
Data acquisition and analysis system based on wireless body area network and low-energy-consumption data fusion privacy protection algorithm
InactiveCN110545282AReduce data trafficImprove privacy protectionKey distribution for secure communicationSecurity arrangementStructure of Management InformationPrivacy protection
Owner:CHINA JILIANG UNIV
Systems and methods for traffic monitoring with improved privacy protections
PendingUS20220100894A1Detection of traffic movementDigital data protectionUnique identifierPrivacy protection
Owner:REKOR SYST INC
Block chain assisted privacy protection image retrieval method
PendingCN114579787ASolve the problem of integrity verificationImprove efficiencyStill image data indexingDigital data protectionCiphertextPrivacy protection
The invention discloses a blockchain-assisted privacy protection image retrieval method, which comprises the following steps: firstly, an image owner extracts image features by using a CNN model, then encrypts an image and the features by using an SM4 algorithm and a secure kNN algorithm, and uploads a ciphertext image to a cloud server; then, the image owner calculates the hash of the ciphertext image and generates a Merkle hash tree, then an index table of encryption features is constructed by using an LSH algorithm, and the index table and the Merkle tree are uploaded to an alliance chain; and finally, the user uploads the encryption feature of the query image to the alliance chain, retrieves the IDs of the first k images similar to the image, and returns the k IDs to the cloud, the cloud sends the corresponding image to the user, and the user decrypts the image to obtain a plaintext image. The advanced block chain technology and the cryptography technology are adopted, the accuracy of the retrieval result can be guaranteed, and the integrity of the image data stored in the cloud can be verified; meanwhile, the image retrieval problem in the multi-cloud environment is solved, and the efficiency of the retrieval scheme is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
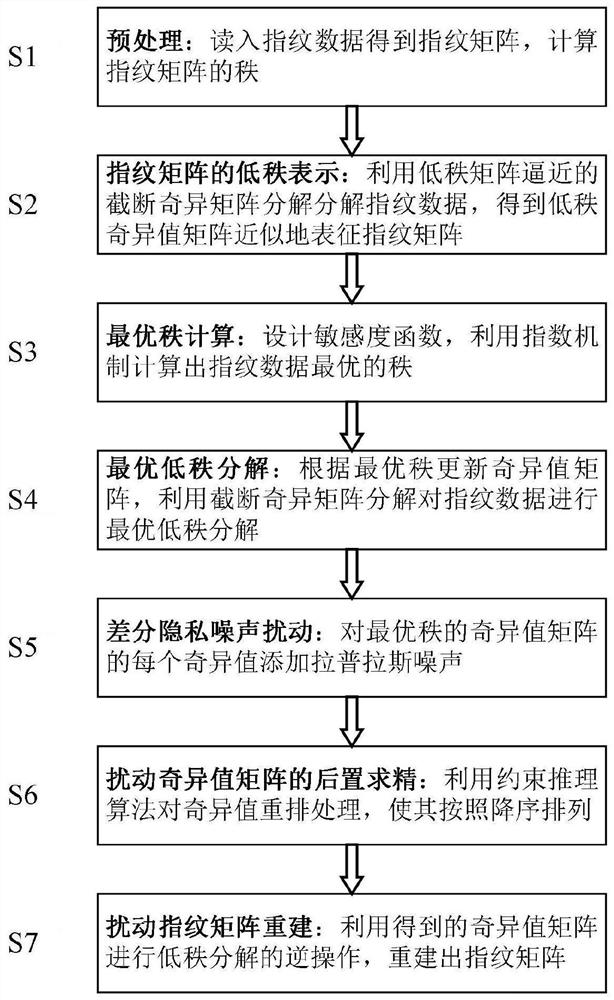
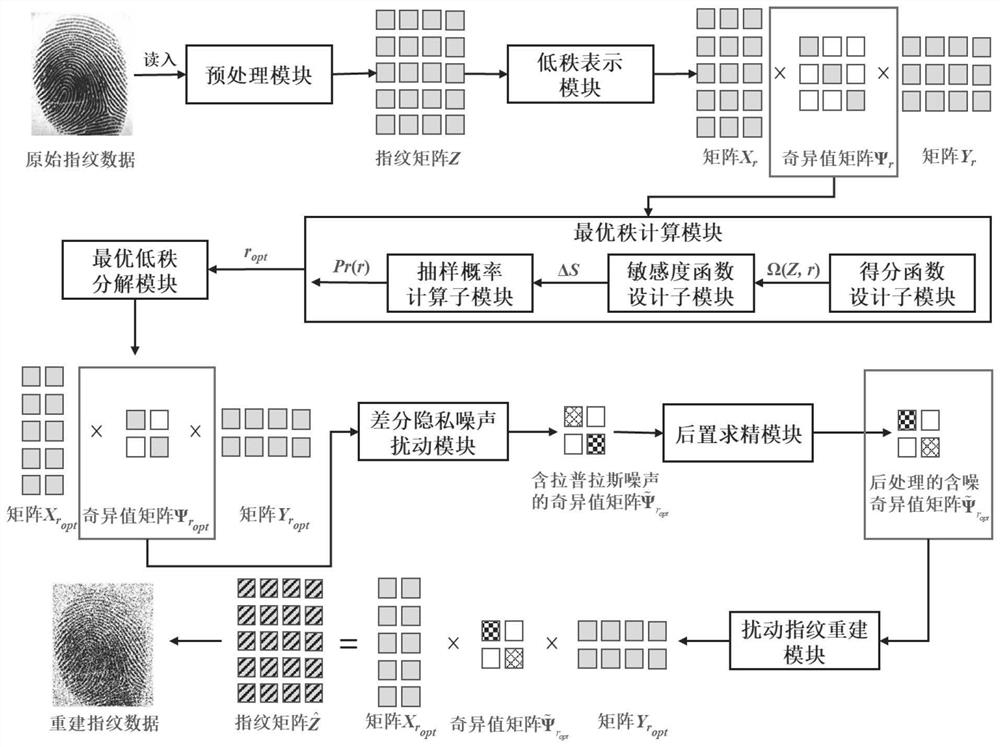
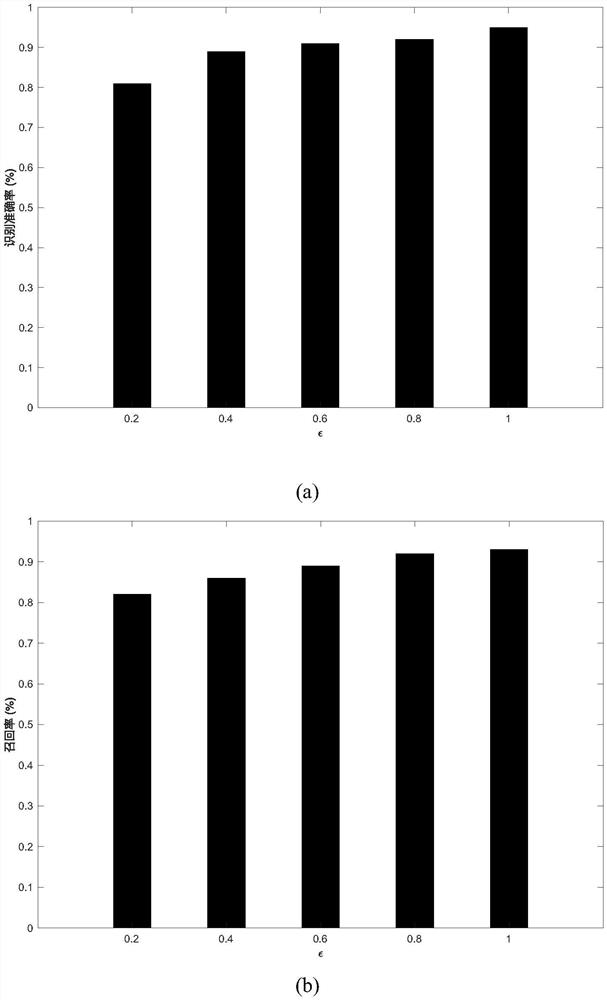
Privacy protection method and system for fingerprint authentication
PendingCN114880700ADigital data protectionDigital data authenticationPrivacy protectionSingular matrix
Owner:HUAZHONG NORMAL UNIV
Computer privacy protection device for assisting software development
InactiveCN112487512AProtection securitySimple structureInternal/peripheral component protectionSoftware engineeringPrivacy protection
The invention relates to the technical field of basic software development, and discloses a computer privacy protection device for assisting software development, which comprises a shell, the shell isslidably connected with a restart button, the right side of the restart button is provided with a power supply button, and the bottom of the power supply button is fixedly connected with a trigger rod; a limiting groove is formed in the surface of the trigger rod, a matching groove is formed in the bottom of the trigger rod, a horizontal rod is arranged on the lower side of the power button, anda clamping groove is formed in the surface of the horizontal rod. According to the computer privacy protection device for assisting software development, through cooperative use of the restart button,the power button, the touch button, the camouflage pressing plate, the touch rod and the like, when other people start a computer by using a normal method, a display of the computer cannot normally display, so that other people cannot operate the computer, therefore, the effect of protecting the safety of data in the computer is achieved.
Owner:HANGZHOU XUZHAN ROBOT TECH CO LTD
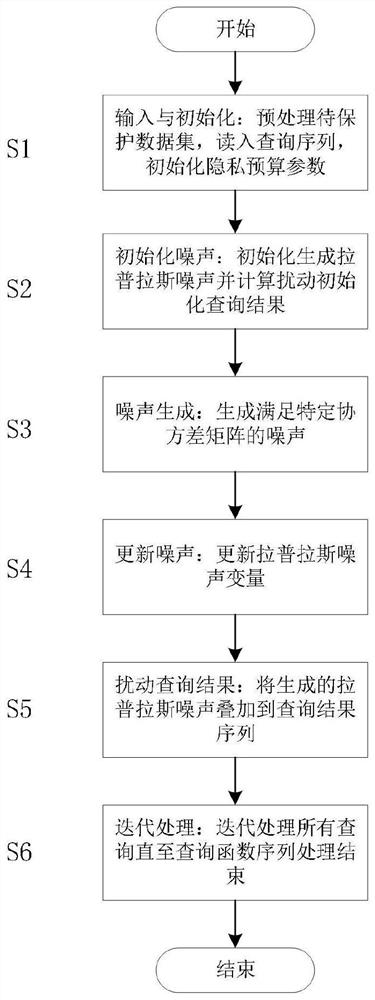
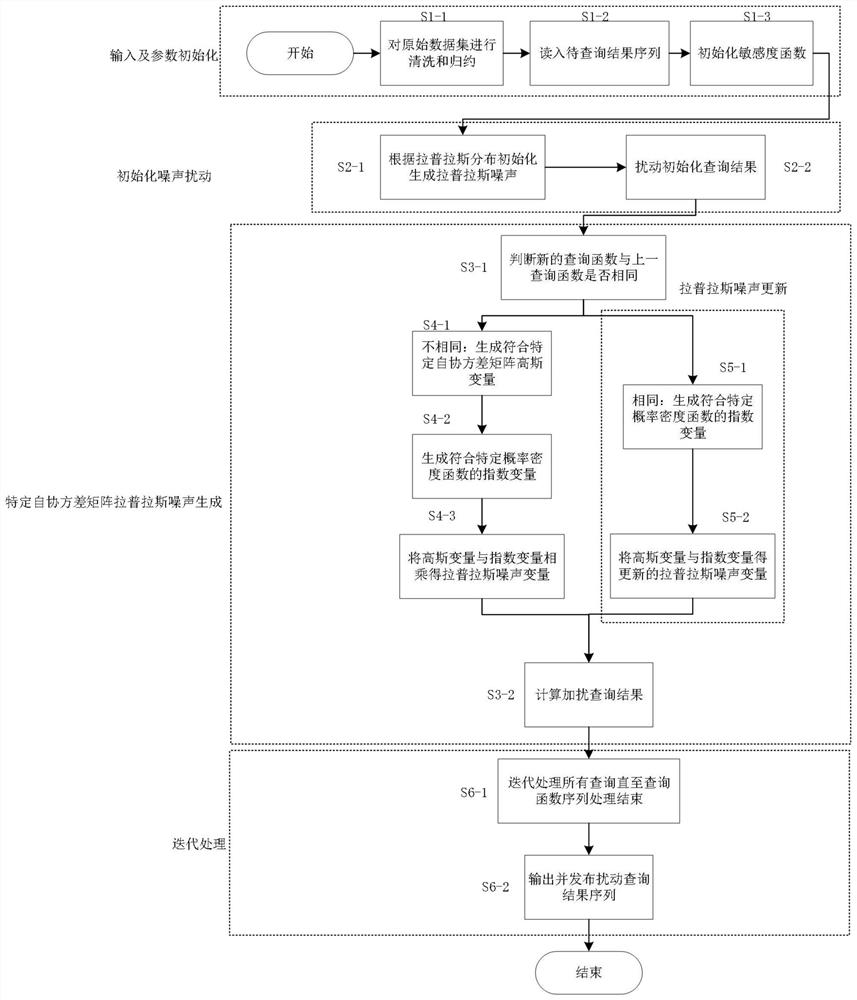
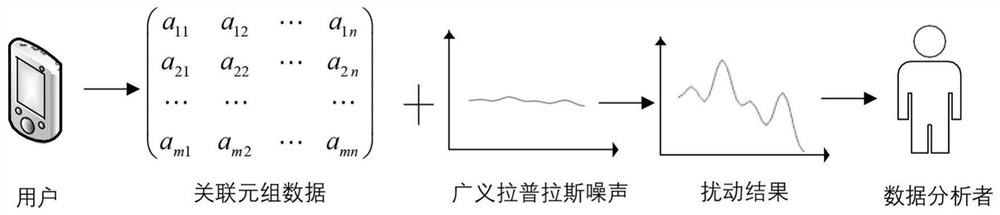
Differential privacy release method and system for associated tuple data
ActiveCN112487471ADigital data information retrievalDigital data protectionPrivacy protectionEngineering
Owner:CHONGQING UNIV OF POSTS & TELECOMM
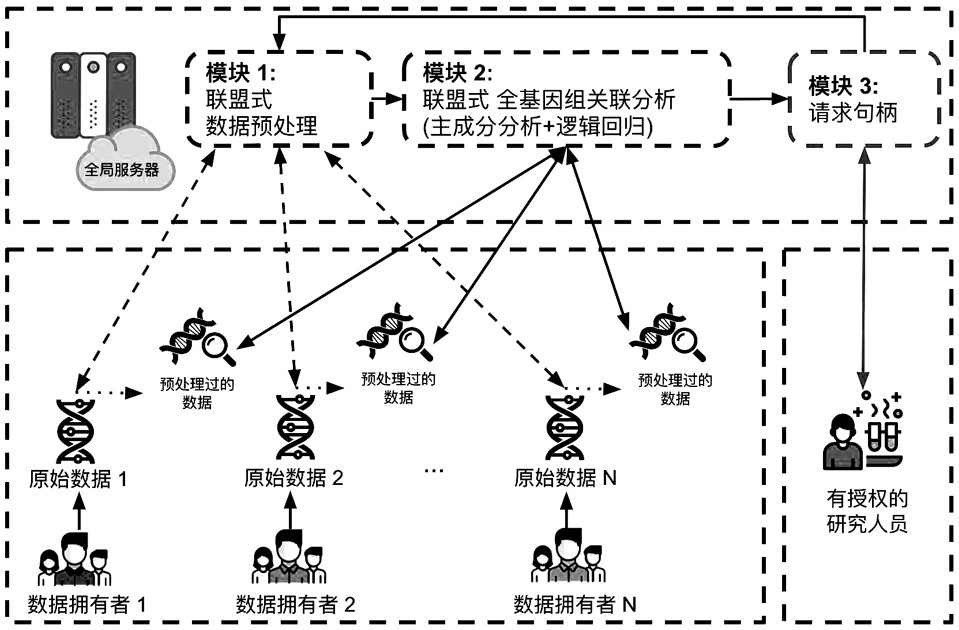
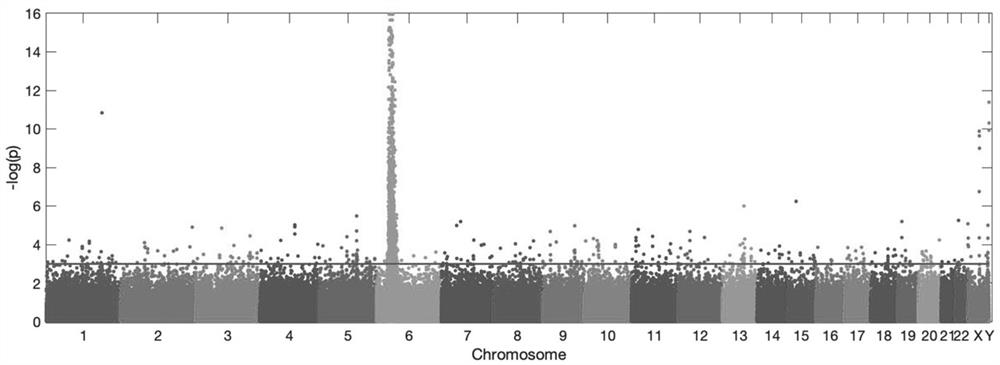
Privacy protection-based alliance learning system and method for realizing whole genome association analysis
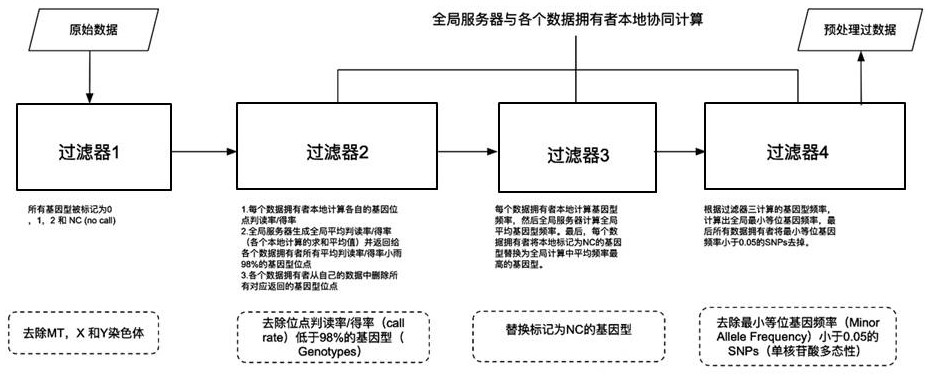
PendingCN113517027ARealize privacy protectionPrevent leakageBiostatisticsDigital data protectionWhole Genome Association AnalysisOriginal data
Owner:杭州锘崴信息科技有限公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap