Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
19 results about "Authentication system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication Systems aid the process of verifying the legitimacy of data, most often data used by people attempting to access a system.
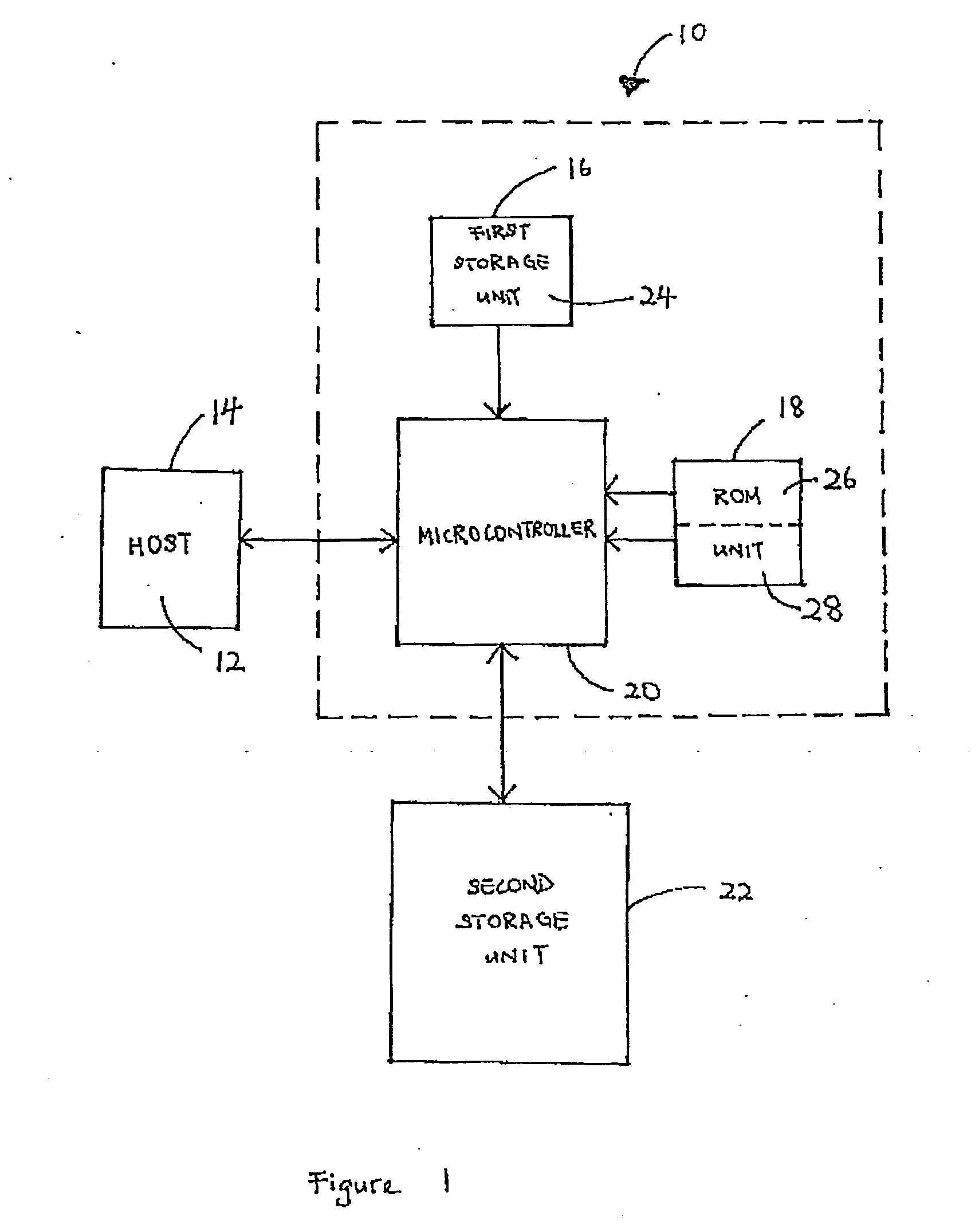
Authentication system and method
InactiveUS20090193264A1Digital data authenticationCoded identity card or credit card actuationAuthentication systemStrong authentication
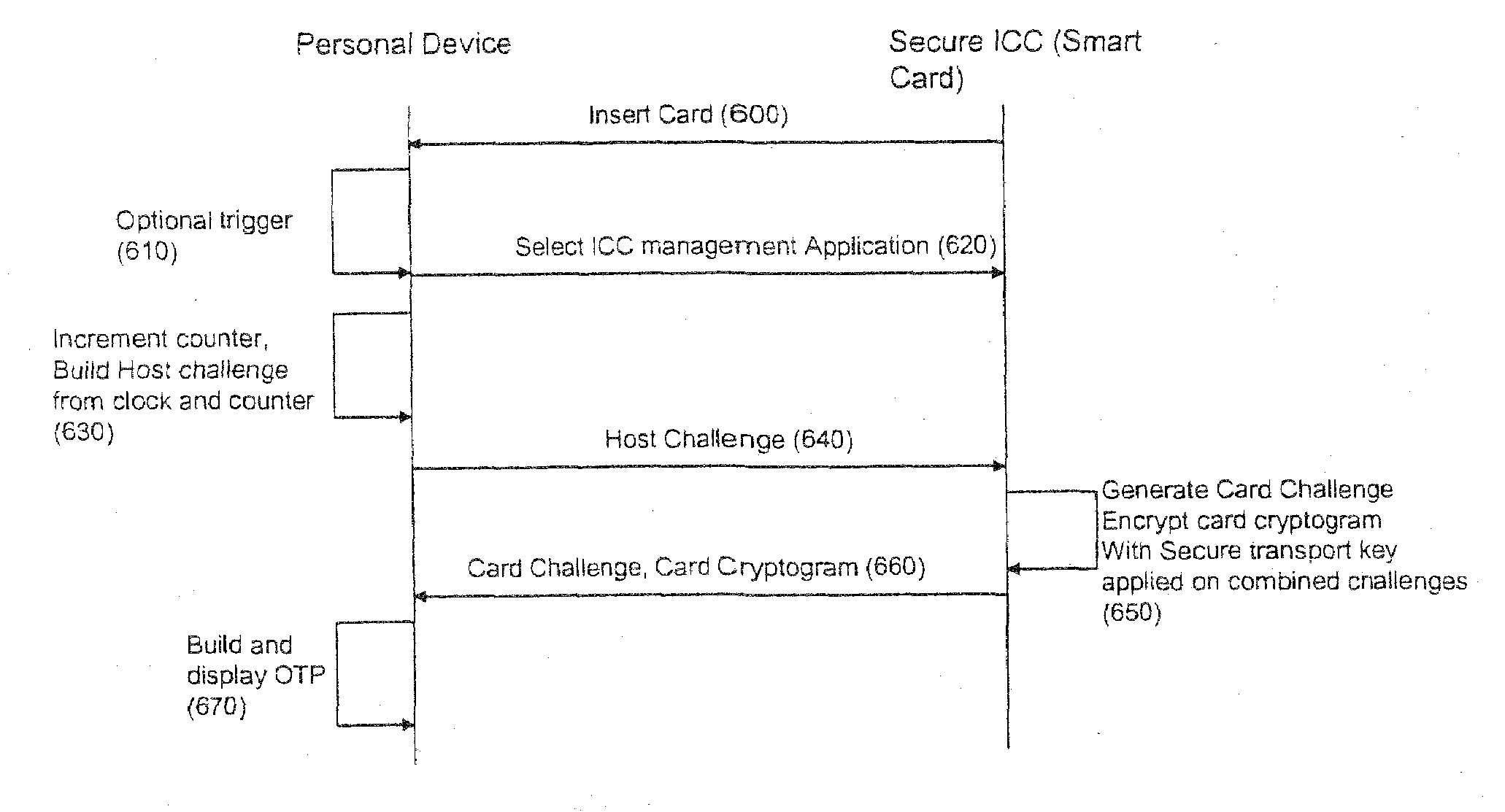
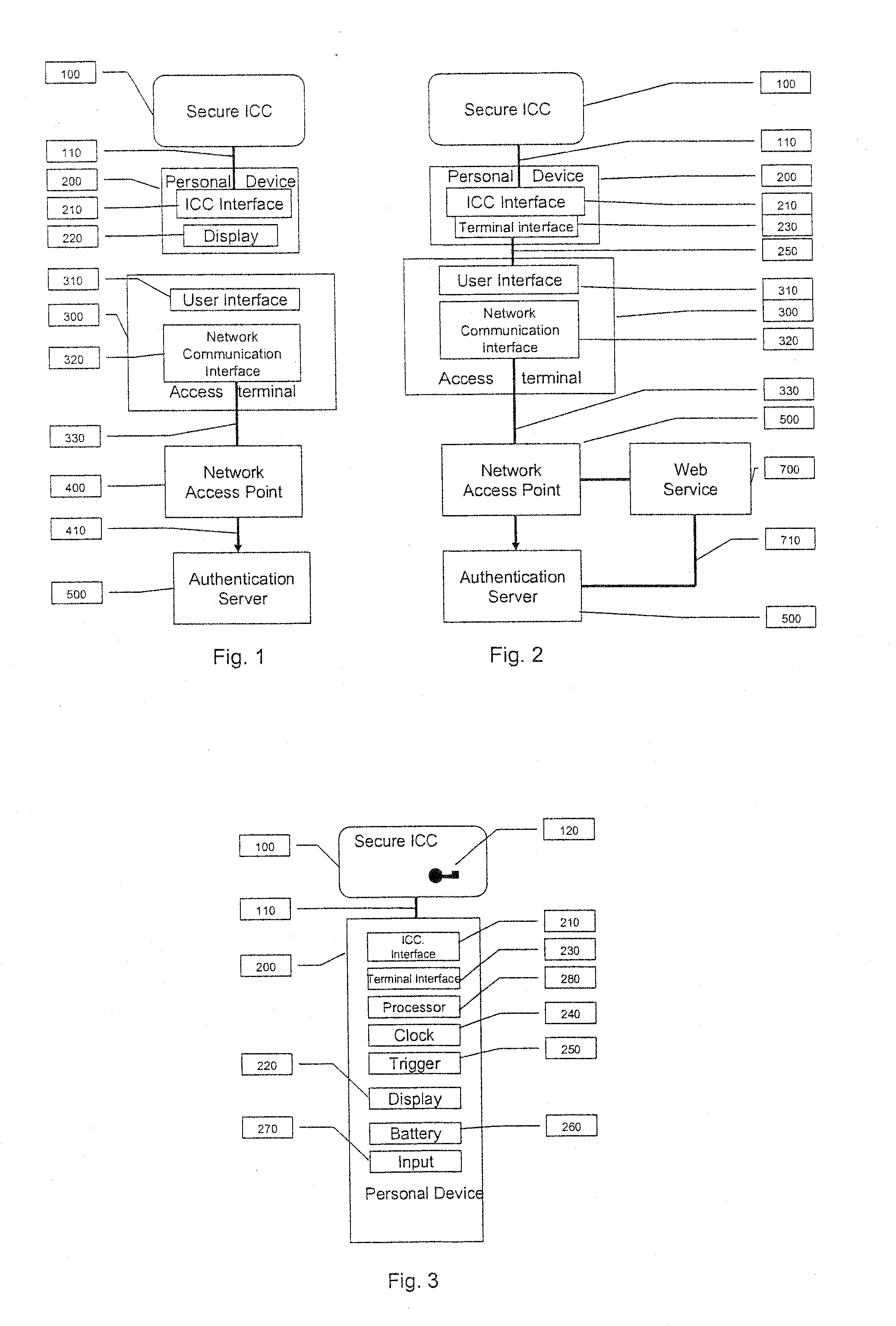
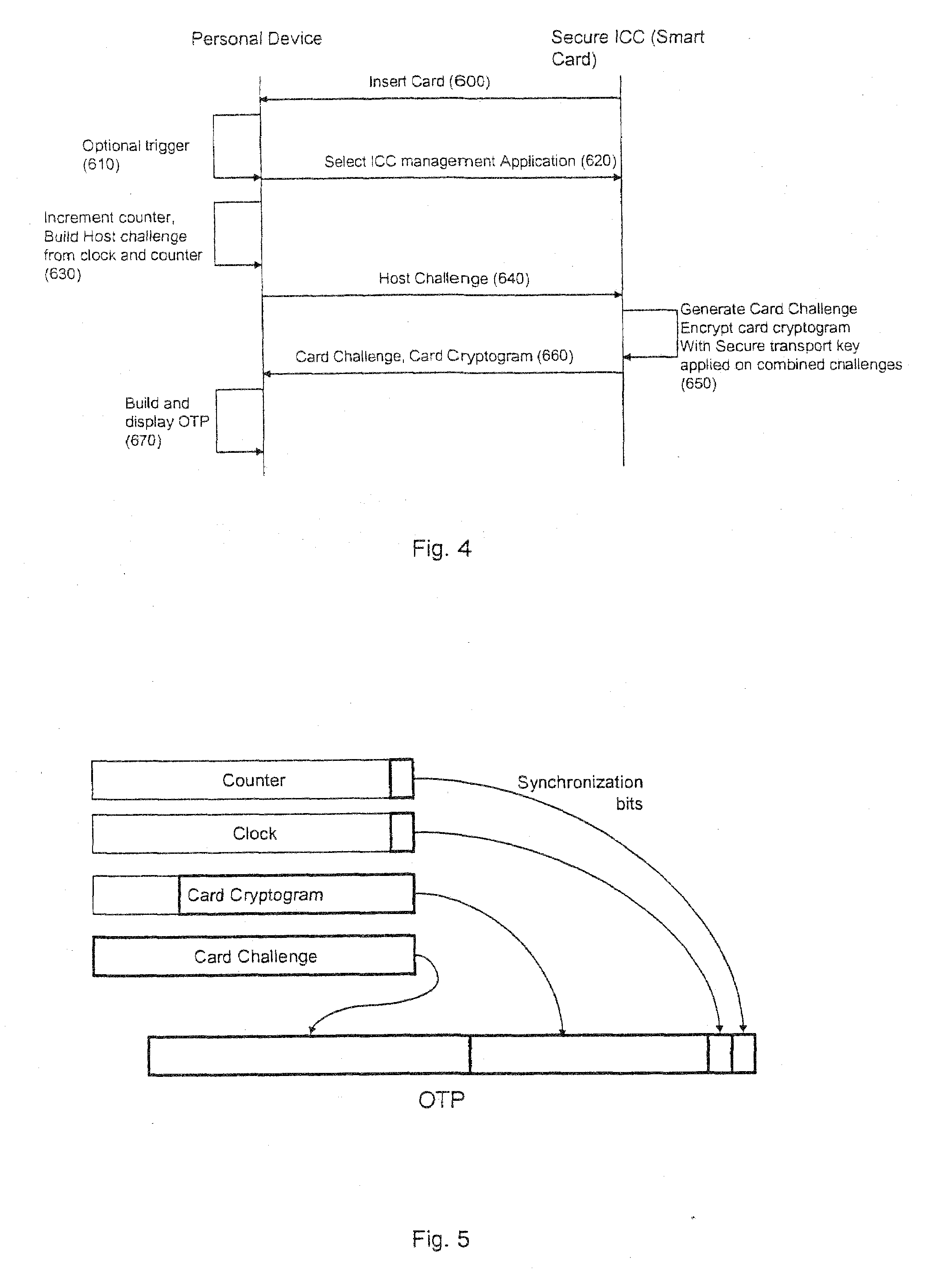
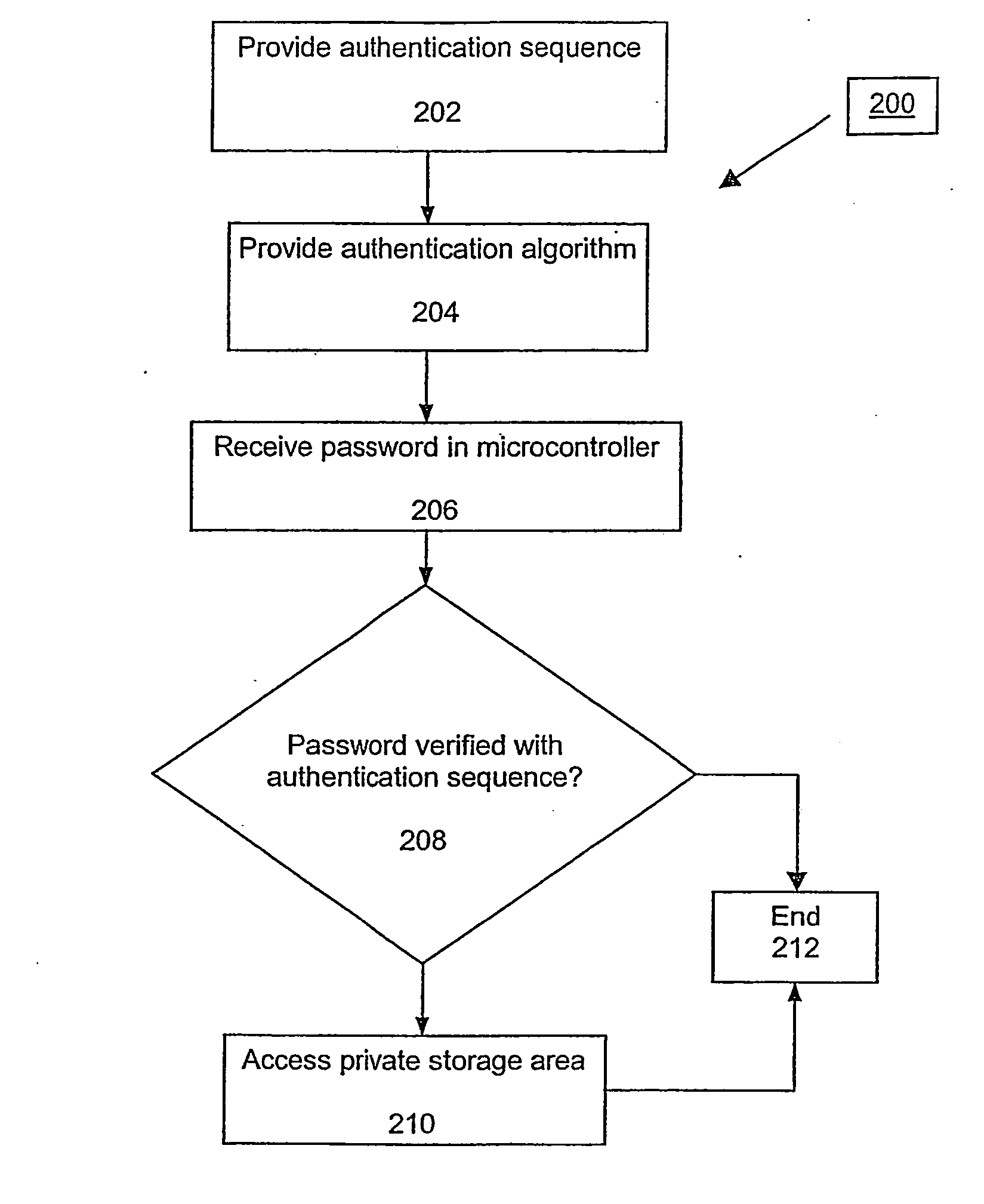
A strong authentication method and system using a Secure ICC component coupled with a Personal device, and relying on the existing cryptographic protocols and keys for managing the secure ICC to generate One-Time-Passwords when the necessary authentication keys or cryptographic protocols are not already present in the Secure ICC configuration for that purpose.
Owner:ACTIVIDENTITY
Digital certificate safety lock device and digital certificate authentication system and method
InactiveCN102255730AImprove general performanceImprove applicabilityUser identity/authority verificationMicrocontrollerTablet computer
The invention relates to a digital certificate safety lock device and a digital certificate authentication system and method. The digital certificate safety lock device comprises a universal encryption and digital signature microcontroller, an audio plug and a first modulation and demodulation module, wherein the universal encryption and digital signature microcontroller is provided with an encryption and digital signature module and a storage for storing a digital certificate, a key of the digital certificate and encryption and decryption algorithms; and the first modulation and demodulation module is used for modulating data information from the encryption and digital signature module for transmitting through an MIC (Microphone) pole of the audio plug, demodulating a signal received from a first sound channel pole of the audio plug and transmitting the demodulated signal to the encryption and digital signature module. The digital certificate safety lock device is provided with a universal audio interface plug which has high university and adaptability and can support communication terminals such as mobile phones, tablet computers, PDAs (Personal Digital Assistants) or PCs (Personal Computers) and the like, with audio interfaces. Due to the functions of independent hardware signature, digital certificate encryption and the like, the security of application logon and transactions of Internet banks or enterprises can be ensured to the maximum extent.
Owner:吴沙林 +1
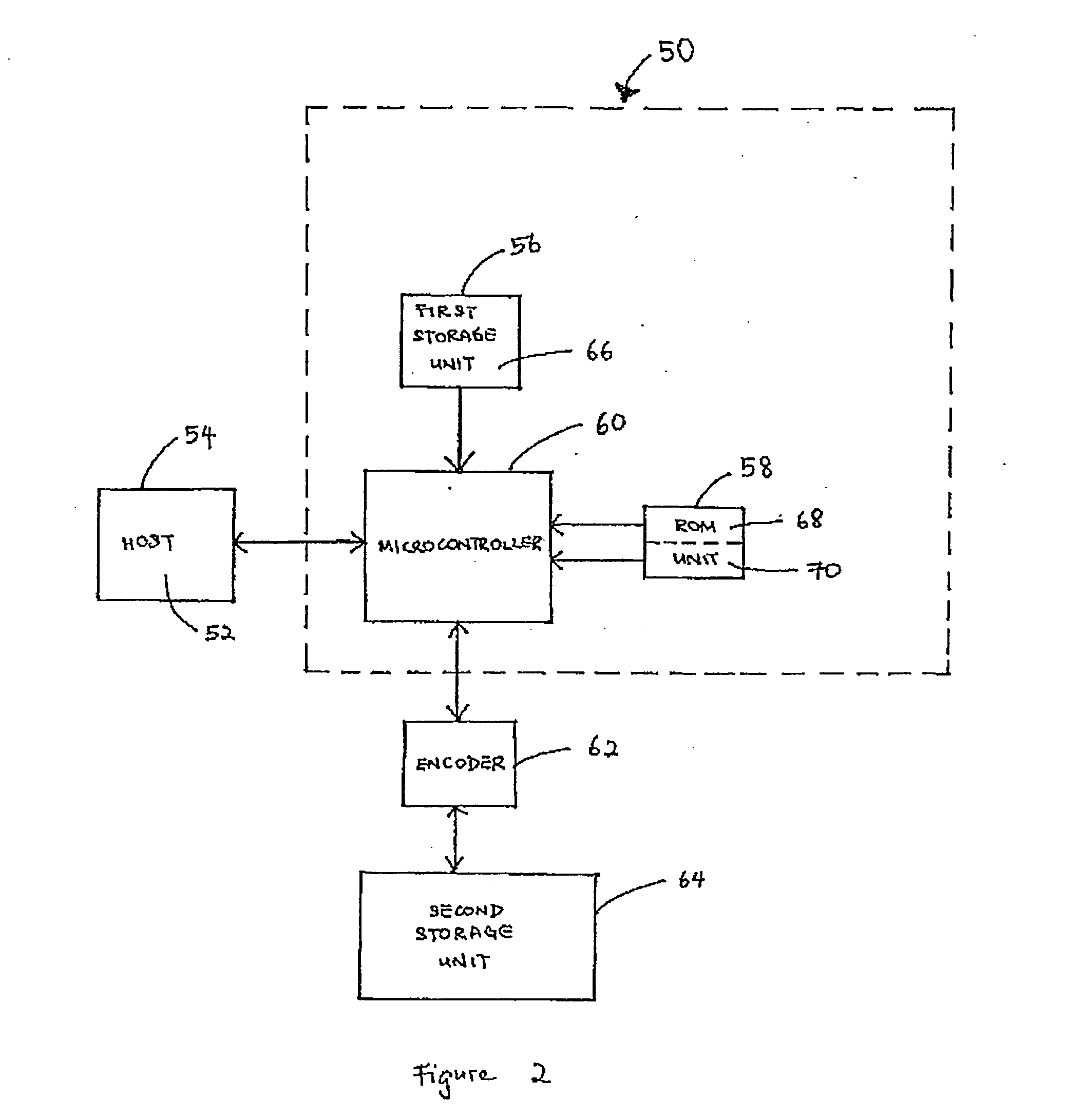
System and method for authentication
ActiveUS20050081064A1Digital data processing detailsUser identity/authority verificationAuthentication systemRead-only memory
Owner:TREK 2000 INT
Authentication system for mobile terminal having electronic money function
InactiveUS20060160525A1Reduce usageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPasswordComputer terminal
Owner:FUJIFILM CORP
Authentication system and method for embedded applets
ActiveUS20140325627A1Avoiding security pitfallEliminate needDigital data processing detailsMultiple digital computer combinationsUser deviceInternet privacy
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Safety authentication method and system for wireless network
Owner:HUAZHONG UNIV OF SCI & TECH
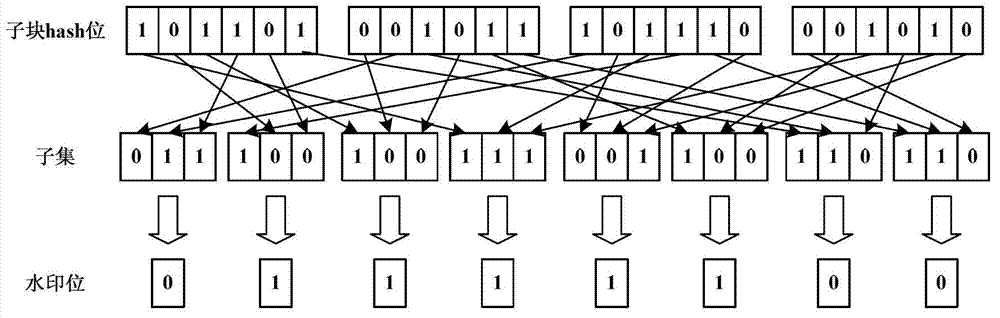
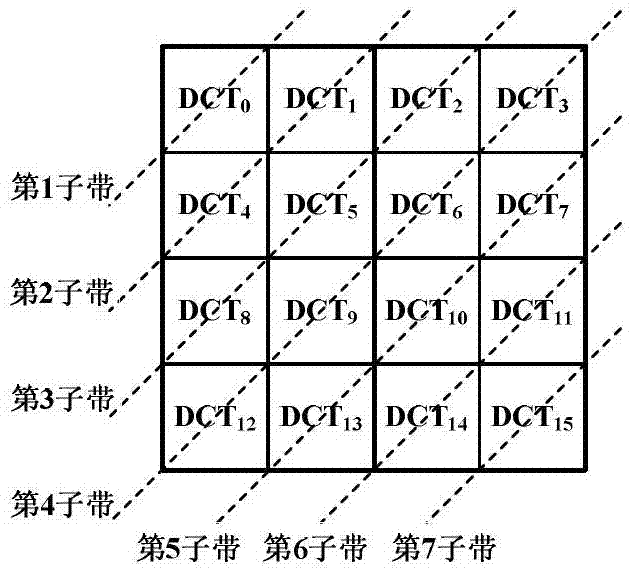
H.264 video integrality authentication method
InactiveCN102857831ATelevision systemsDigital video signal modificationAuthentication systemLarge capacity
Owner:HEFEI UNIV OF TECH
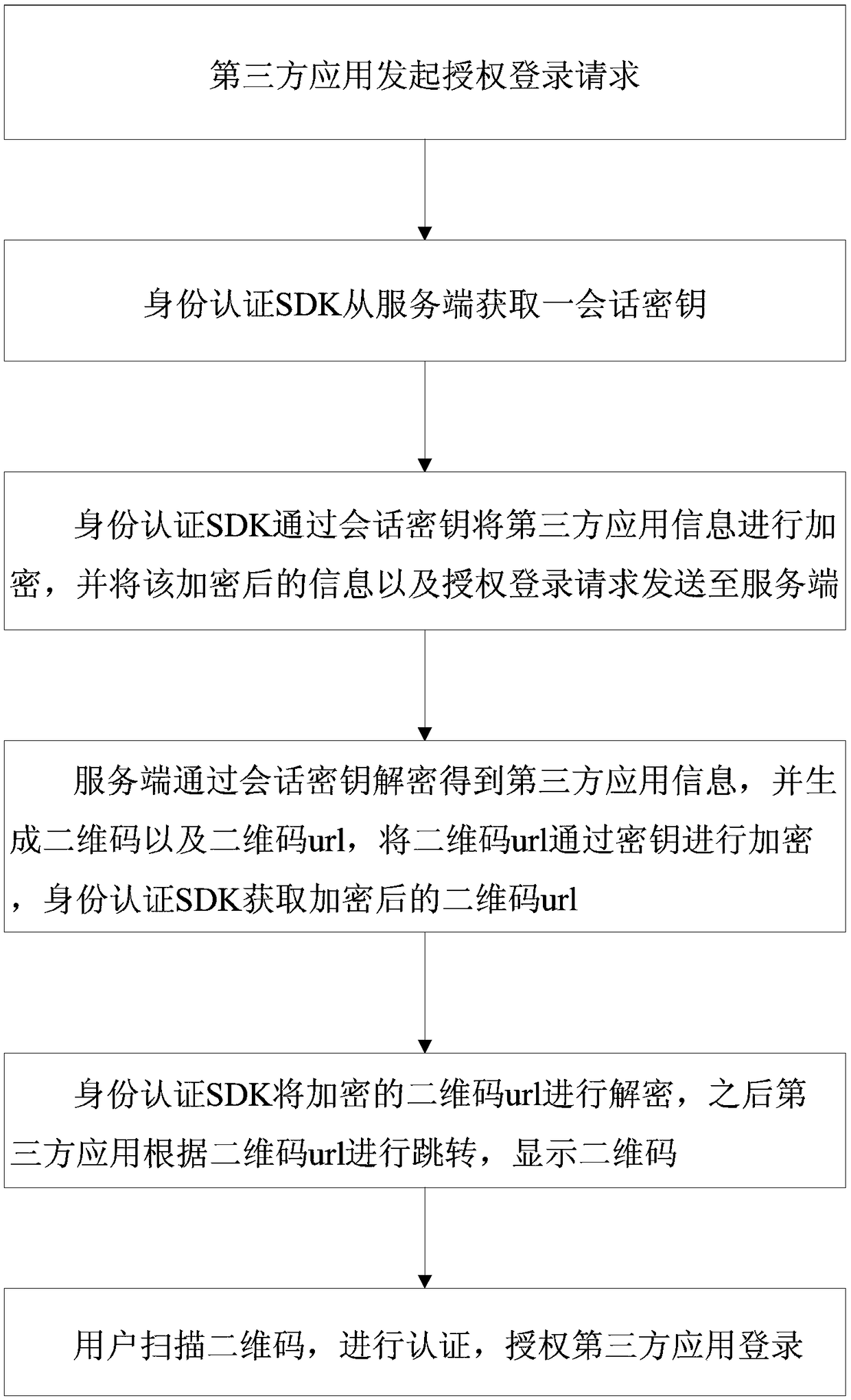
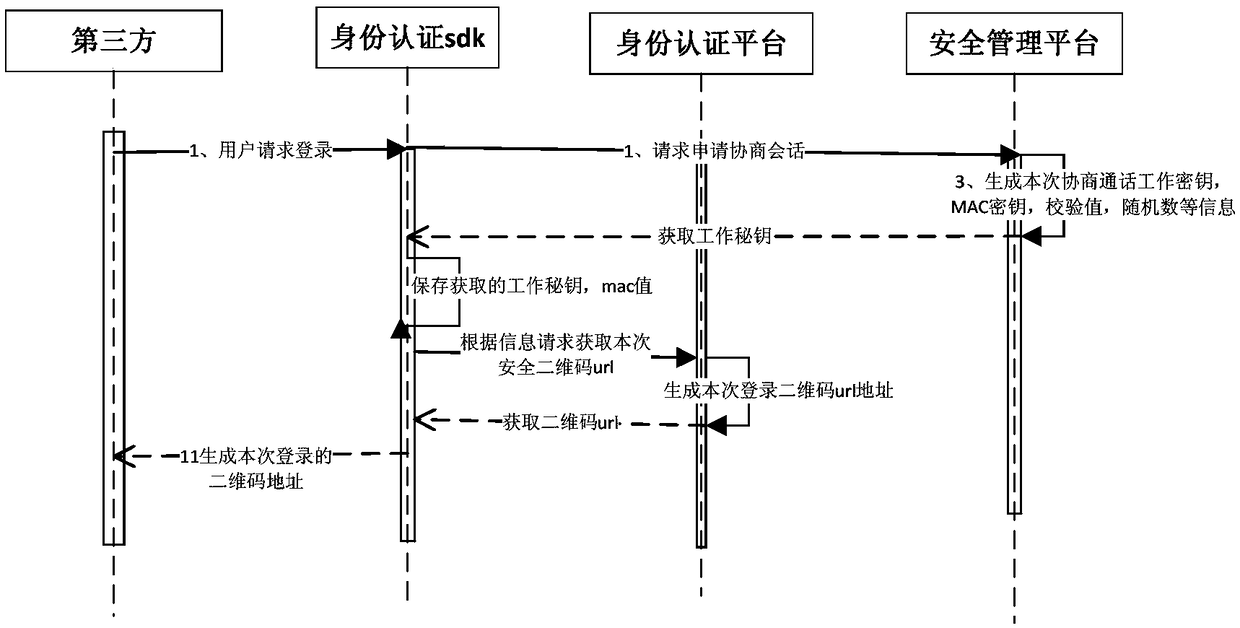
Digital identity authentication method and system based on secure two-dimensional code
Owner:新大陆(福建)公共服务有限公司
Authentication system and method using flash of smart mobile
ActiveUS20180262908A1Improve securityImprove stabilityClose-range type systemsSubstation equipmentPasswordMobile device
It is capable of authentication by transmitting through light emitted from a flash of a smart mobile according to foregoing solution of the problem, security and stability can be improved in comparison with other authentication systems such as an ID, a password and a public authentication which are necessary to a bank task, a personal authentication, an identity authentication and a transaction remittance. And, even if the smart mobile is lost or a stranger acquiring this are misappropriating, cryptography such as patterns cannot be solved thereby it is not available. Further, carrying is easy to use anywhere regardless of the place because the transaction is available using a flash equipped to the smart mobile.
Owner:B PLAT LLC
Authentication system and authentication method based on central node
Owner:ZHEJIANG QUANTUM TECH CO LTD
Multimedia data safety monitoring device, receiving terminal, authentication method and system thereof
ActiveCN102457518AEasy to judgeAvoid enteringData switching networksComputer hardwareContent security
The invention relates to the multimedia data communication technology field and provides a multimedia data safety monitoring device, a receiving terminal, a multimedia data authentication method and a system thereof. The authentication system comprises: a multimedia data safety monitoring device and a multimedia data receiving terminal, wherein the multimedia data safety monitoring device is used to acquire multimedia data, carry out safety authentication to the multimedia data and stores authentication result information in a safety checking code database; the multimedia data receiving terminal is used to receive the multimedia data, using a same method which the multimedia data safety monitoring device used to carry out the safety authentication to the multimedia data and feed back the safety authentication result information to the multimedia data safety monitoring device. The multimedia data safety monitoring device carries out comparison authentication to the received safety authentication result information and the corresponding safety authentication result information stored in the safety checking code database. If the two are matched, the authentication is passed and the multimedia data receiving terminal decodes and plays. A technical scheme is easy to be realized. Contents are safe and a definition is simple and strictness. Security is high. Implementation and management costs are low.
Owner:CHANGSHA DILU DIGITAL TECH
Systems and methods for material authentication
ActiveUS20080230719A1Efficient detectionPaper-money testing devicesFluorescence/phosphorescenceAuthentication systemEngineering
Owner:XEROX CORP
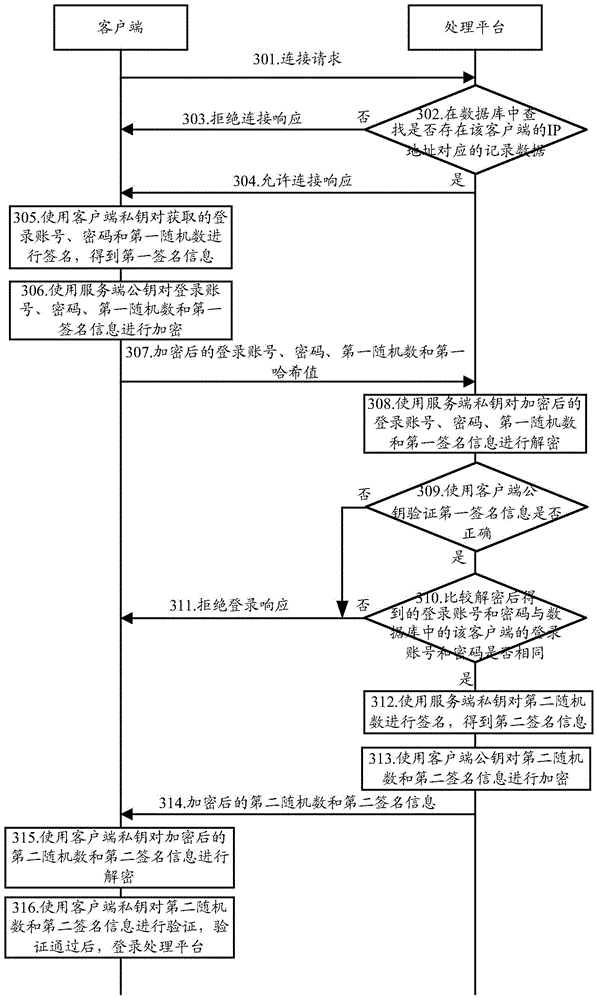
Authentication method and system, storage medium and big data authentication platform
PendingCN111476640ATimely and effective assessment basisWeb data indexingDigital data protectionBusiness enterpriseEngineering
Owner:江苏思特瑞信息技术有限公司
Authentication system and method thereof for dial-up networking connection via terminal
InactiveUS20060053484A1Service degradationShortening duration of timeDigital data processing detailsCharacter and pattern recognitionAuthentication systemDial-up Internet access
Owner:LG ELECTRONICS INC
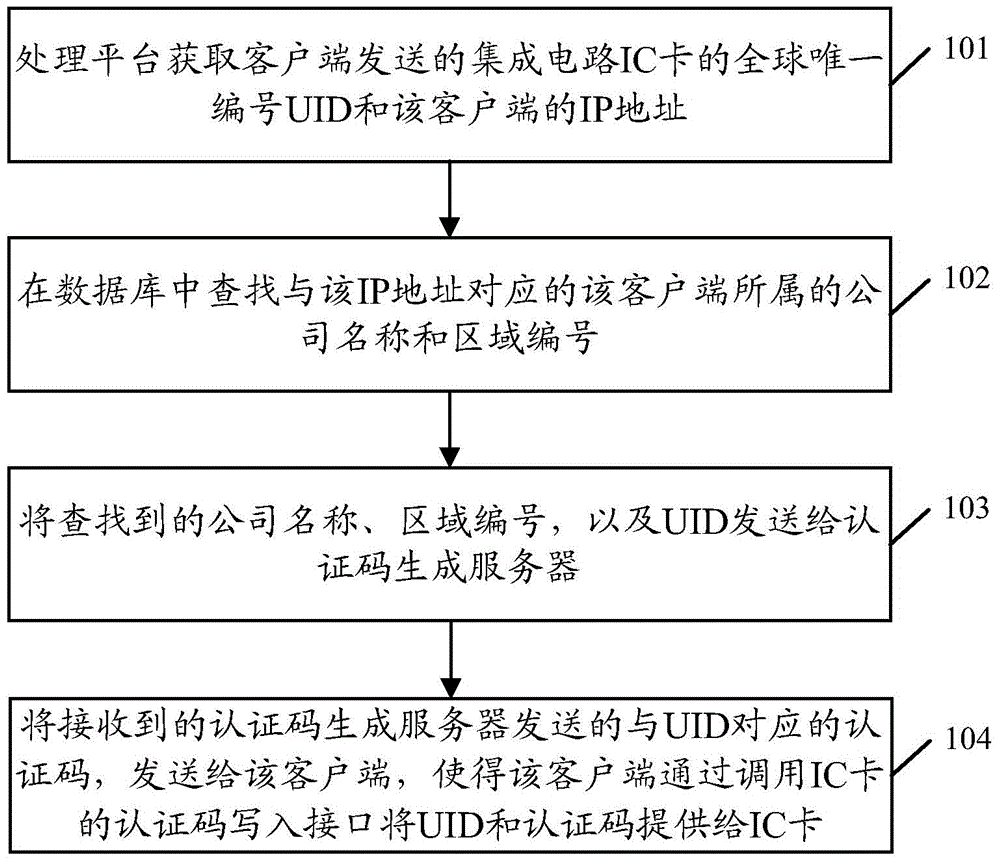
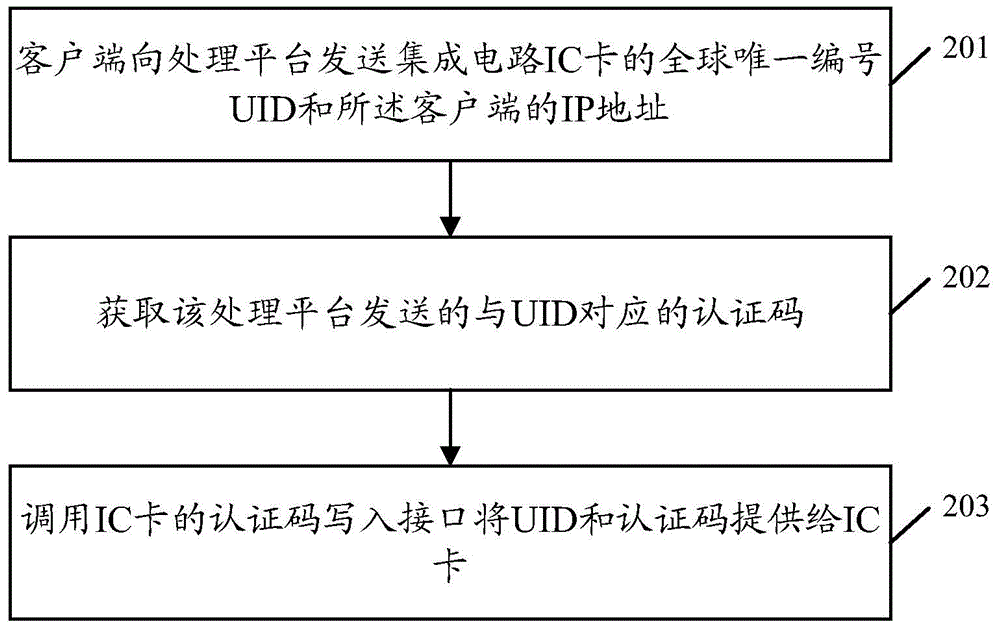
Method, device and system for obtaining authentication code of integrated circuit card
ActiveCN106330821AShort processReduce acquisition timeUser identity/authority verificationCode writingComputer hardware
Owner:SUMAVISION TECH CO LTD
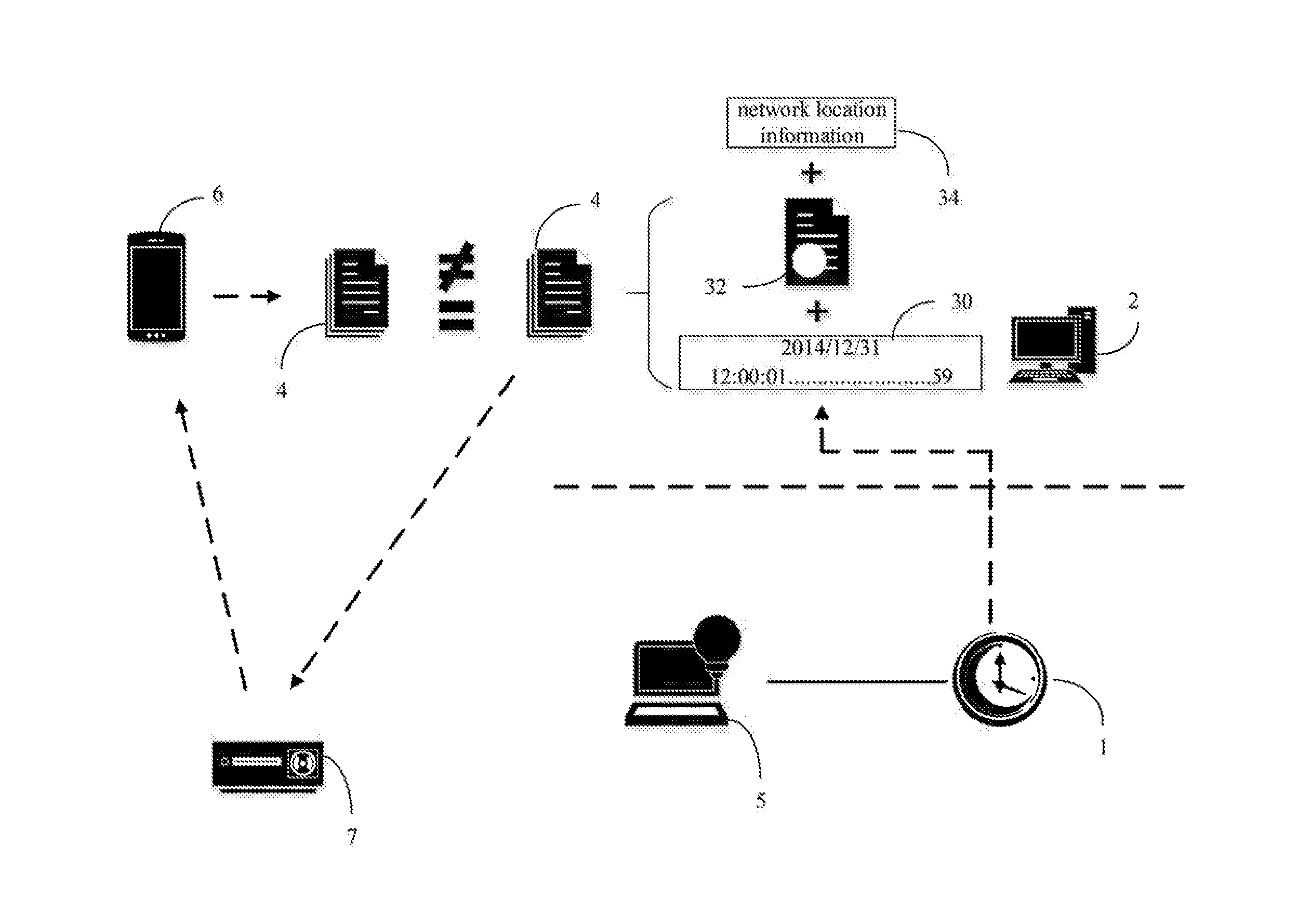
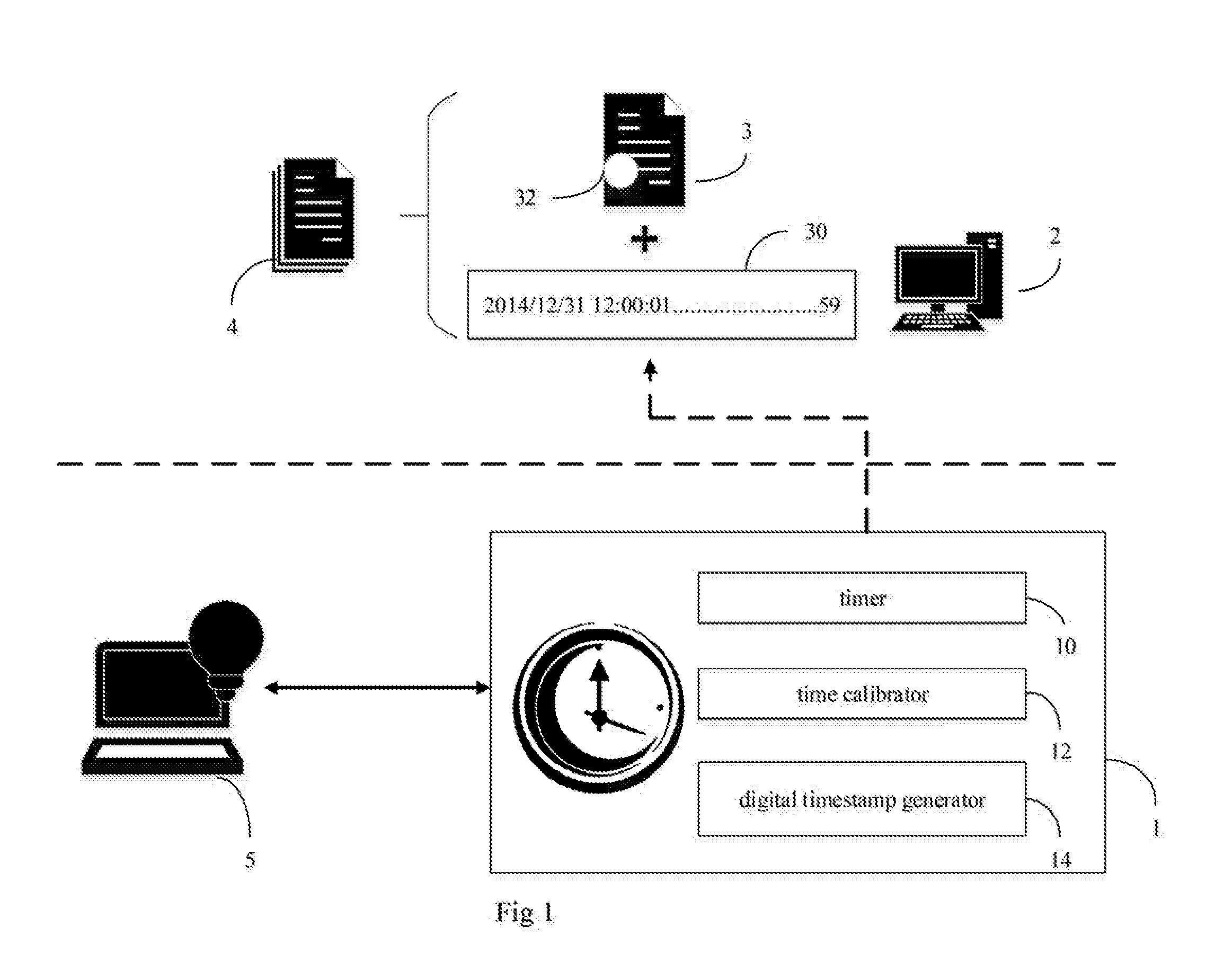
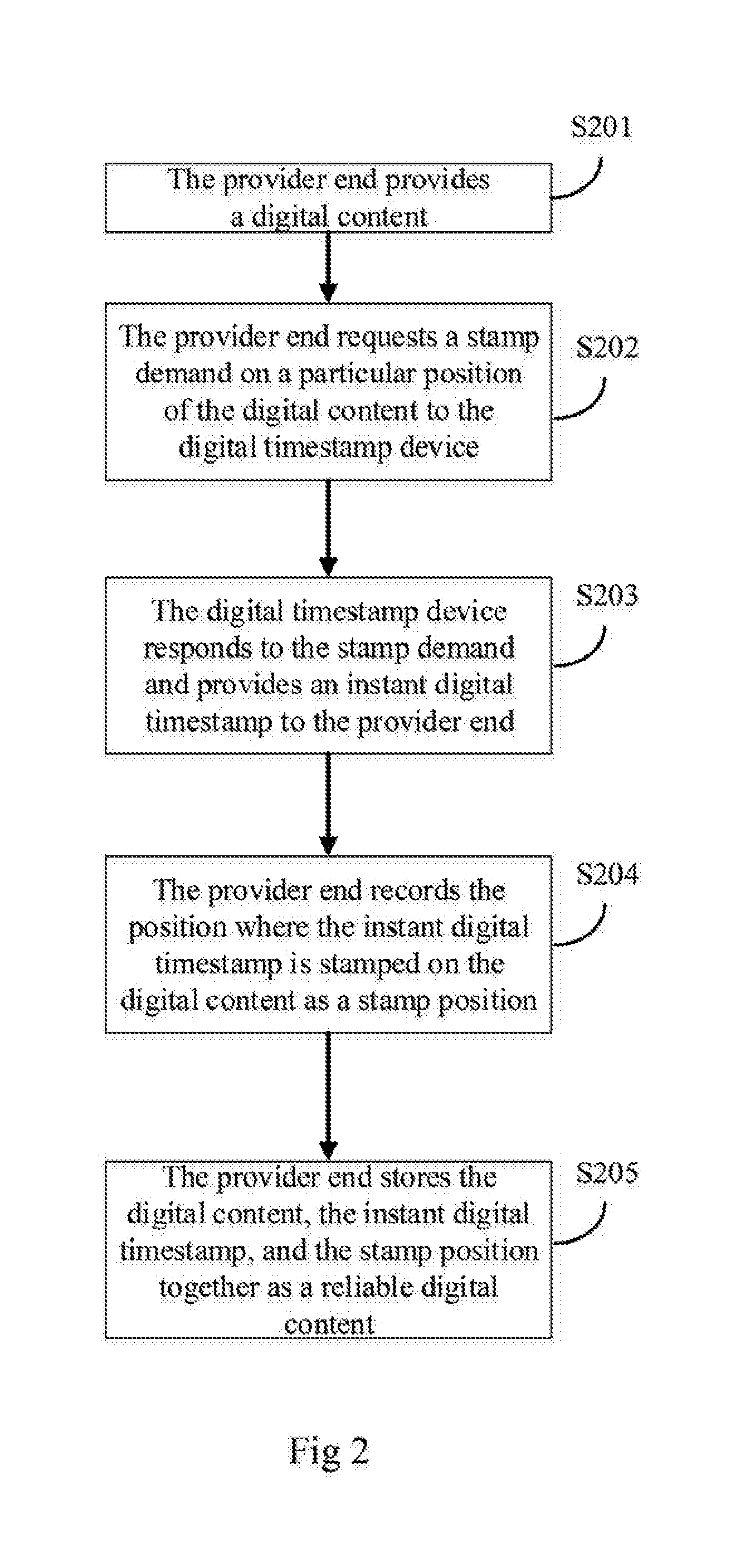
Authentication system of synchronizing instant timestamp and a method thereof
ActiveUS20160188892A1Verify authenticityTime-division multiplexAnalogue secracy/subscription systemsAuthentication systemTimestamp
Owner:MORIMOTO
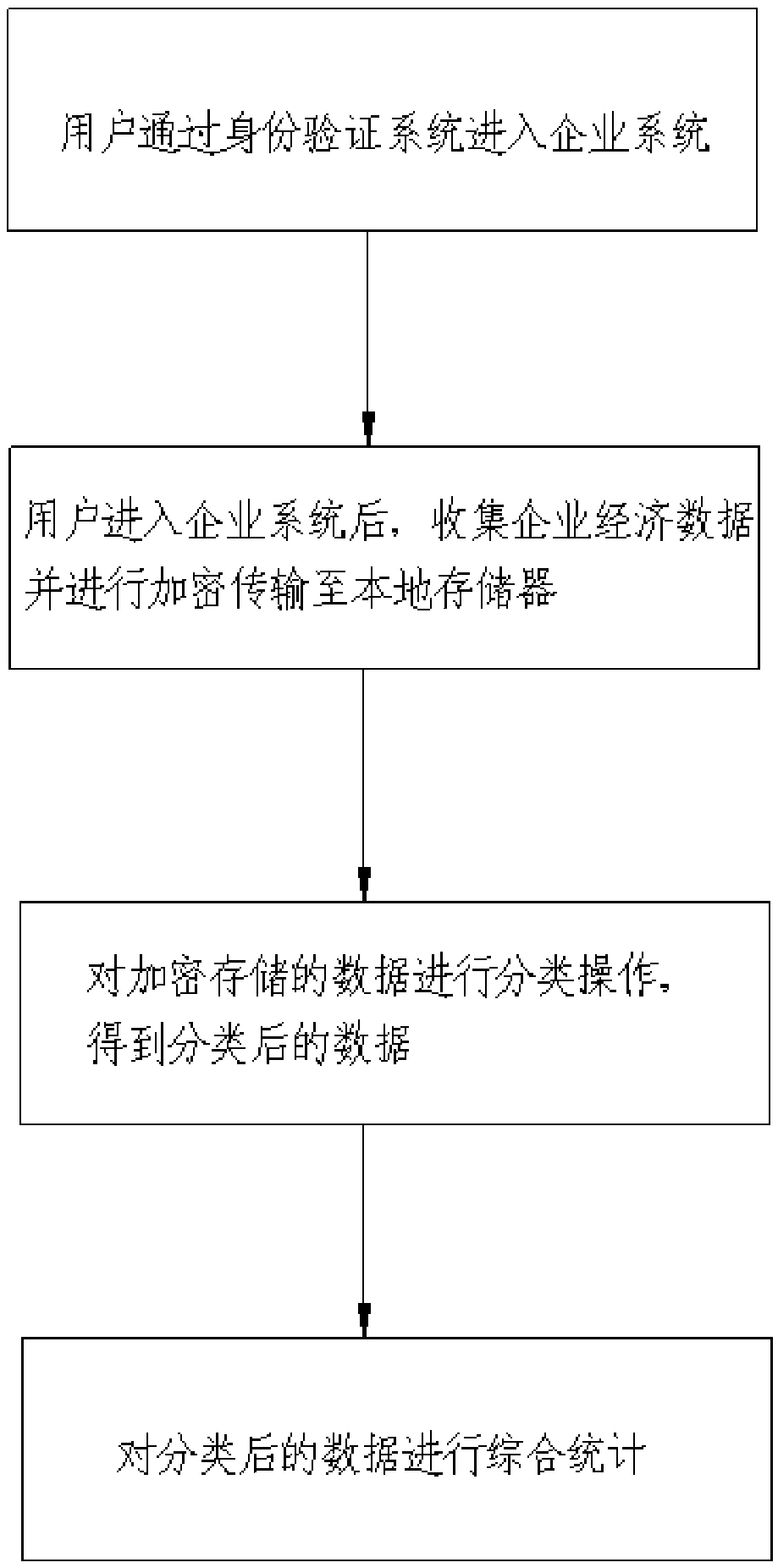
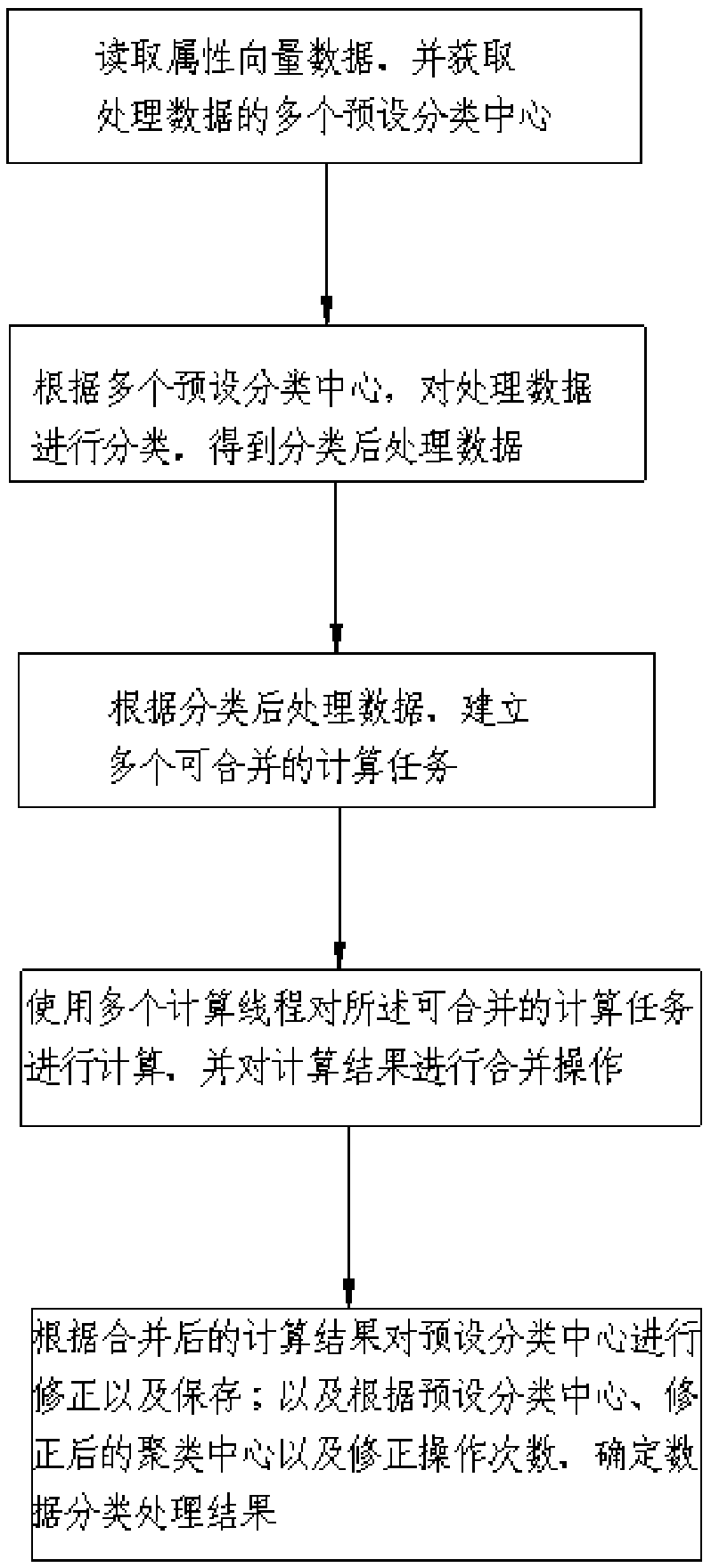
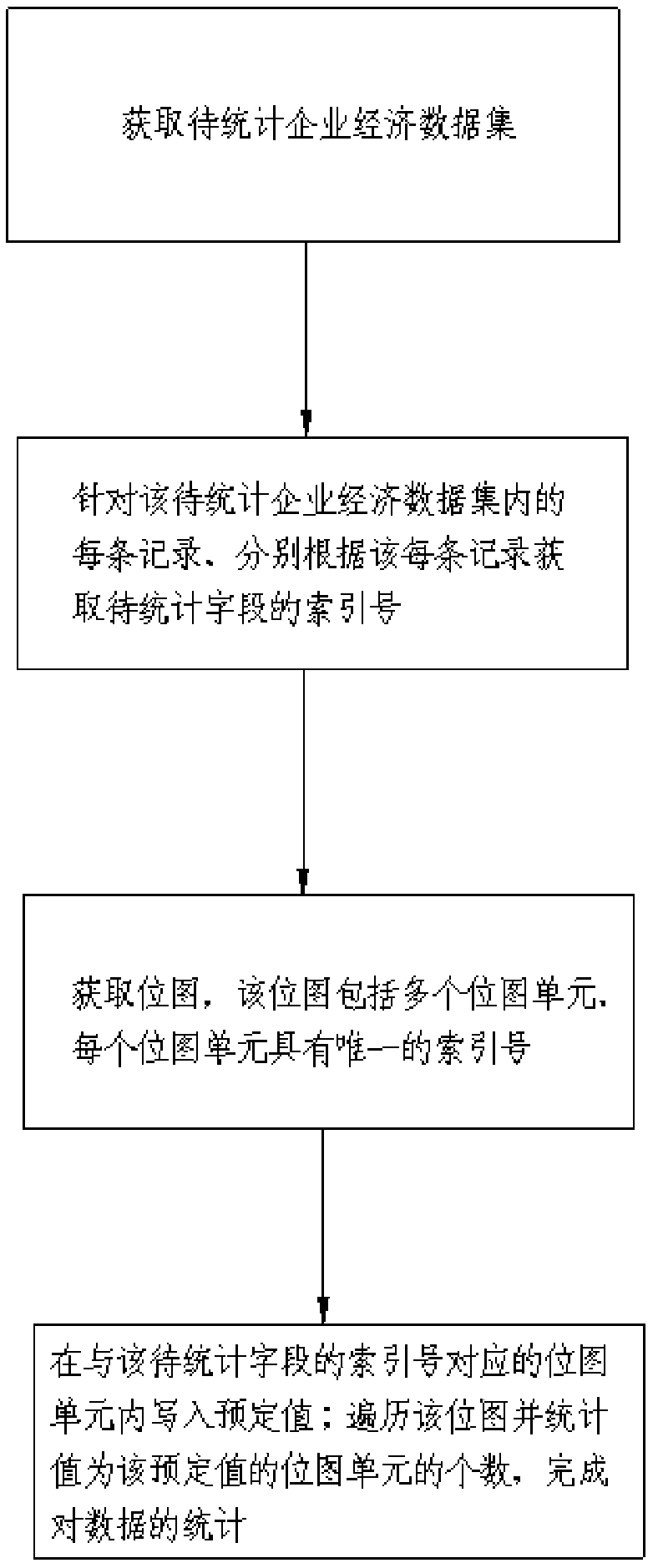
Method for statistical informatization of enterprise economic data
InactiveCN108763945AImplement encryptionImplement classificationDigital data protectionTransmissionInformatizationAuthentication system
Owner:PINGXIANG UNIV
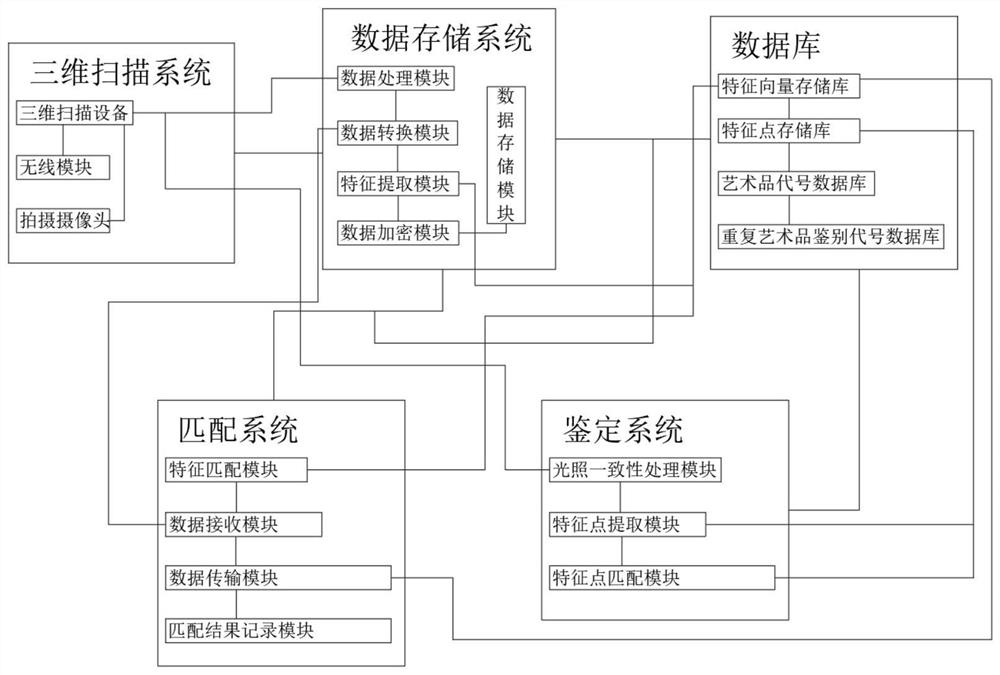
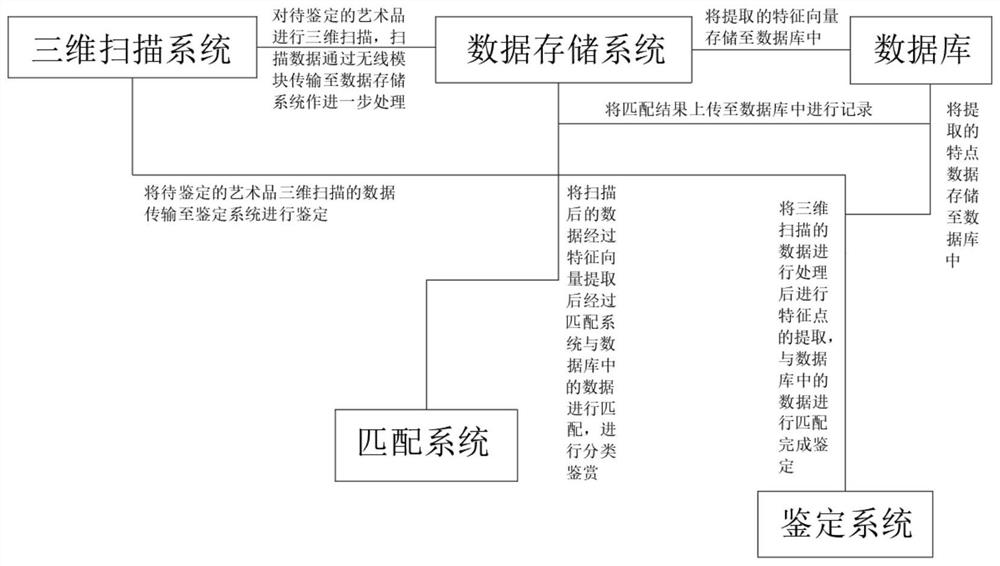
Identification learning system for artwork body identification
PendingCN114816850AAvoid critique learningReduce usageDigital data protectionRedundant operation error correctionBody identificationFeature extraction
Owner:深圳壹盆花文创科技有限公司
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap