Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
20 results about "User identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
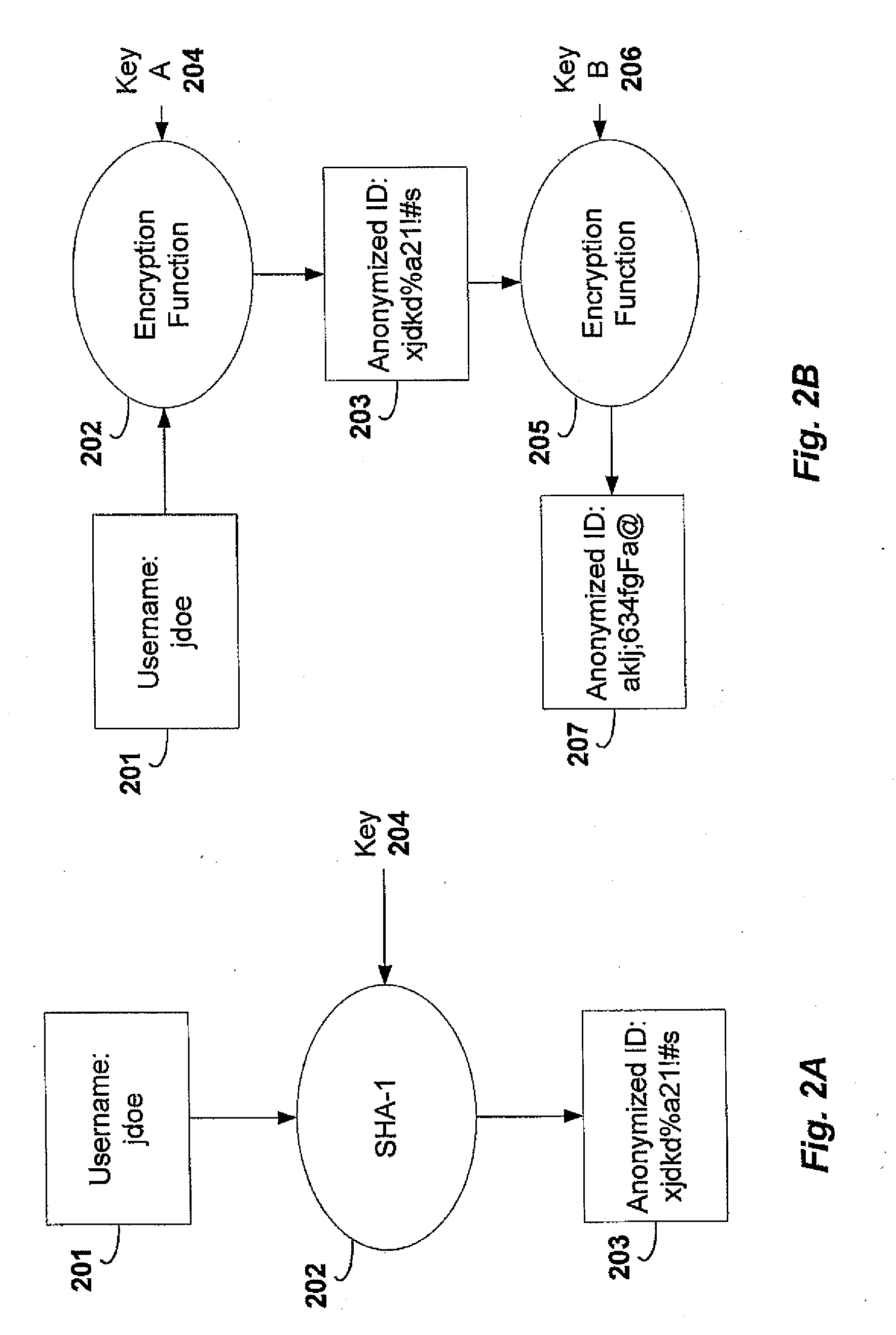
Unix-like operating systems identify a user by a value called a user identifier, often abbreviated to user ID or UID. The UID, along with the group identifier (GID) and other access control criteria, is used to determine which system resources a user can access. The password file maps textual user names to UIDs. UIDs are stored in the inodes of the Unix file system, running processes, tar archives, and the now-obsolete Network Information Service. In POSIX-compliant environments, the command-line command id gives the current user's UID, as well as more information such as the user name, primary user group and group identifier (GID).
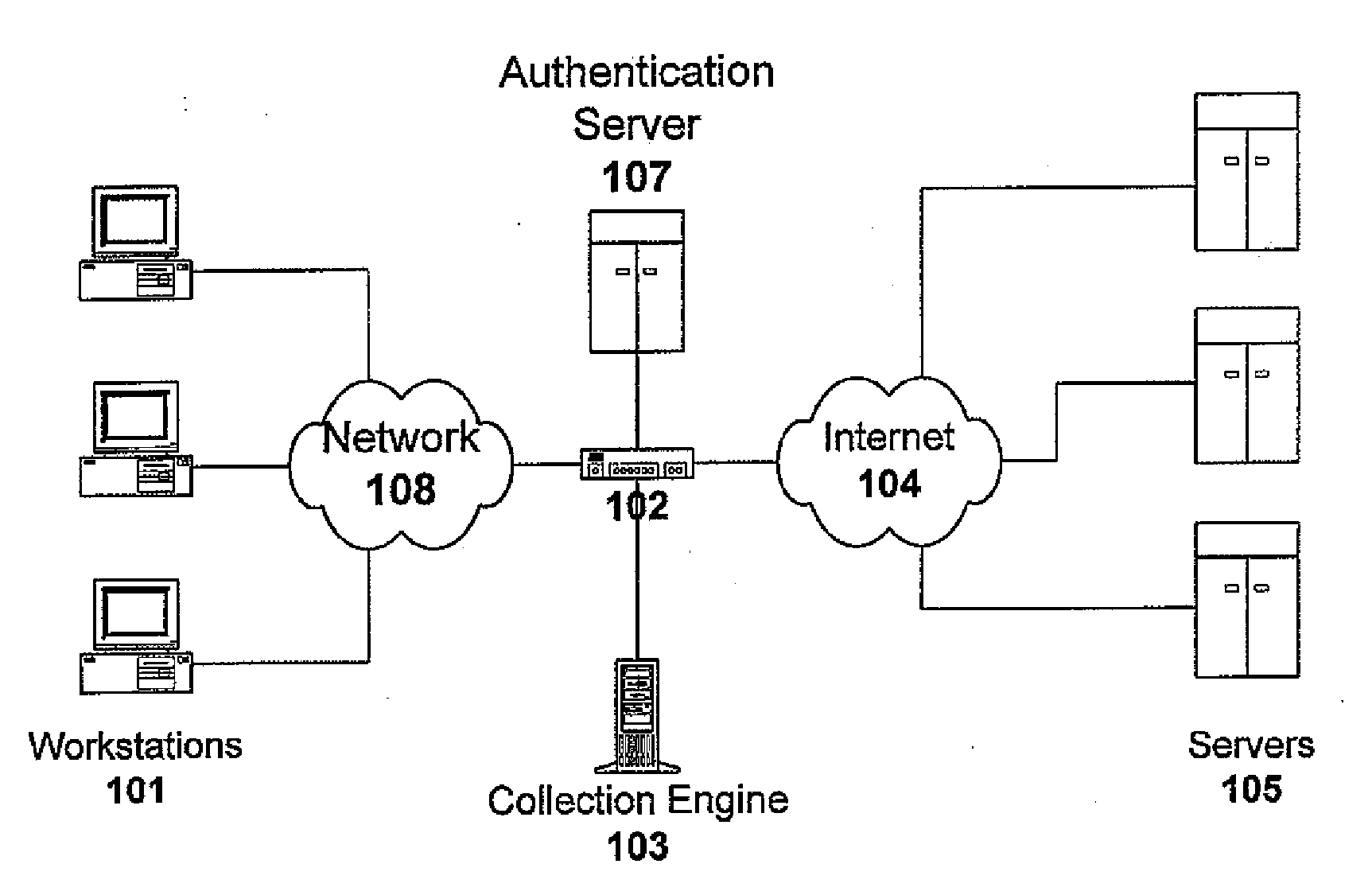
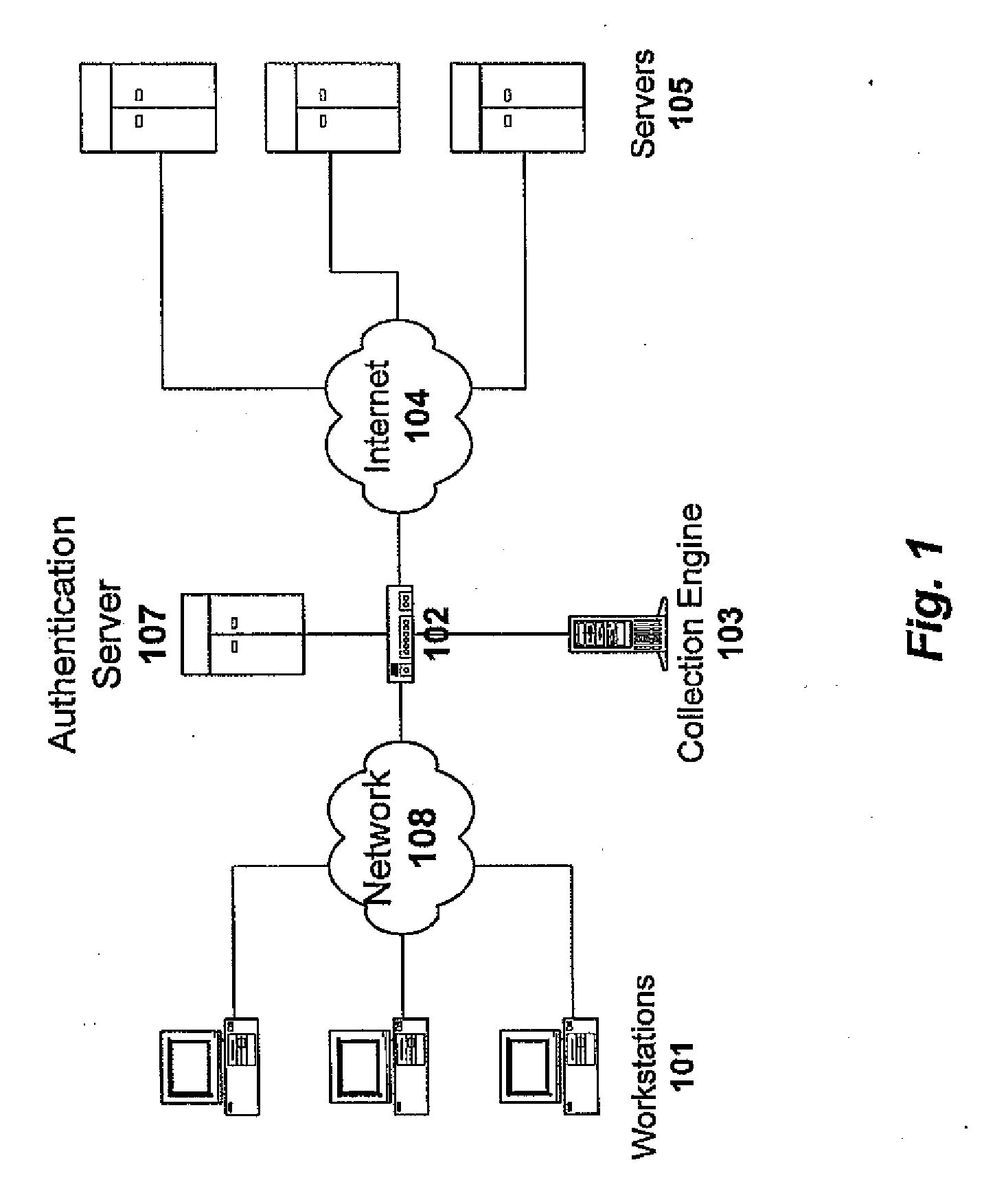
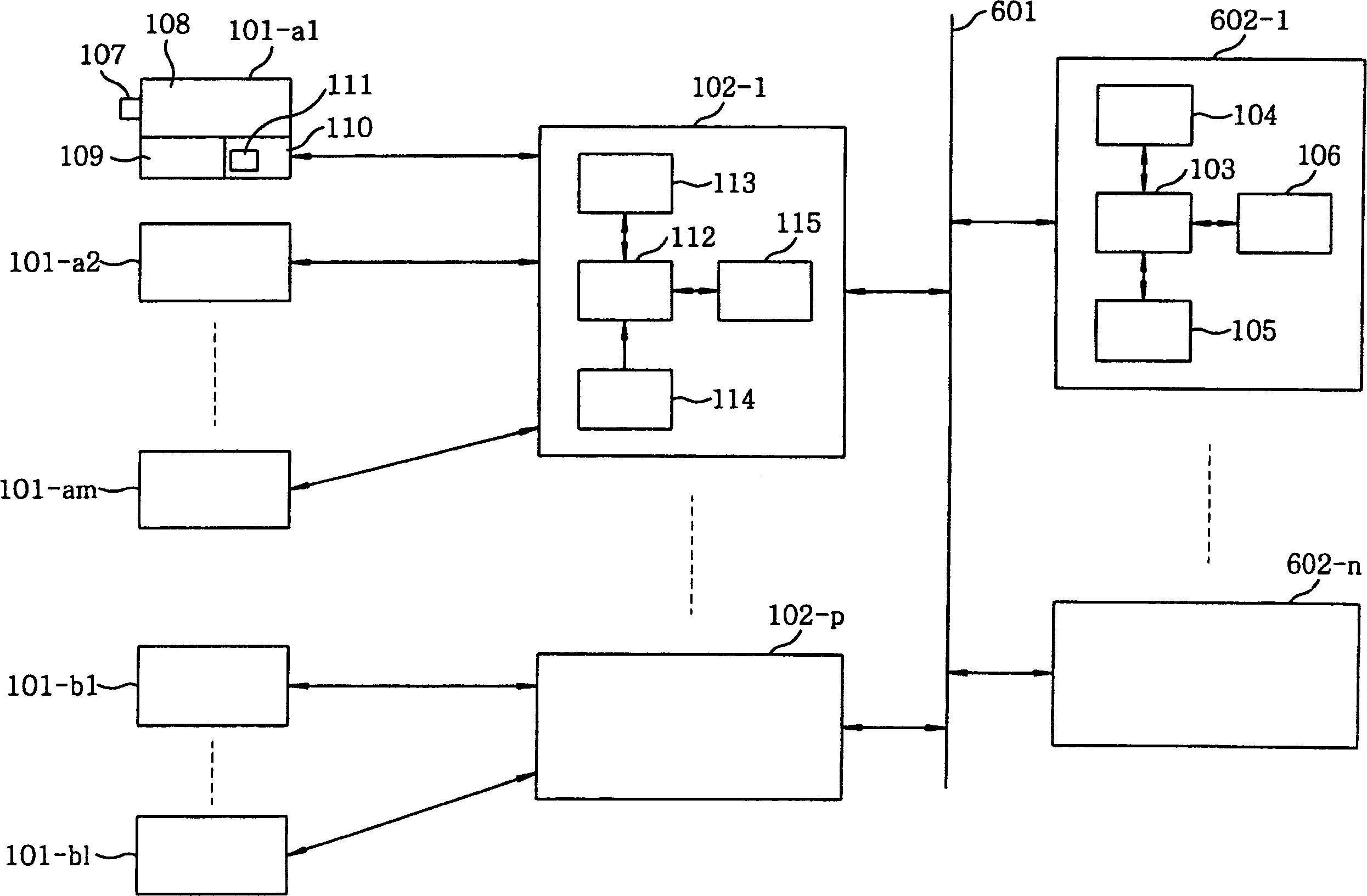
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS20090182873A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyNetwork behavior
Owner:CONNEXITY AUDIENCE INC
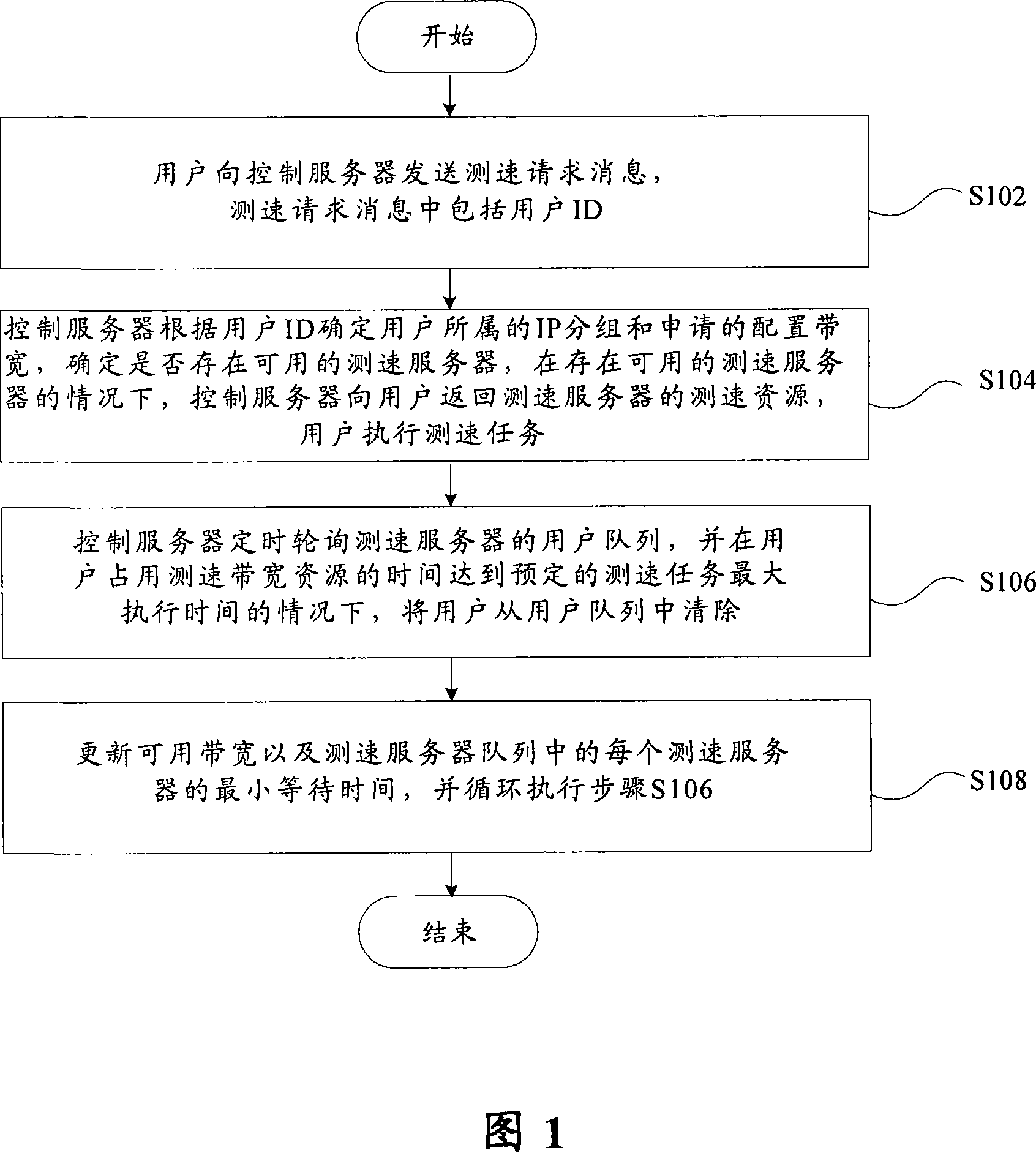
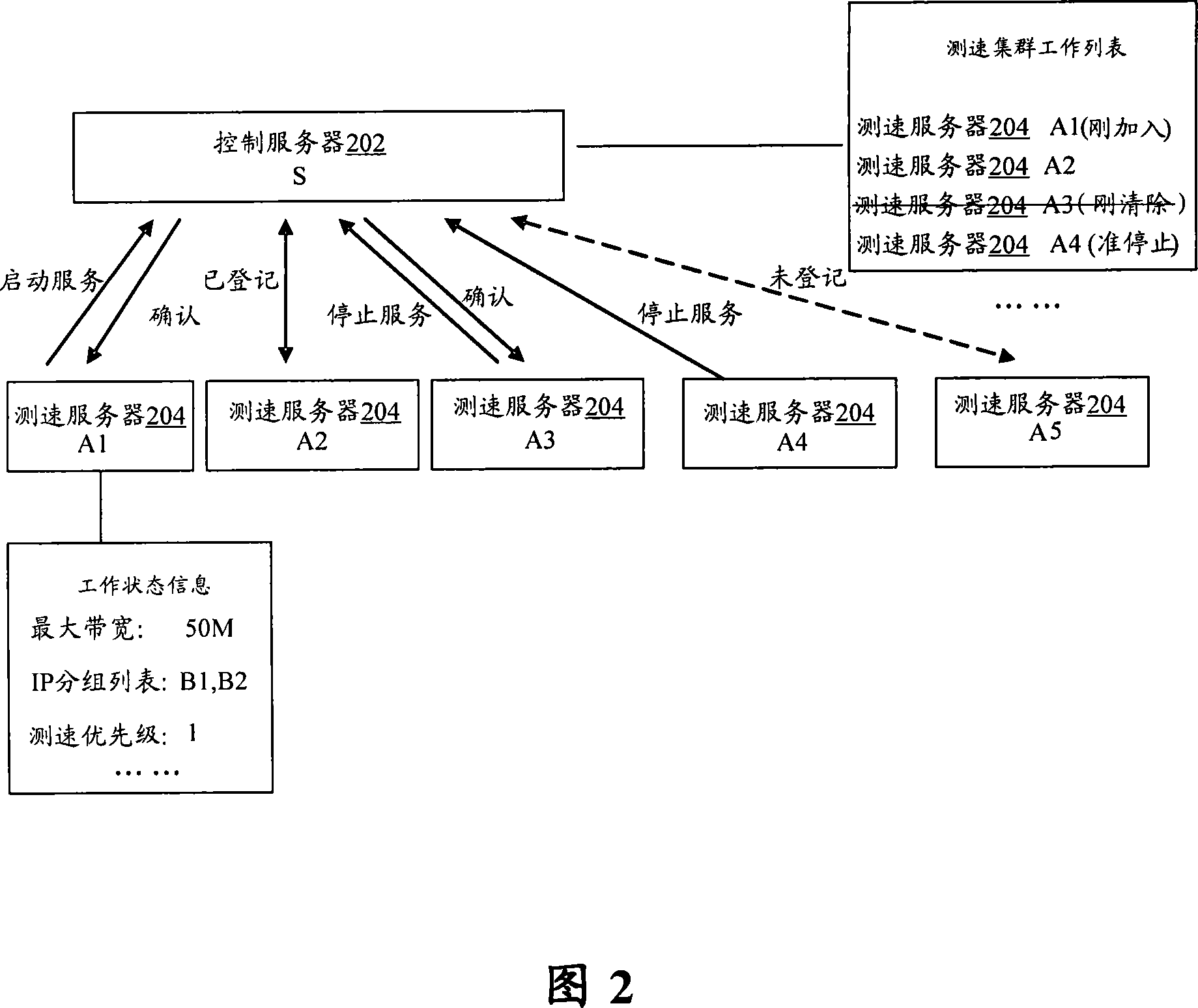
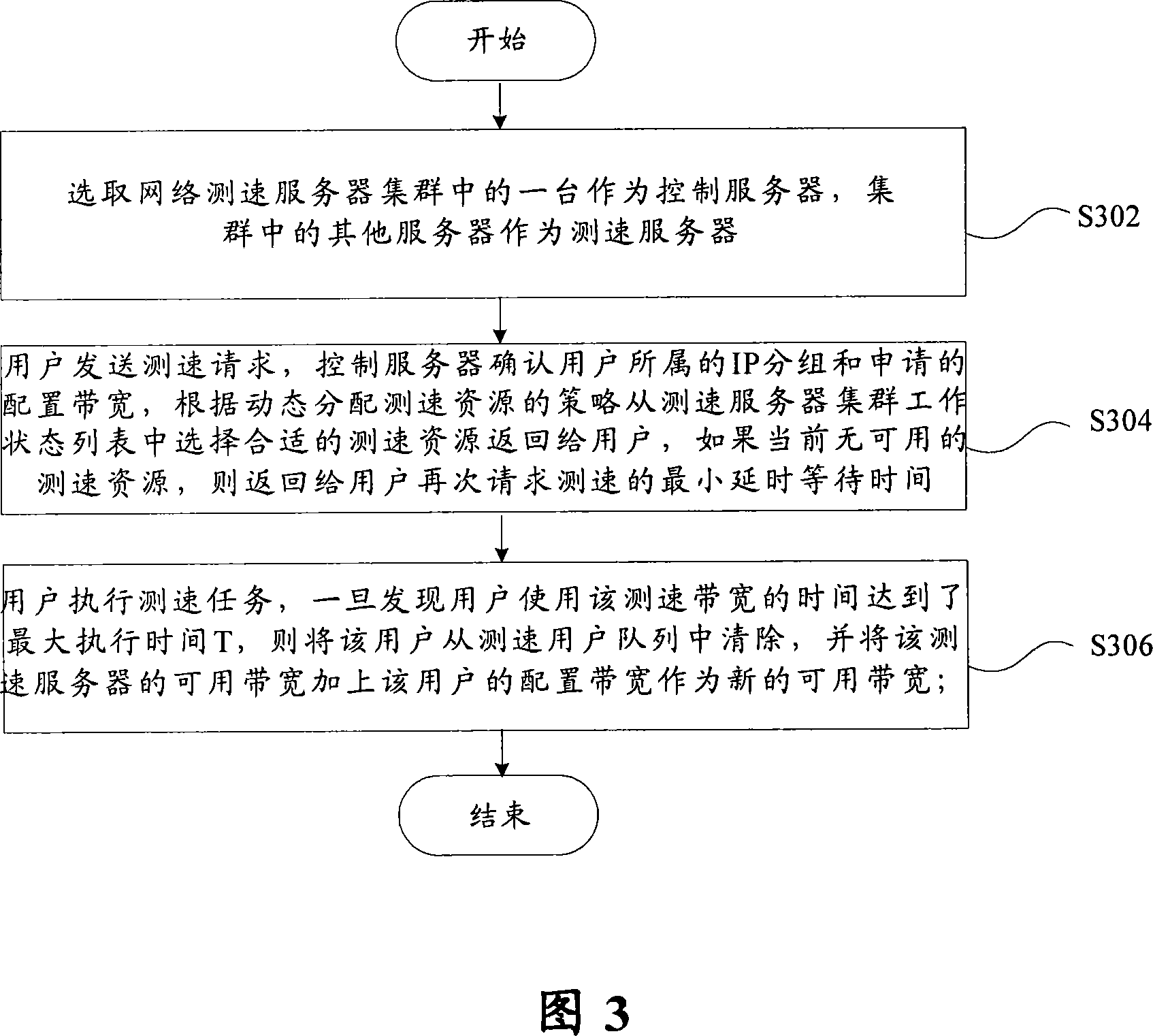
Speed-measuring resource dynamic distributing method and system for network speed-measuring system
InactiveCN101068171AGuaranteed credibilityGuaranteed accuracyData switching networksUser identifierWaiting time
Owner:GLOBAL INNOVATION AGGREGATORS LLC
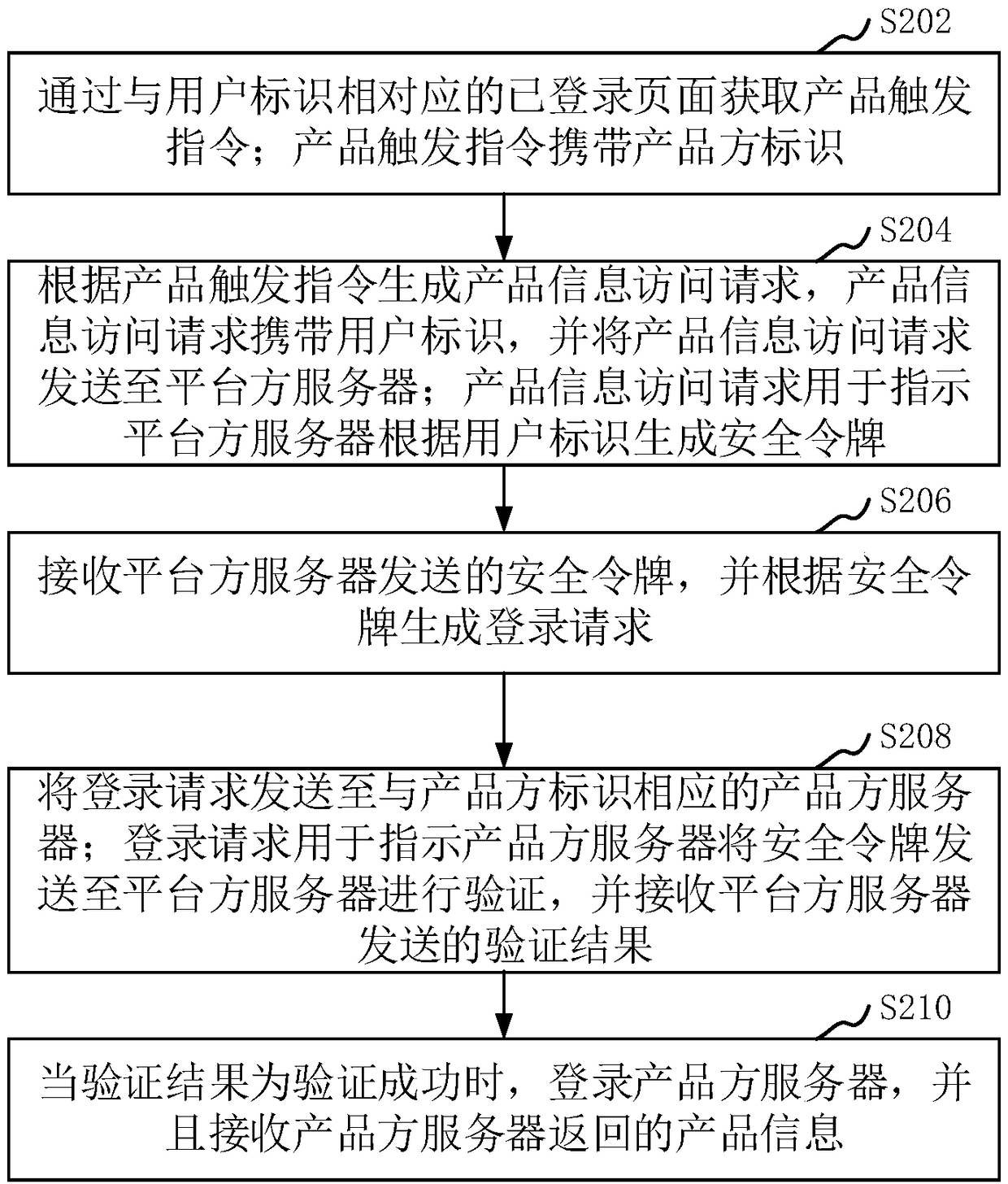
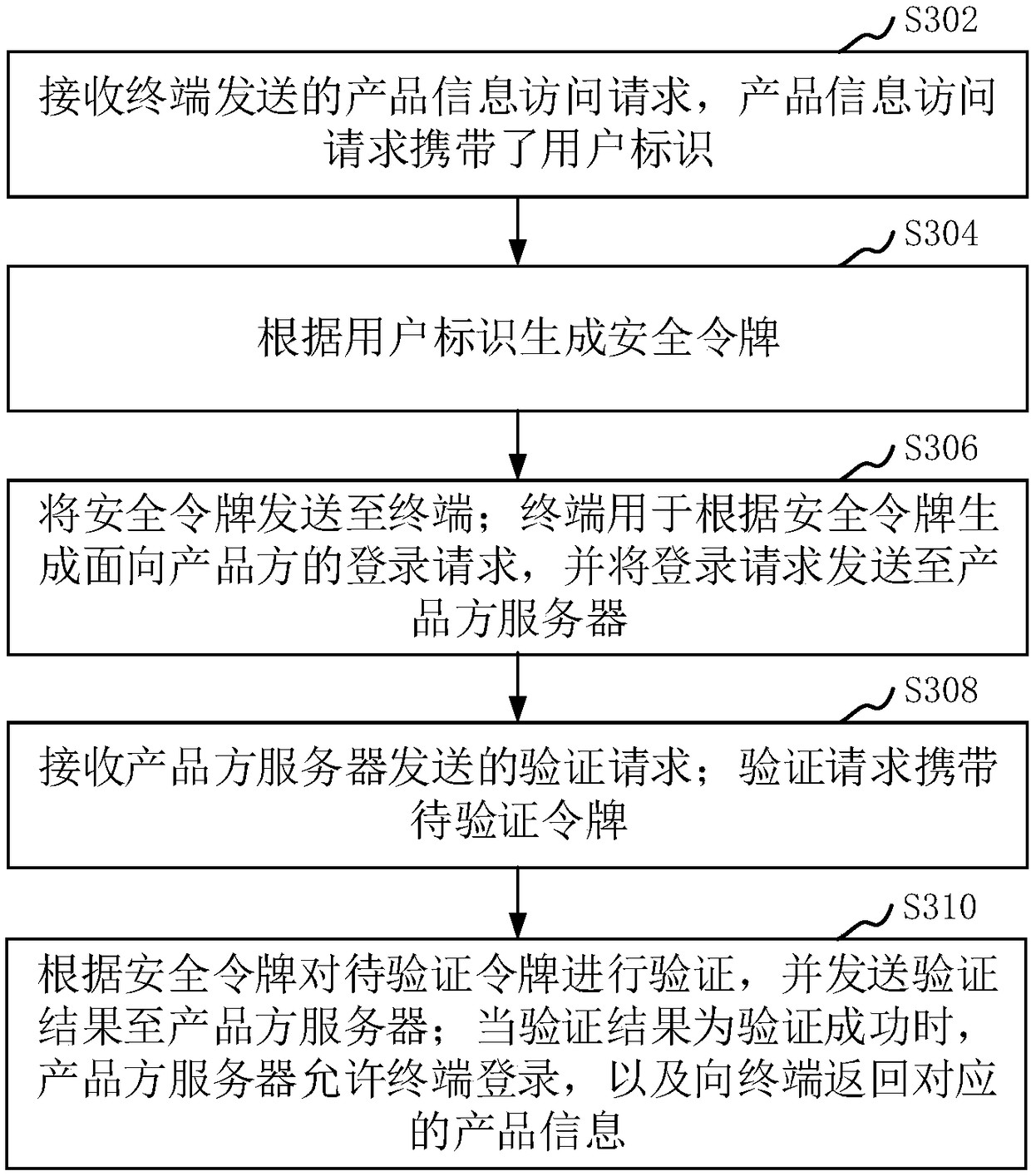
Login method and system, computer device and storage medium
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
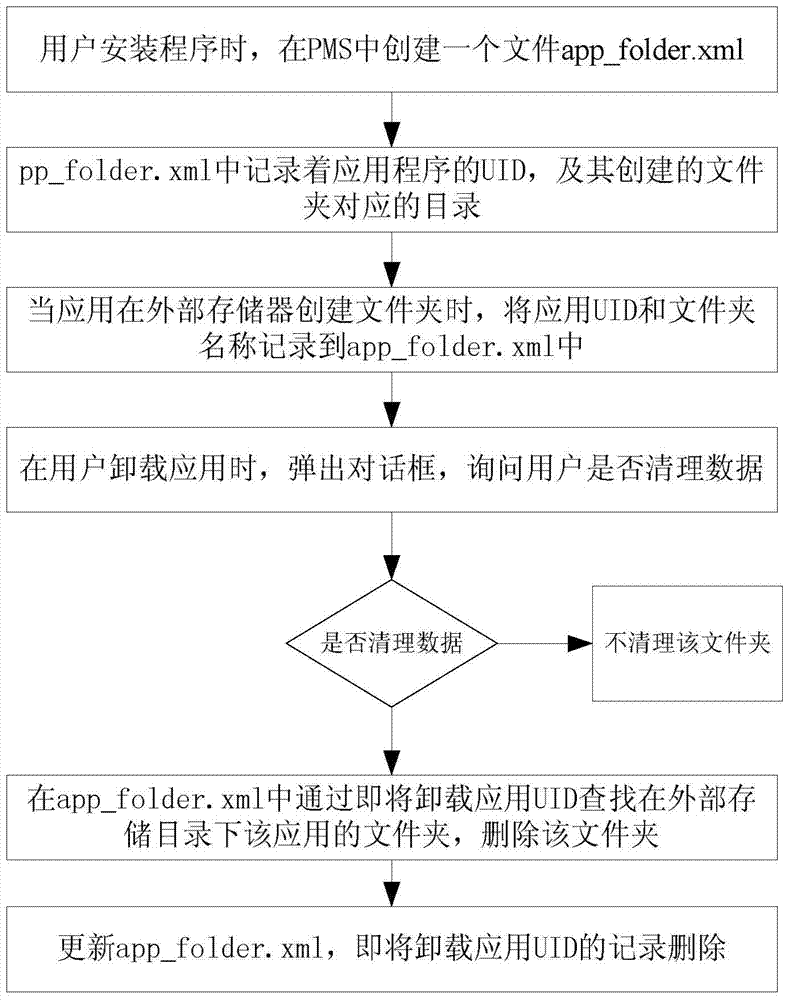
Method for uninstalling application and deleting garbage file in Android system
InactiveCN103577567AClean up in timeRapid positioningSpecific program execution arrangementsSpecial data processing applicationsExternal storagePackage management
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Face recognition method, device, computer device and storage medium
PendingCN109241868AEnsure safetyImprove recognition efficiencyCharacter and pattern recognitionFeature vectorImage extraction
The invention discloses a face recognition method, a device, a computer device and a storage medium. The face recognition method comprises the following steps: obtaining an image to be recognized, extracting a feature vector to be recognized according to the image to be recognized; acquiring a feature similarity between the feature vector to be identified and each reference feature vector; takingthe user identifier corresponding to the reference feature vector with the highest feature similarity as the target user identifier; obtaining a target region in the image to be recognized according to the target user identifier, and extracting a target feature vector according to the target region; calculating the vector similarity between the target feature vector and the user-defined feature vector corresponding to the target user identification, and obtaining the recognition result according to the vector similarity. The face recognition method provided by the invention does not need multiple frames of images for comprehensive verification, does it need to train a complex neural network model in advance to realize, and can ensure the safety of the face recognition process and improve the recognition efficiency at the same time.
Owner:PING AN TECH (SHENZHEN) CO LTD
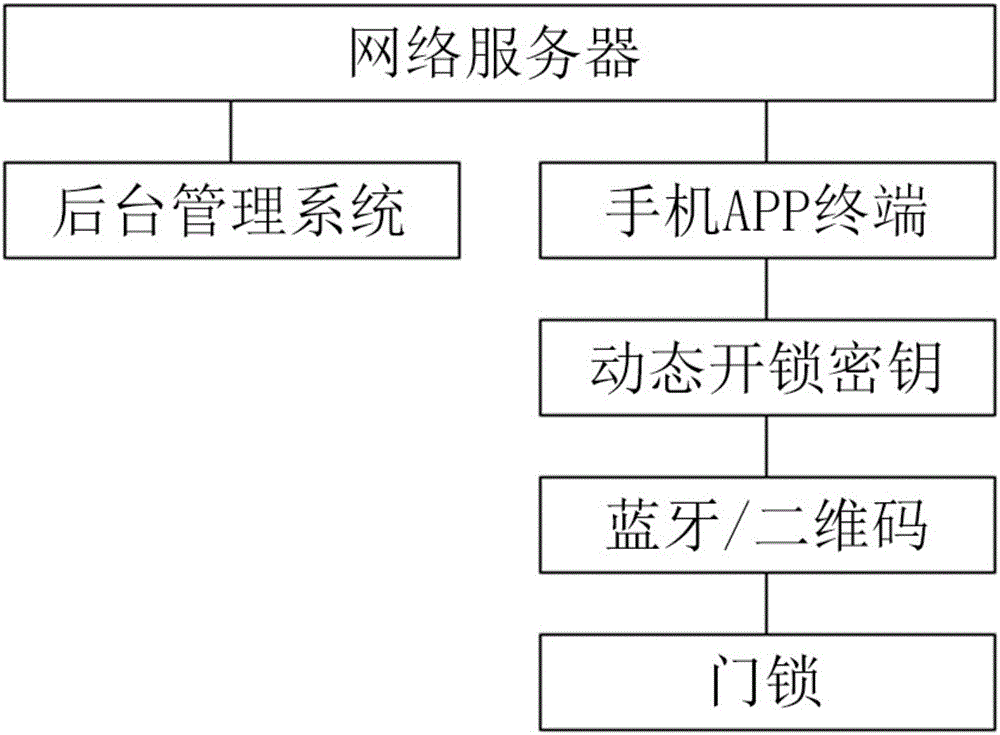
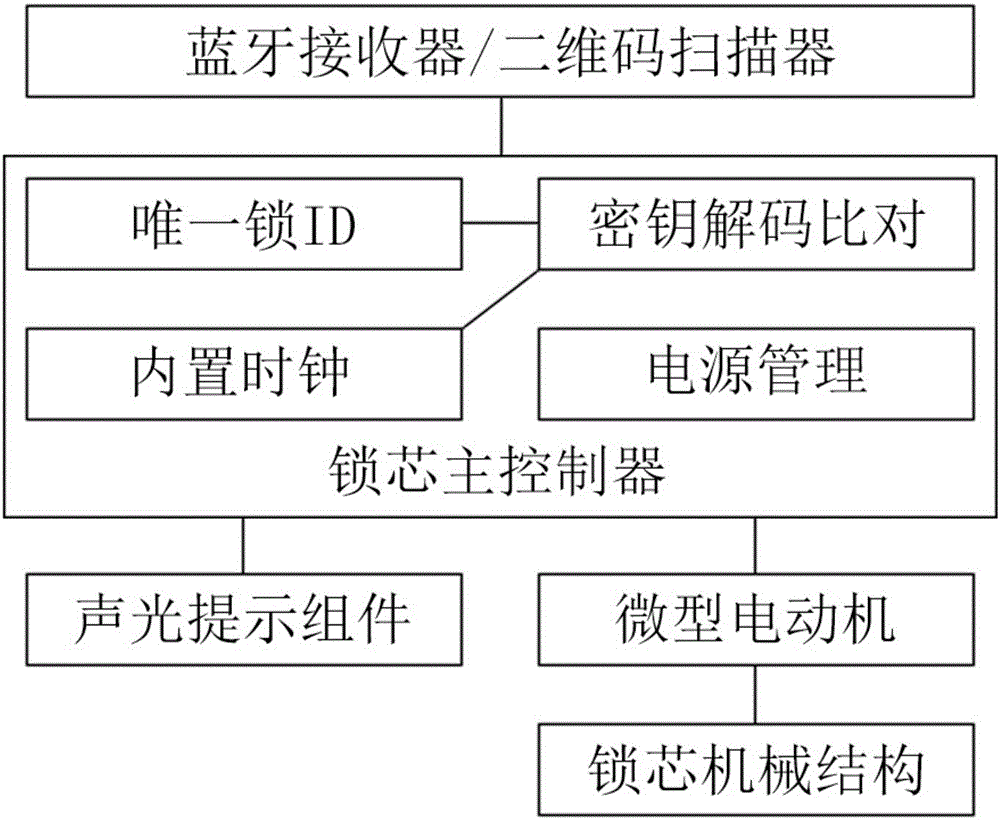
House-renting management system capable of opening locks based on Bluetooth or two-dimensional codes and method thereof
InactiveCN106530454ALow costProtection of rights and interestsData processing applicationsIndividual entry/exit registersStructure of Management InformationDimensional modeling
Owner:俞毅
Message subscription management apparatus and method
ActiveCN106095789AImprovements to detail storageReduce storageSpecial data processing applicationsArray data structureFirst generation
The invention discloses a message subscription management apparatus and method. The message subscription management apparatus comprises a receiving module used for receiving a new message created by a message creator, a first generation module used for generating a message identifier corresponding to the new message, an acquisition module used for acquiring a subscription user identifier of a subscription user of the message creator, and a storage module used for storing the message identifier in a preset storage region according to the subscription user identifier, wherein the preset storage region comprises subscription user identifier fields corresponding to the subscription user and message identifier array fields in one-to-one correspondence with the subscription user identifier fields, and the message identifier is stored in the message identifier array fields. According to the apparatus and the method, a message detail storage mode is improved, so that the data storage capacity is greatly reduced, the pressures of a server and a database are reduced, and the overall performance of the server is improved.
Owner:NUBIA TECH CO LTD
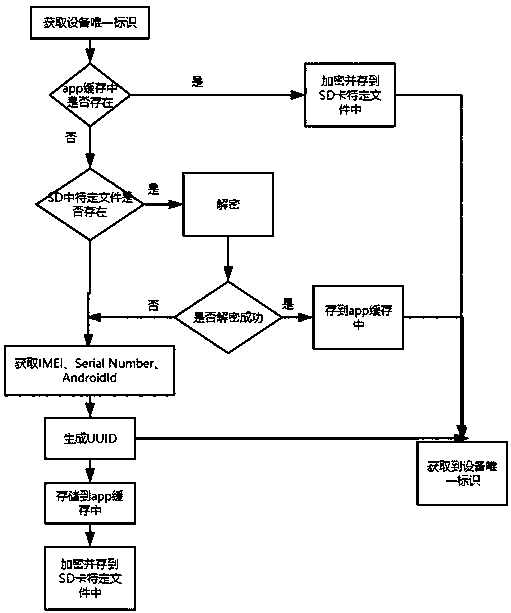
Method for acquiring unique identifier of Android equipment
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
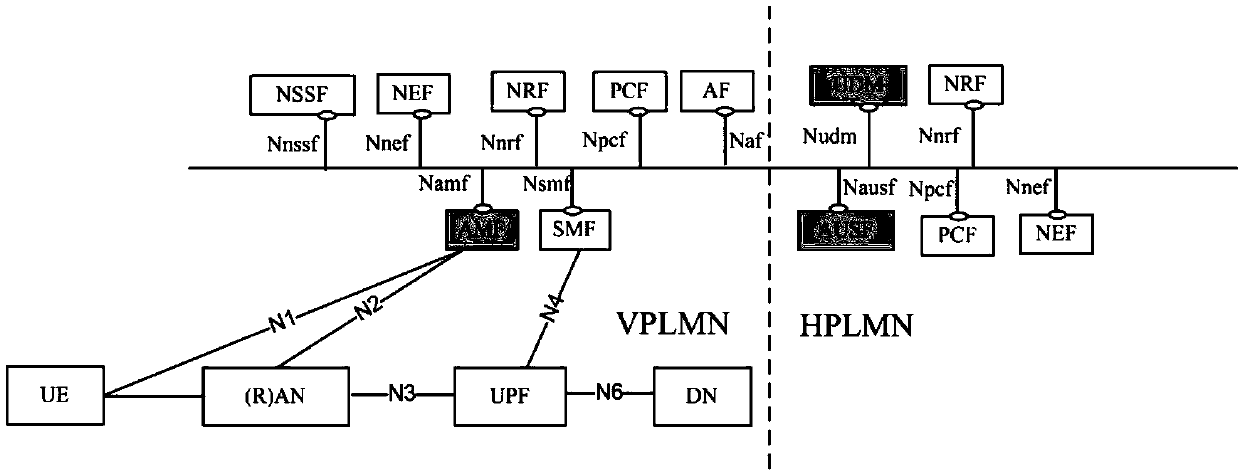
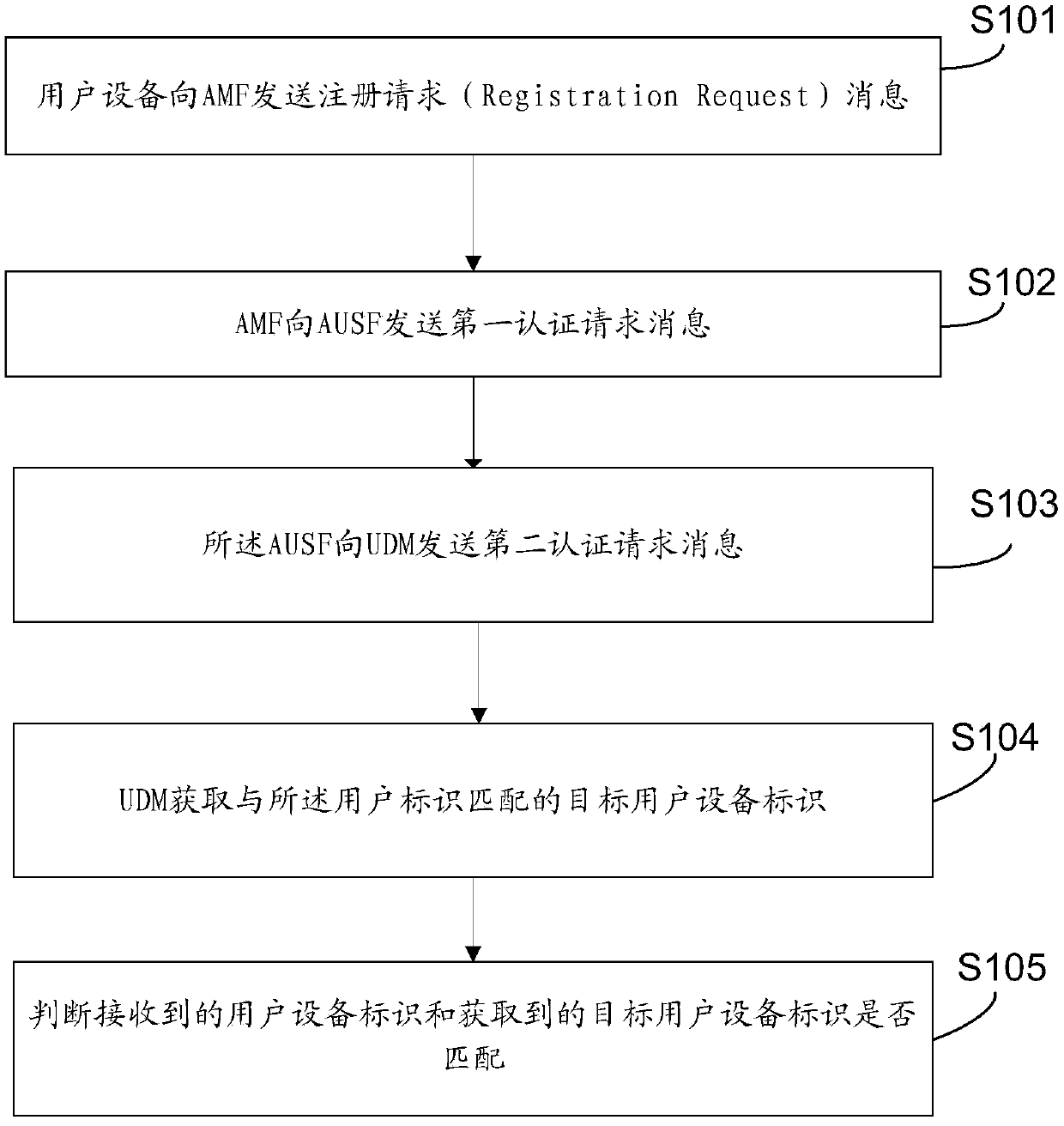
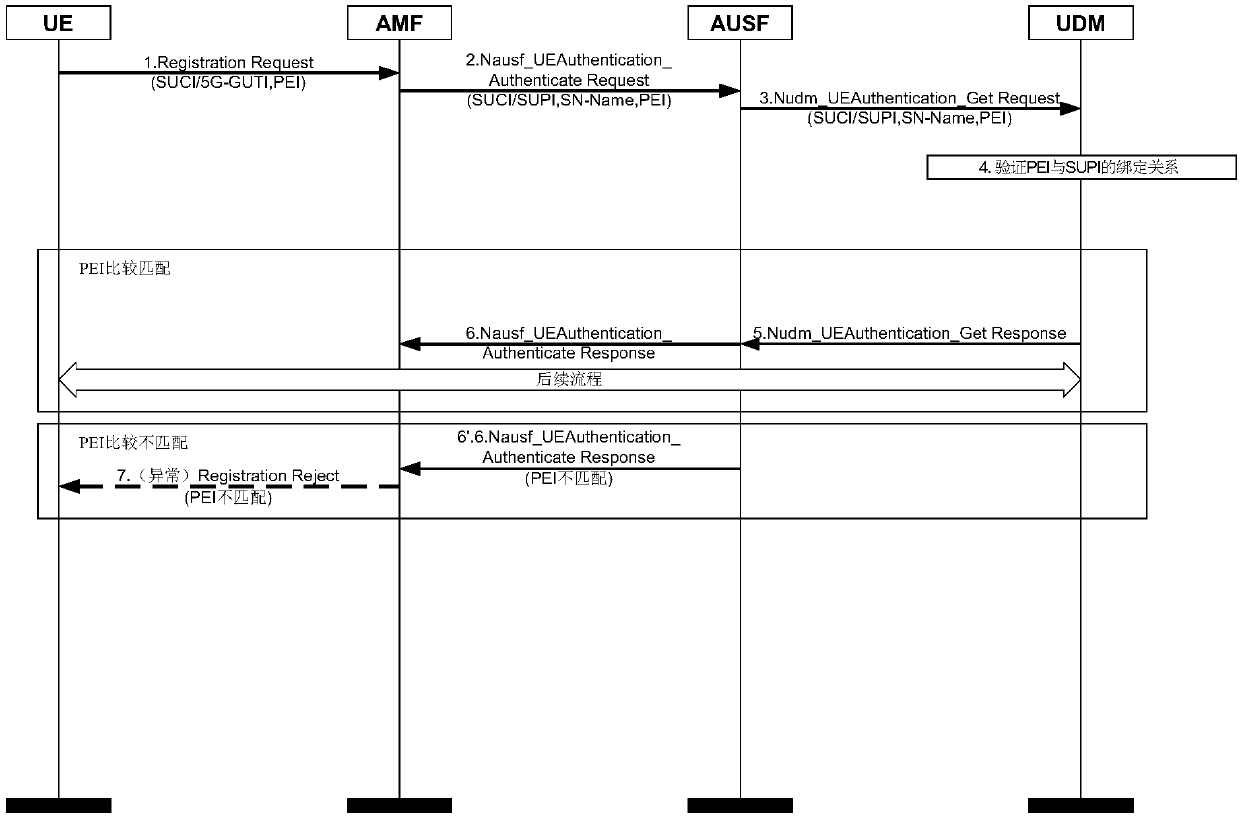
Method and device for verifying user equipment identifier in authentication process
Owner:HUAWEI TECH CO LTD
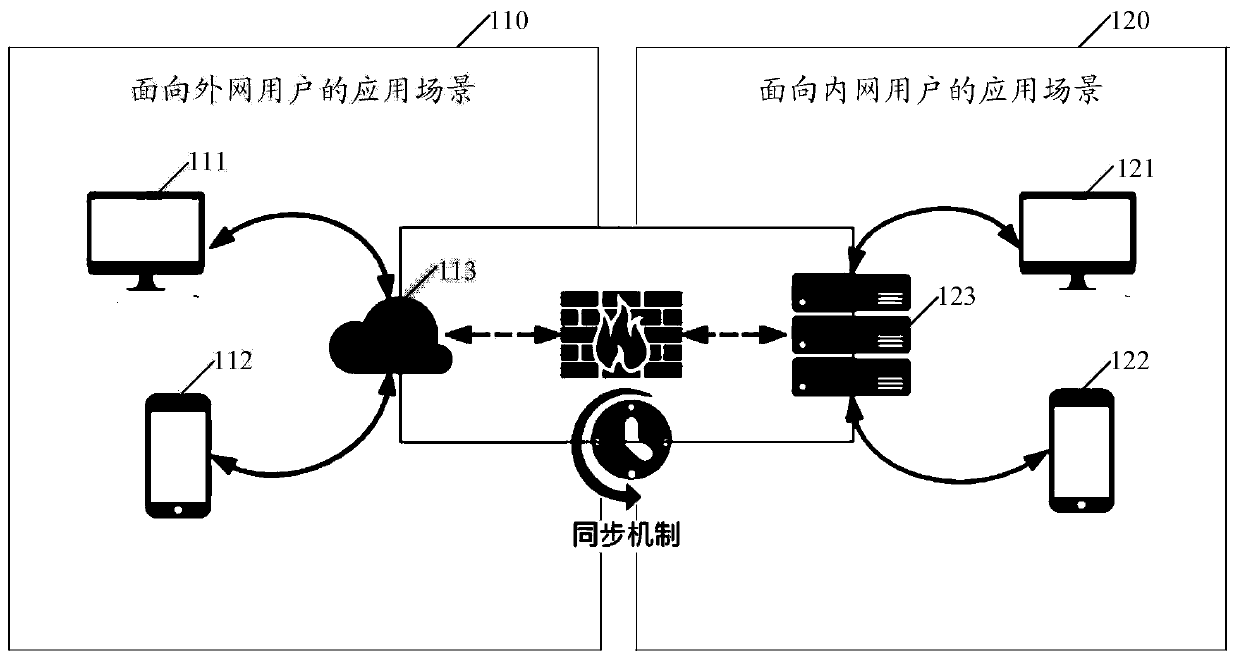
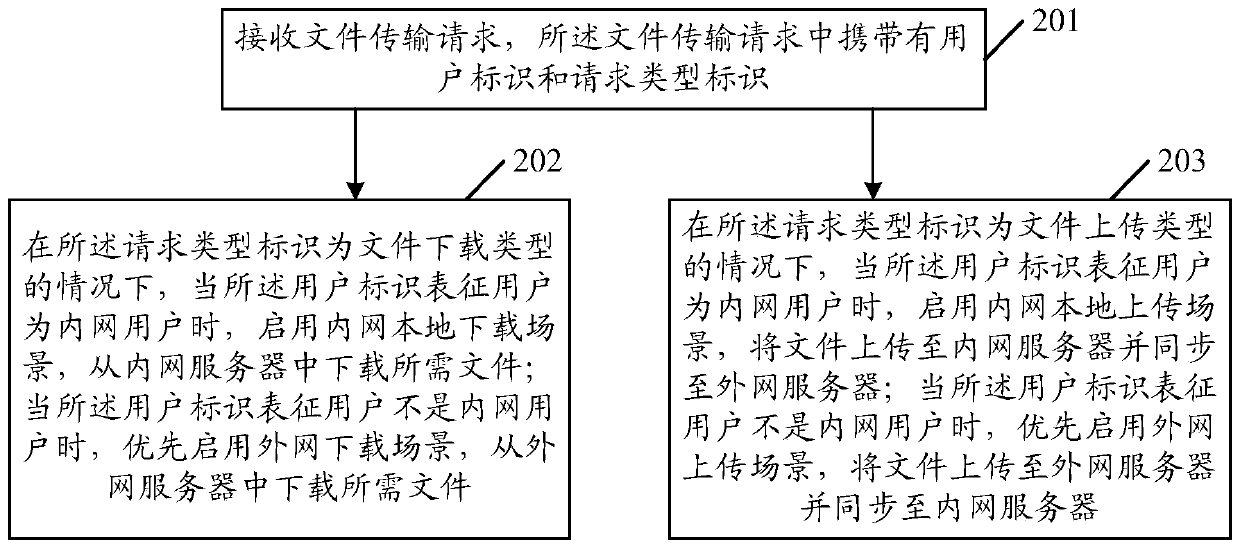
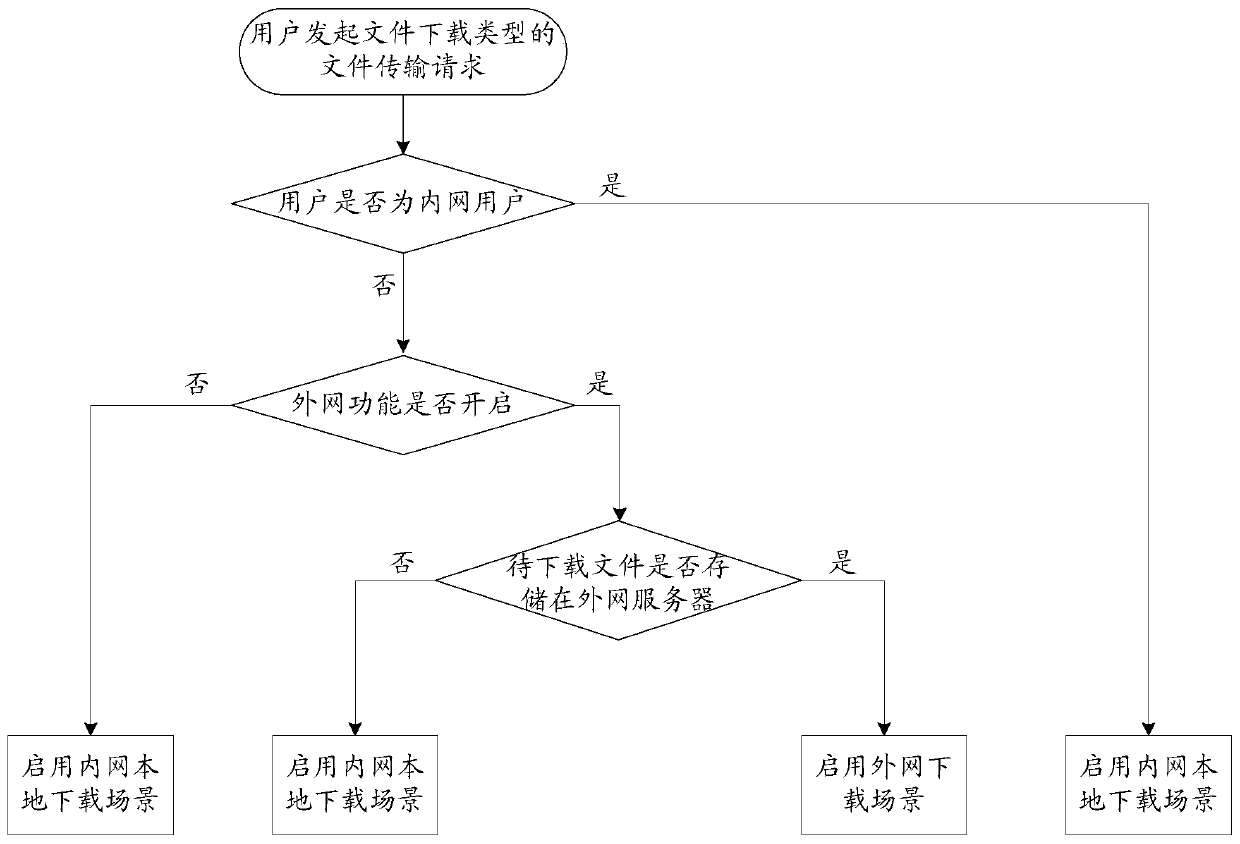
File transmission control method and device, equipment and storage medium
ActiveCN110247951ASolve the problem of linear growthIngress Bandwidth SavingsTransmissionLinear growthFile transmission
Owner:建信融通有限责任公司
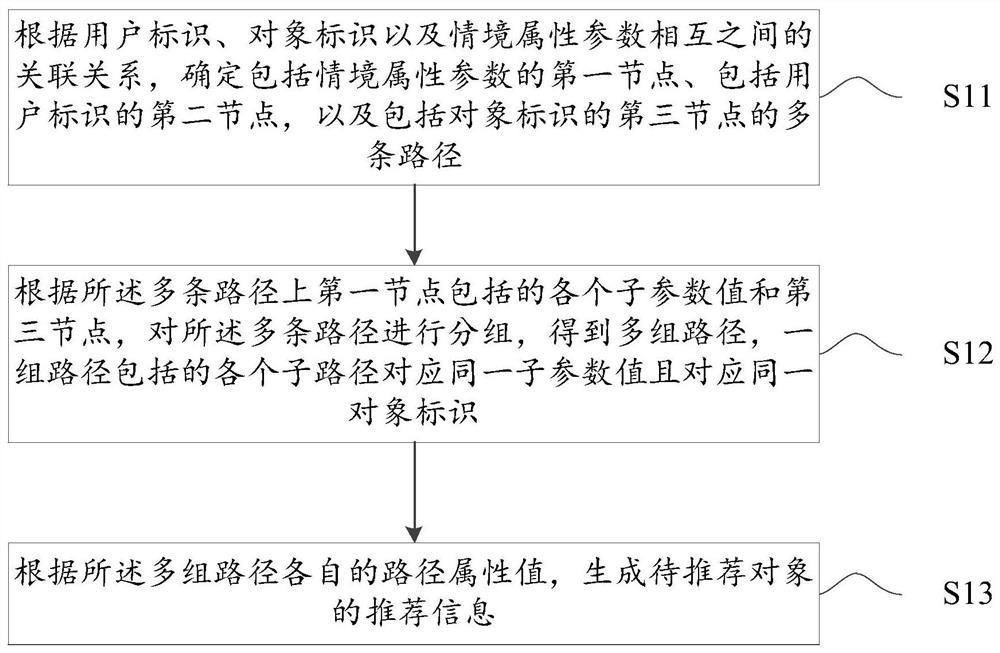
Recommendation information generation method and device, electronic equipment and readable storage medium
PendingCN111639266AInformativeDigital data information retrievalBuying/selling/leasing transactionsUser identifierEngineering
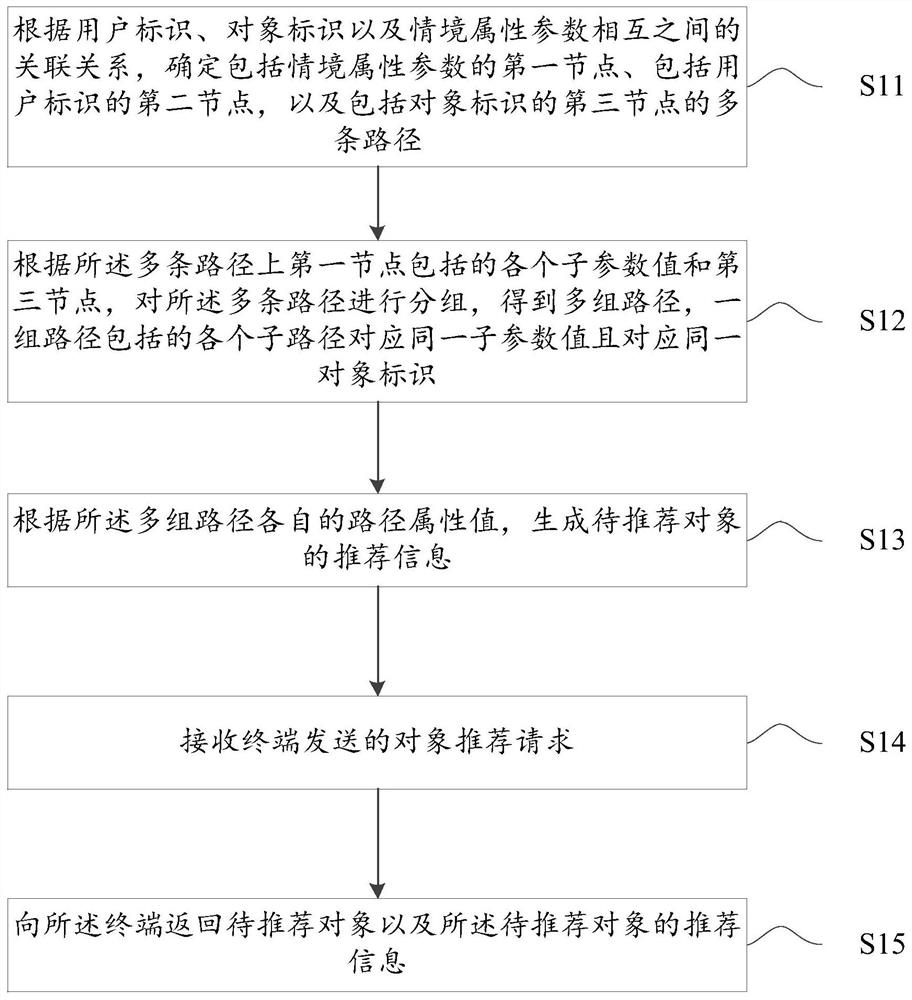
The embodiment of the invention provides a recommendation information generation method and device, electronic equipment and a readable storage medium. The method comprises the following steps: according to an association relationship among user identifiers, object identifiers and situation attribute parameters, obtaining user identifiers; determining a first node comprising a context attribute parameter and a second node comprising a user identifier, and a plurality of paths including a third node of the object identification, according to each sub-parameter value included in the first node on the plurality of paths and a third node, grouping the plurality of paths; obtaining multiple sets of paths, according to the respective path attribute values of the multiple groups of paths; generating recommendation information of the to-be-recommended object, by adoption of the method provided by the embodiment of the invention, the process of generating the to-be-recommended information is combined with the situation attribute parameters and the path attribute values in the historical data of the field to which the recommendation information belongs, so that the recommendation informationfor the to-be-recommended object is richer and has reference, and more surprise and attraction can be brought to the user.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
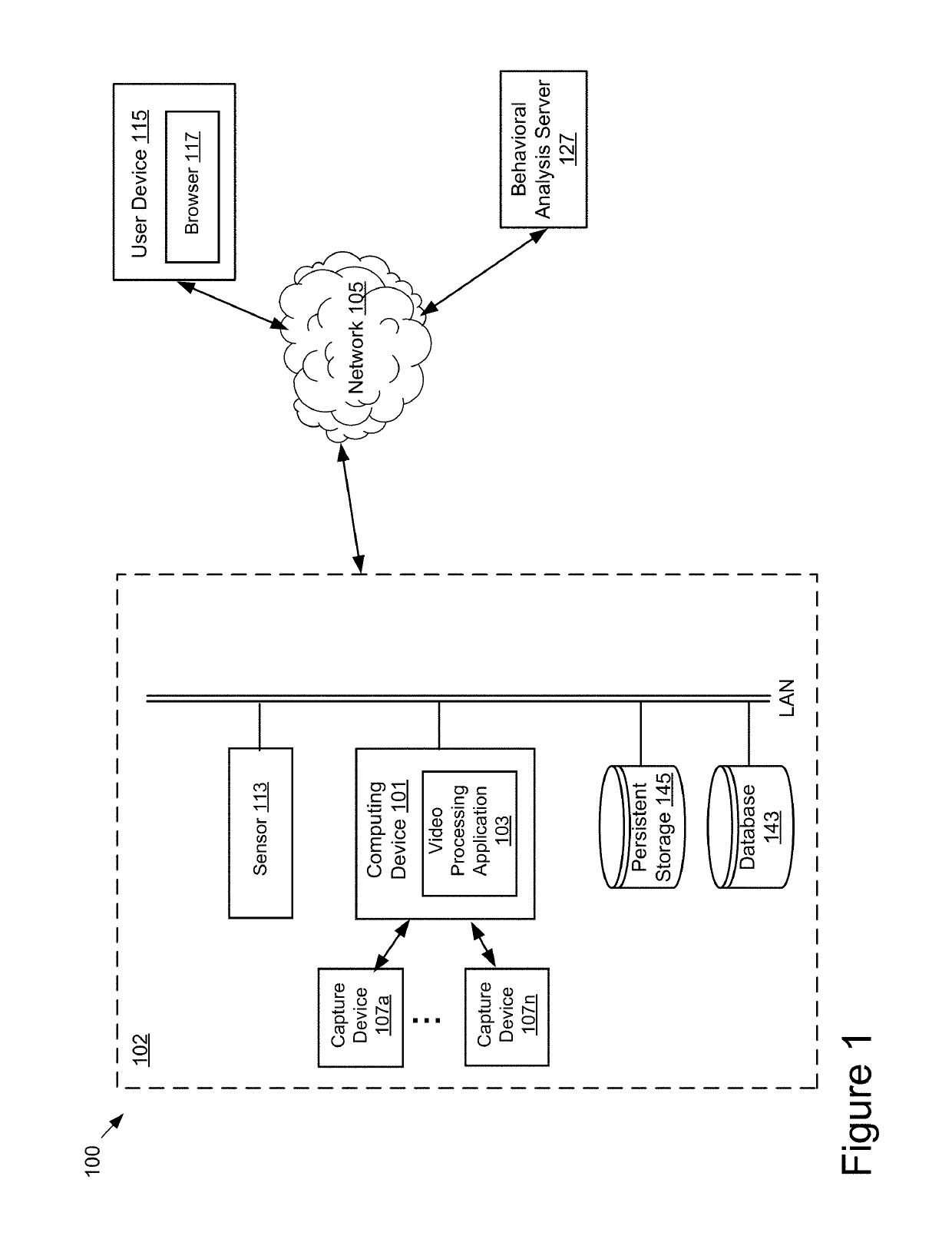
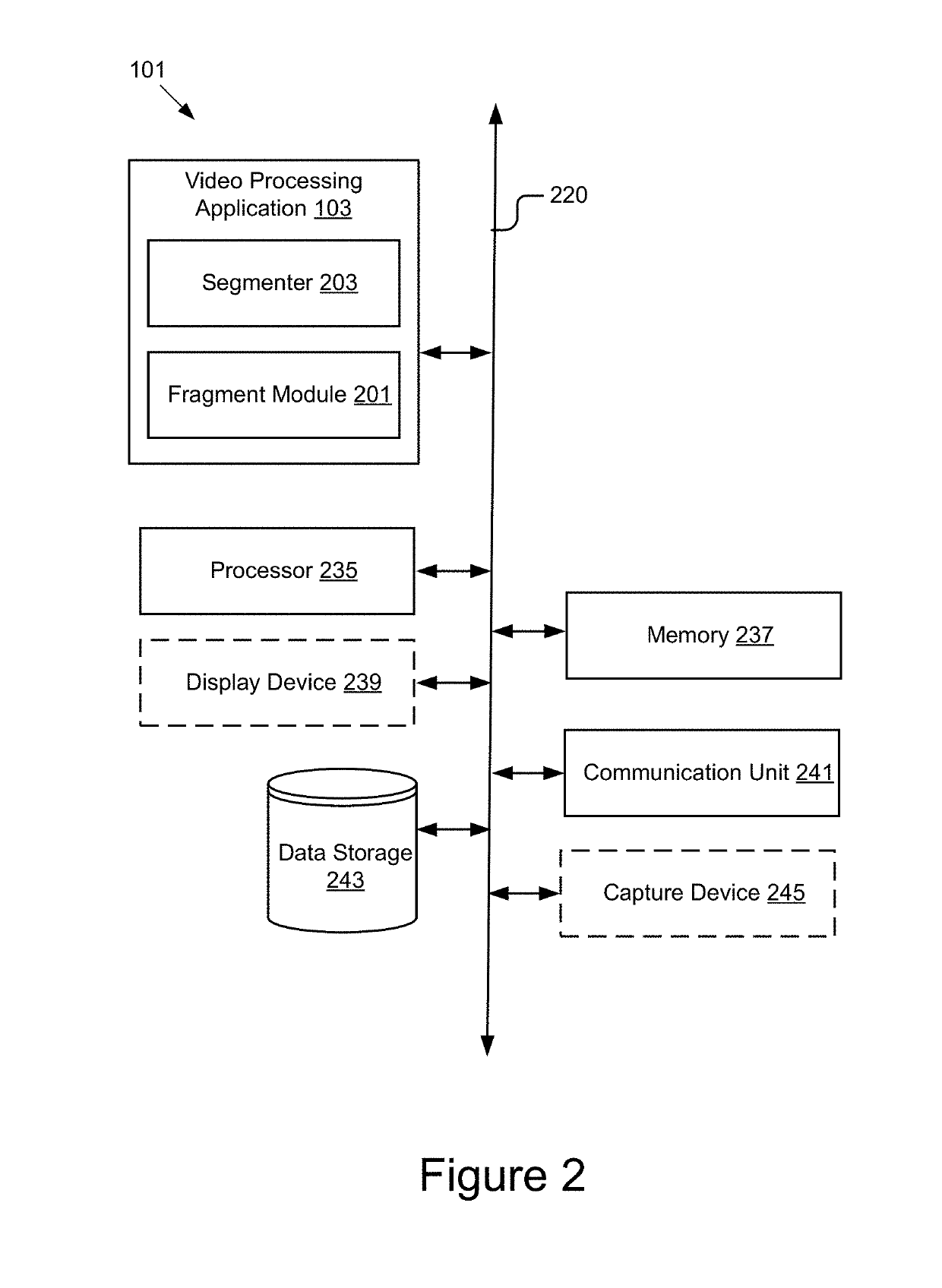
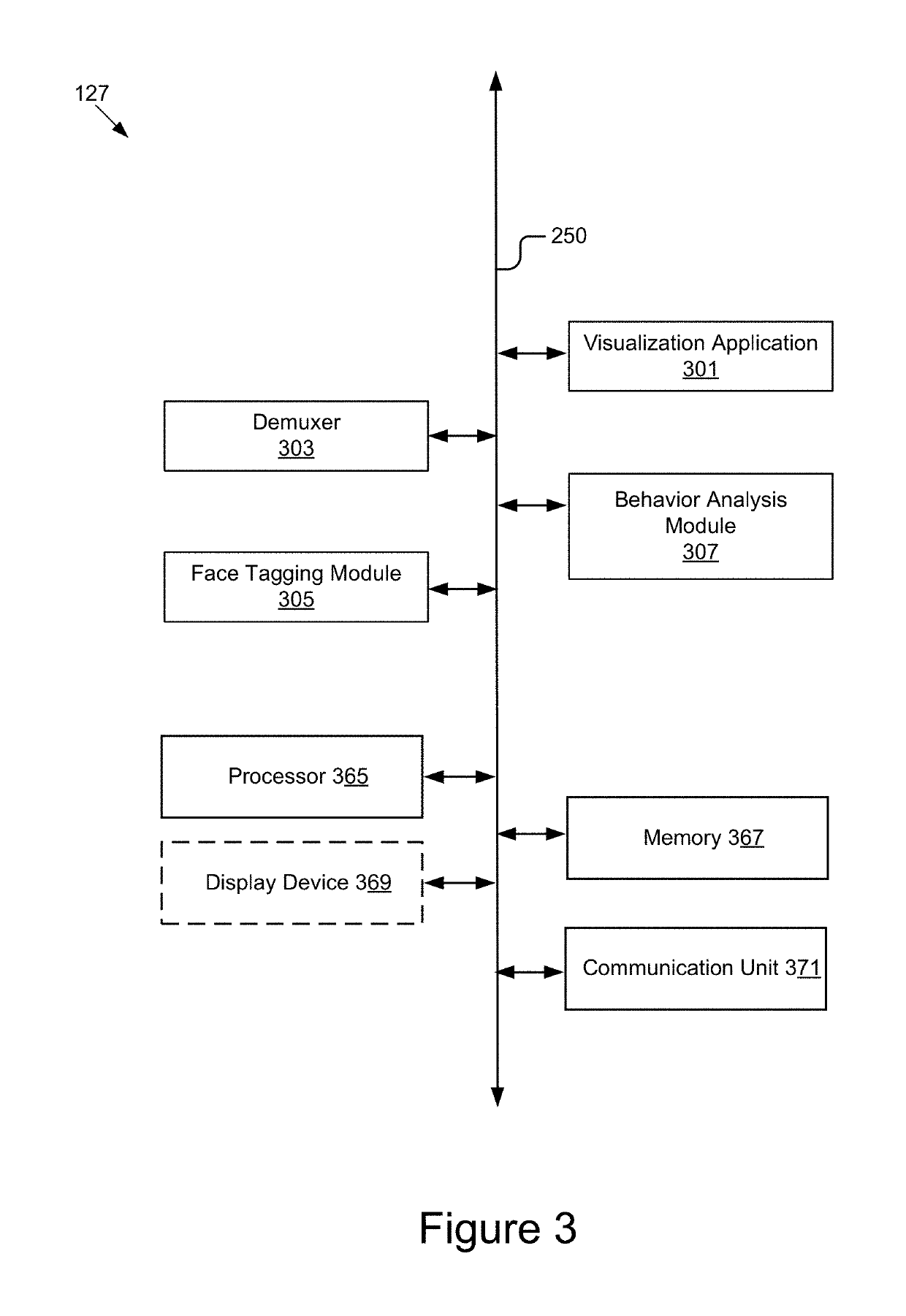
Focalized Behavioral Measurements in a Video Stream
ActiveUS20190244052A1Overcome limitationsImage analysisCharacter and pattern recognitionPattern recognitionUser device
Owner:RICOH KK
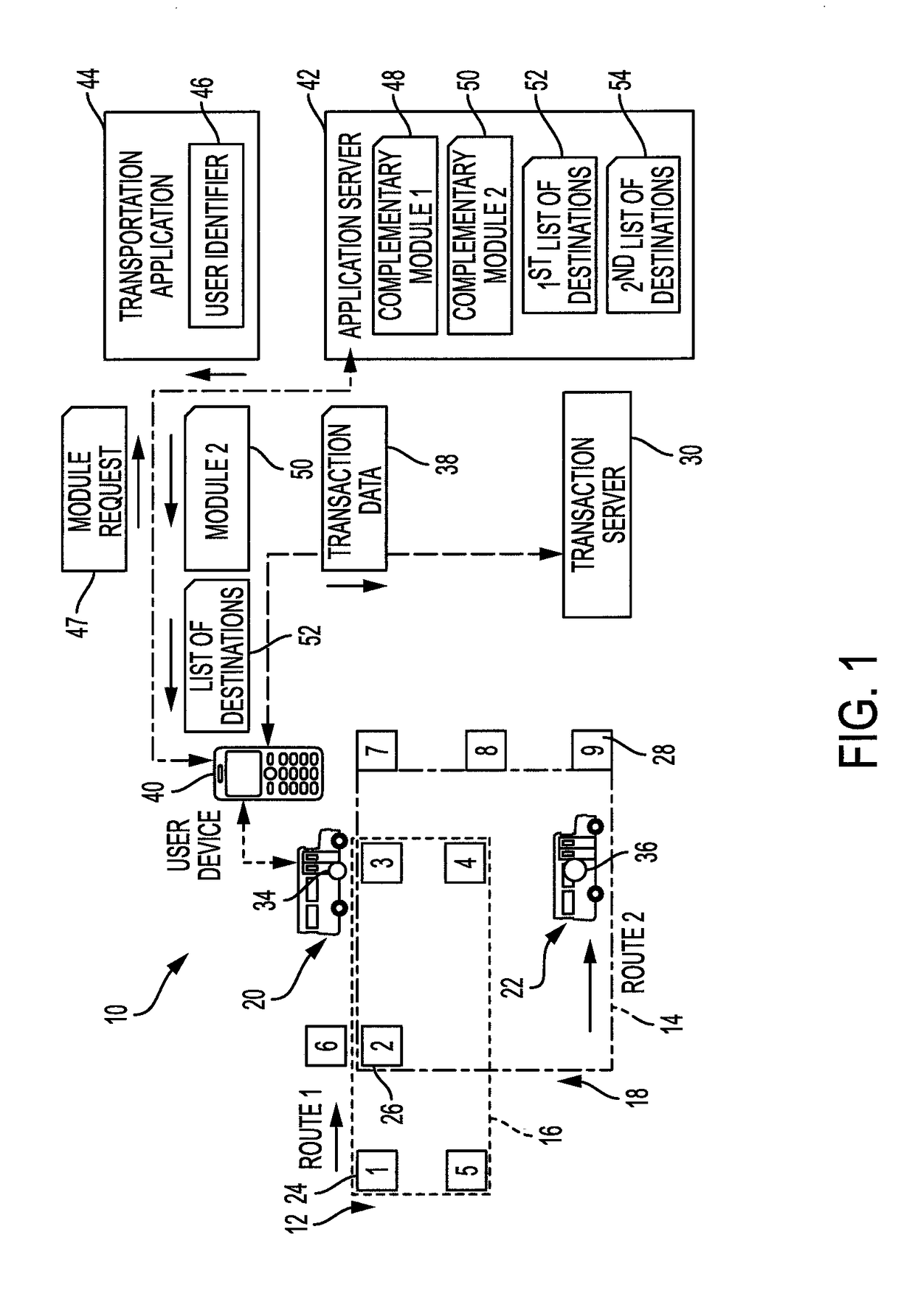
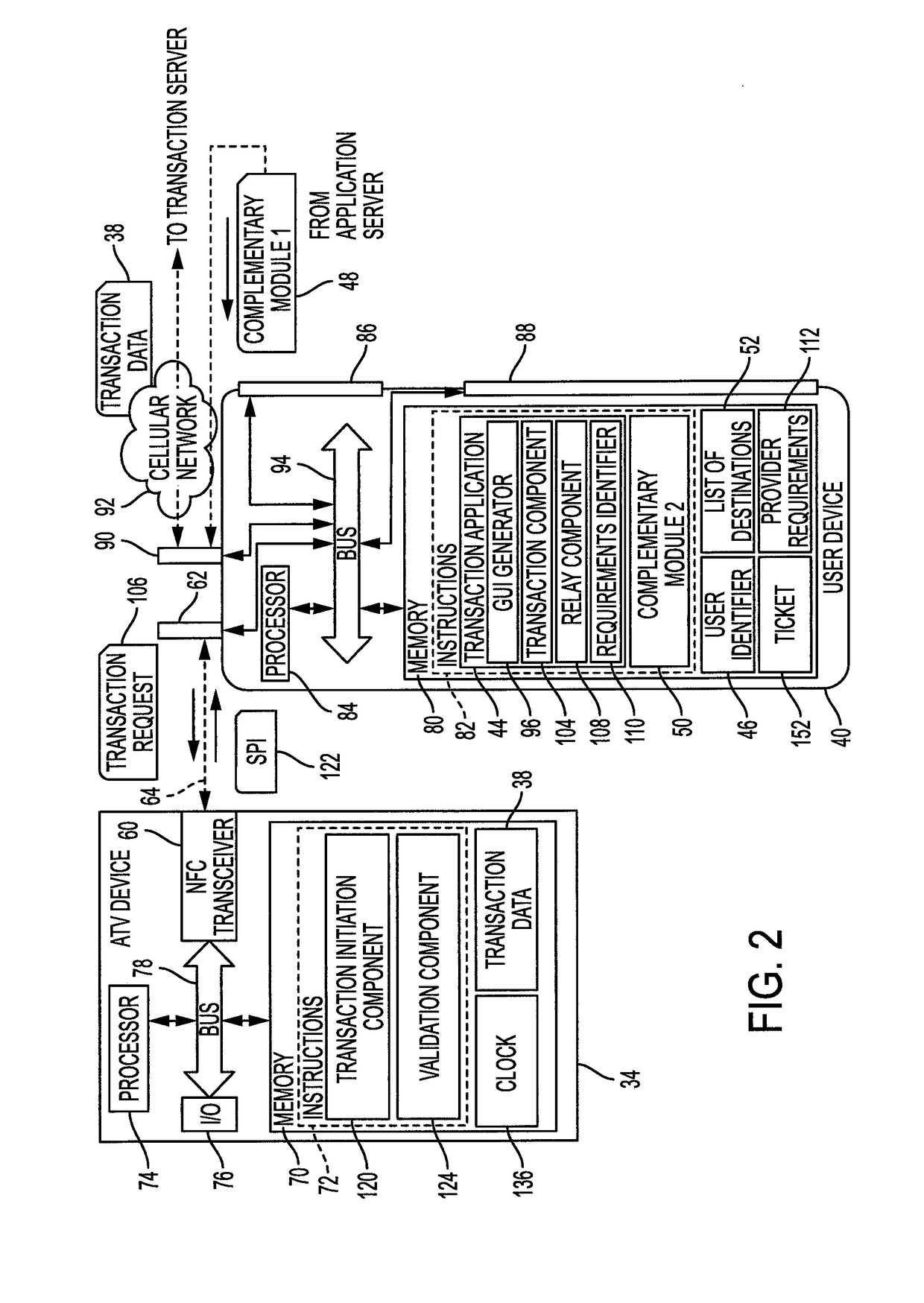
System and method for specializing transactions according to the service provider
A method for enabling transactions on networks that deliver services to users includes communicating a transaction application and a respective user identifier to a mobile communication device via a wireless connection. A set of complementary modules is stored, remote from the mobile communication device. When one of the complementary module has been loaded on the user's mobile communication device, it enables the user of the device to specialize a transaction on at least one of the associated networks by selecting at least one variable of the transaction. Different complementary modules can be provided to the user's mobile communication device for specializing transactions on other service provider networks.
Owner:CONDUENT BUSINESS SERVICES LLC
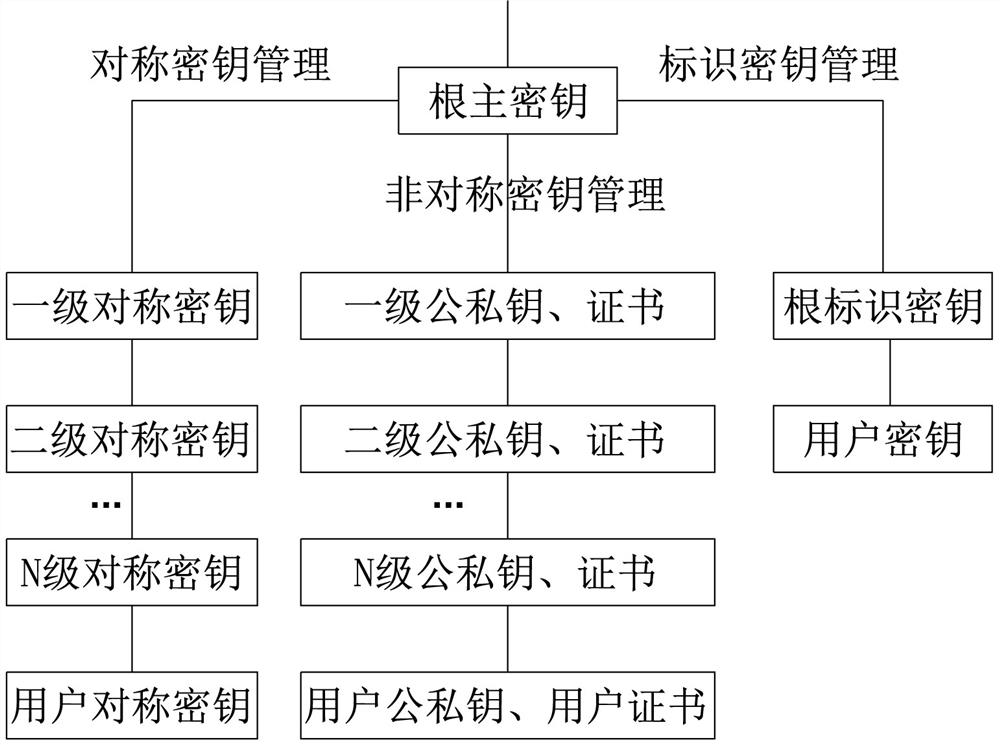
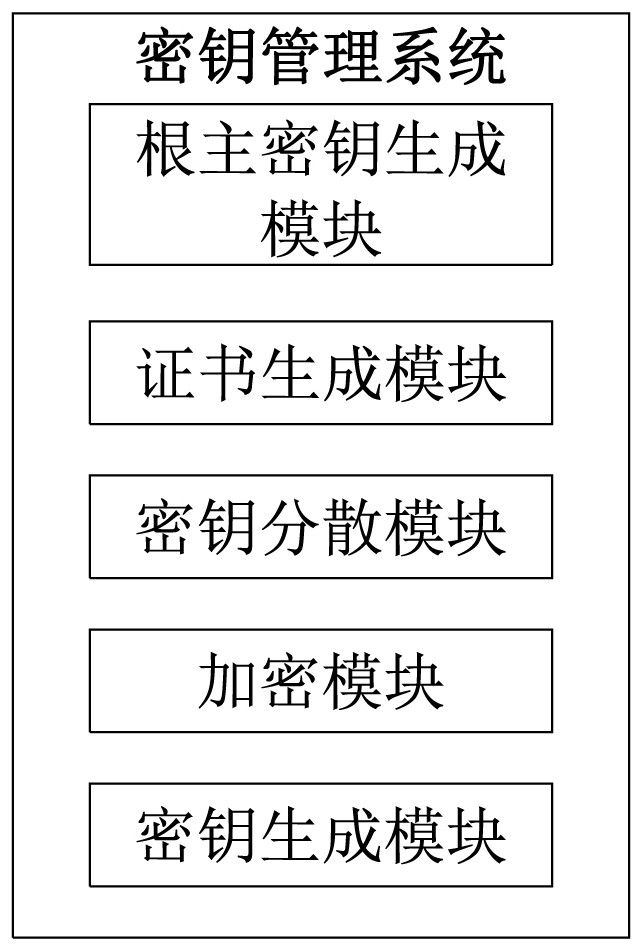
Key management method and system supporting multiple key systems
ActiveCN112054901AEnsure safetyPrevent theftKey distribution for secure communicationPasswordEngineering
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
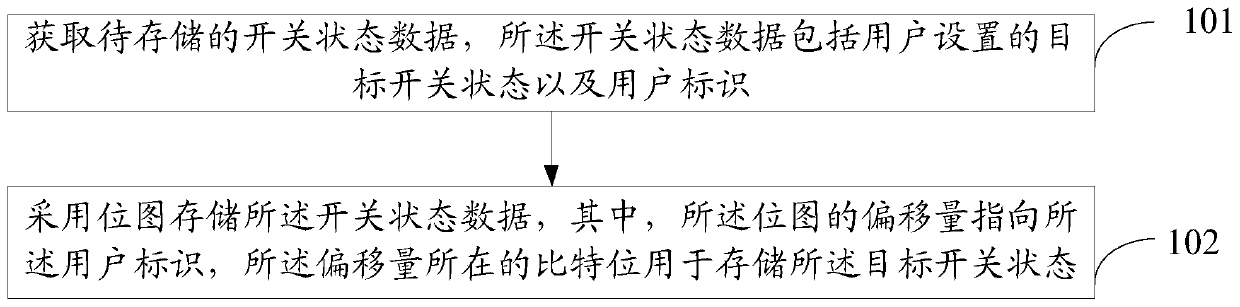
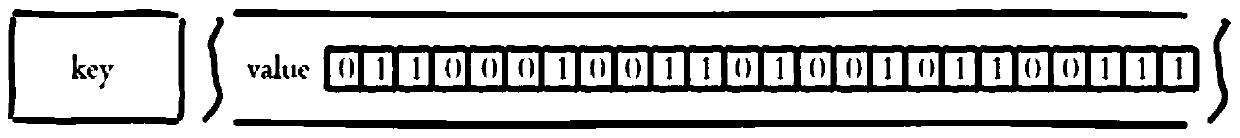
Status data storage method and device and data sending method and device
InactiveCN109977117ASave storage spaceSave storage space effectDatabase design/maintainanceDatabase indexingComputer hardwareUser identifier
Owner:GUANGZHOU HUYA INFORMATION TECH CO LTD
Camera system
InactiveCN1741580ATelevision system detailsColor television detailsComputer graphics (images)Terminal equipment
Owner:KOKUSA ELECTRIC CO LTD
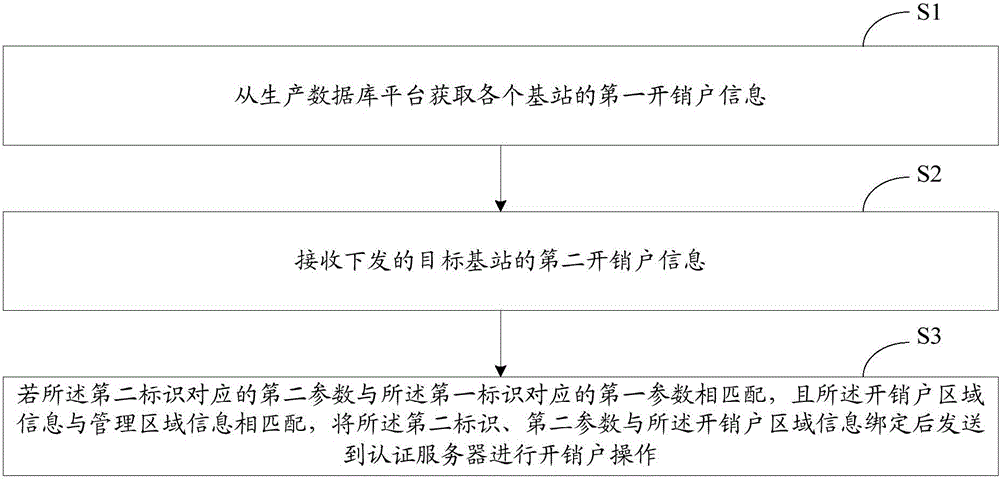
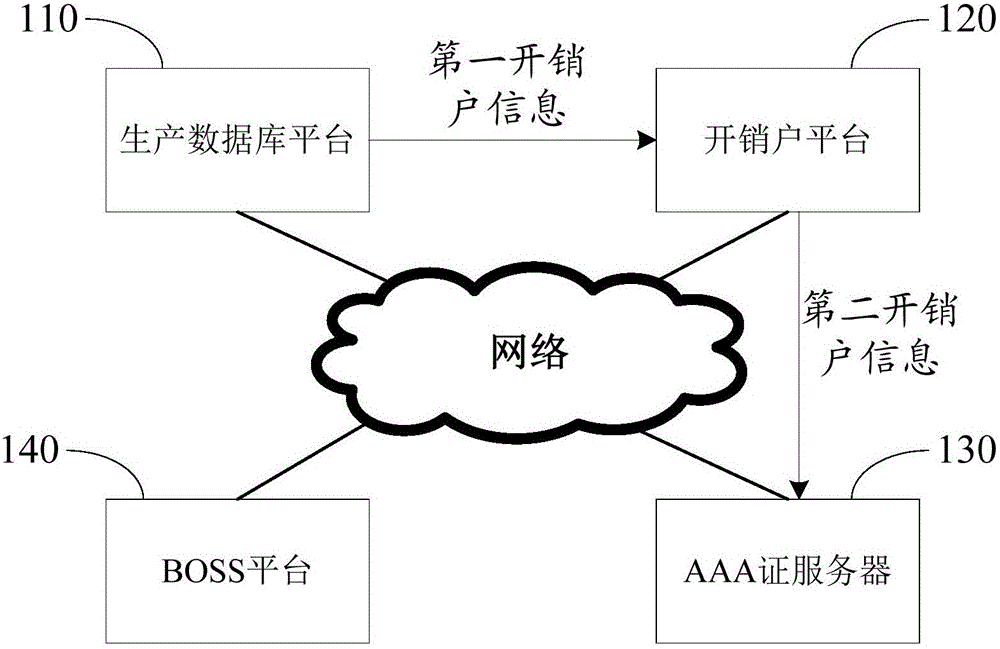
Base station account opening/closing method and system
Owner:COMBA TELECOM SYST CHINA LTD
Member level configuration method and device, computer equipment and readable storage medium
Owner:GUANGZHOU HUADUO NETWORK TECH
Media Storage System
InactiveUS20090064210A1Digital data processing detailsFilamentary/web record carriersRelevant informationRemote control
A media storage system includes a disc input element for receiving a media disc, a disc output element for ejecting a disc, and a media reader for reading information from a disc. If insufficient information is readable from a disc, it may be obtained through a computer network. The system includes a disc transporter for moving received discs to respective internal storage locations. The system includes a data input device for entering disc catalogue data and a data output device such as a display for displaying disc catalogue data. The data input and output devices may be input buttons and a display on a remote control. Each disc and related information is associated with an identifier such that access to disc data may be by restricted by user identifier or content ratings.
Owner:SHYAM CONSULTANTS
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Try Eureka
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap